Managing Unix groups with MMC
You can access Active Directory Users and Computers (ADUC) from the Control Center. Navigate to the Tools | Safeguard Authentication Services Extensions for Active Directory Users and Computers.
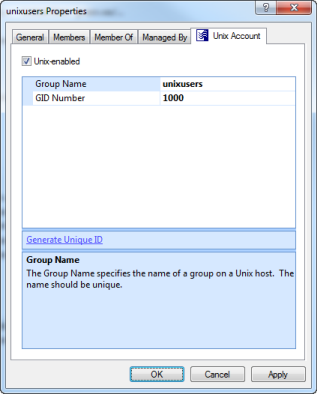
After installing Safeguard Authentication Services on Windows, a Unix Account tab appears in the Active Directory group's Properties dialog.
Note: If the Unix Account tab does not appear in the Group Properties dialog, review the installation steps outlined in the Safeguard Authentication Services Installation Guide to ensure that Safeguard Authentication Services was installed correctly or refer to the Unix Account tab is missing in ADUC for more information.
The Unix Account tab contains the following information:
- Unix-enabled: Check this box to Unix-enable the group. Unix-enabled groups appear as standard Unix groups on Unix hosts. Checking this box causes Safeguard Authentication Services to generate a default value for the GID number attribute. You can alter the way default values are generated from the Control Center.
- Group Name: This is the Unix name of the Windows group.
- GID Number: Use this field to set the numeric Unix Group ID (GID). This value identifies the group on the Unix host. This value must be unique in the forest.
- Generate Unique ID: Click this link to generate a unique GID Number. If the GID Number is already unique, the GID Number is not modified.
Managing groups from the Unix command line
Using the vastool command you can create and delete groups as well as list group information from the Unix command line.
To create a group, use the vastool create command. The following command creates the sales group in Active Directory that is not Unix-enabled:
vastool create -g sales
To create a group that is Unix-enabled, pass in a string formatted like a line from /etc/group as an argument to the -i option, as follows:
vastool create -i "sales:x:1003:" -g sales
By default, all groups created with vastool create are created in the Users container. To create a group in a different organizational unit, use the -c command line option. The following command creates a Unix-enabled group, sales, in the OU=sales,DC=example,DC=com organisational unit:
vastool create -i "sales:x:1003" -c "OU=sales,DC=example,DC=com" -g sales
To delete a group, use vastool delete with the -g option. The following command deletes the sales group:
vastool delete -g sales
To list groups, use vastool list groups. The following command lists all the groups with Unix accounts enabled:
vastool list groups
This command produces output similar to the following:
eng:VAS:1001:pspencer,djones@example.com it:VAS:1002:molsen sales:VAS:1003:bsmith
Managing groups with Windows PowerShell
Using Windows PowerShell you can Unix-enable, Unix-disable, modify, report on, and clear Unix attributes of Active Directory groups using the Safeguard Authentication Services PowerShell commands.
Note: You can access the Safeguard Authentication Services PowerShell commands from Tools in the Control Center. To add Safeguard Authentication Services cmdlets to an existing PowerShell session run Import-Module Quest.AuthenticationServices. See PowerShell cmdlets for a complete list of available commands.
To Unix-enable a group, use the Enable-QasUnixGroup command. The following command Unix-enables the Active Directory group named UNIXusers:
Enable-QasUnixGroup -Identity <domain>\UNIXusers
To disable a group for Unix use the Disable-QasUnixGroup command:
Disable-QasUnixGroup -Identity <domain>\UNIXusers
To report on a group, use the Get-QASUnixGroup <groupname> command. The following commands shows all groups that start with "sa":
Get-QasUnixGroup -Identity sa
The Safeguard Authentication Services PowerShell commands are designed to work with the Active Directory commands from Microsoft (Get-ADGroup) and One Identity (Get-QADGroup). You can pipe the output of these commands to any of the Safeguard Authentication Services PowerShell commands that operate on groups. For example, the following command clears the Unix attributes from the group UNIXusers:
Get-QADGroup -Identity <domain>\UNIXusers | Clear-QasUnixGroup
The Safeguard Authentication Services PowerShell commands are aware of the options and schema settings configured in Control Center. Scripts written using the Safeguard Authentication Services PowerShell commands work without modification in any Safeguard Authentication Services environment.
Overriding Unix group information
You can override group account attributes on the local Unix host. This allows you to use the group information from Active Directory but modify individual attributes on certain hosts as needed. Group overrides are specified in the /etc/opt/quest/vas/group-override configuration file. Overrides are specified as follows:
DOMAIN\sAMAccountName:<Group Name>:<GID Number>:<Group Membership>
DOMAIN\sAMAccountName must refer to a valid Active Directory group account. You can omit any of the Unix account fields. If a field is not specified, it will get the default value for that group. The group membership field consists of a comma-separated list of Active Directory user accounts specified in DOMAIN\sAMAccountName format. For examples, refer to the /etc/opt/quest/vas/group-override.sample file.
You can manage group overrides using Group Policy. For more information, see Account Override policies.
