About this guide
The One Identity Manager On Demand Quick Start Guide provides an overview of the architecture of our One Identity Manager offering and its core capabilities. It also provides information about the customization limitations and prerequisites you will need before installing the on-premises component, and how to set up, install, and update One Identity Manager on-premises components.One Identity Manager
This guide is intended for system administrators, consultants, and any other IAM professionals using the product.
Available documentation
You can access One Identity Manager documentation in the Manager and in the Designer by selecting the Help > Search menu item. The online version of One Identity Manager documentation is available in the Support portal under Technical Documentation. You will find videos with additional information at www.YouTube.com/OneIdentity.
One Identity Manager overview
One Identity Manager is a cloud service offering from One Identity that provides a fully-functional implementation of the One Identity Manager application, deployed to customers over the cloud (https://cloud.oneidentity.com) and supported by the One Identity operations team.
One Identity Manager simplifies the process of managing user identities, access permissions, and security policies. You allow the company control over identity management and access approvals while the IT team focuses on their core competencies.
With this product, you can tackle all Identity Governance and Administration core functions:
-
Identity life cycle: Maintaining digital identities, their relationships with the organization, and their attributes during the entire process from creation to eventual archiving, using one or more identity life cycle patterns.
-
Entitlement management: Maintaining the link between identities and access permissions to be able to tell who has access to what and who is responsible for maintaining an account or access permissions. This includes maintaining and curating the entitlements catalog to describe the types of accounts, roles, group memberships, and other entitlements.
-
Access requests: Enabling users, or others acting on behalf of a user, to request access permissions through a business-friendly user interface.
-
Workflow: Orchestrating tasks to enable functions such as access approvals, notifications, escalations, manual fulfillment requests, and integration with other business processes. For example, this allows managers or resource owners to approve or deny requests.
-
Policy and role management: Maintaining rules that govern automatic assignment (and removal) of access permissions; providing visibility of access permissions for selection in access requests, approval processes, dependencies, and incompatibilities between access permissions; and so on. Roles are a common vehicle for policy management.
-
Access certification: Requiring people like managers and resource owners to review and certify the access permissions that users have on a periodic basis to ensure access continues to comply with policies.
-
Fulfillment: Propagating changes initiated by One Identity Manager to target systems. Automatic fulfillment (often called "provisioning") connects with user account target systems, while manual fulfillment utilizes a workflow or external process to complete actions.
-
Auditing: Evaluating business rules and controls against the identities' current state and access permissions, providing a means for alerting control owners of exceptions (such as changes made directly on target systems), and allowing for orderly remediation.
-
Identity analytics and reporting: Providing means to: (a) evaluate risk based on identity information insights; (b) apply techniques to cleanup excessive, outlier, or wrongful entitlements; and (c) enhance the continuous process of identity governance, including risk reporting.
Every one of these core functions is based on an automation-optimized architecture that addresses major Identity Governance and Administration challenges at a fraction of the complexity and time of "traditional" solutions.
Architecture overview
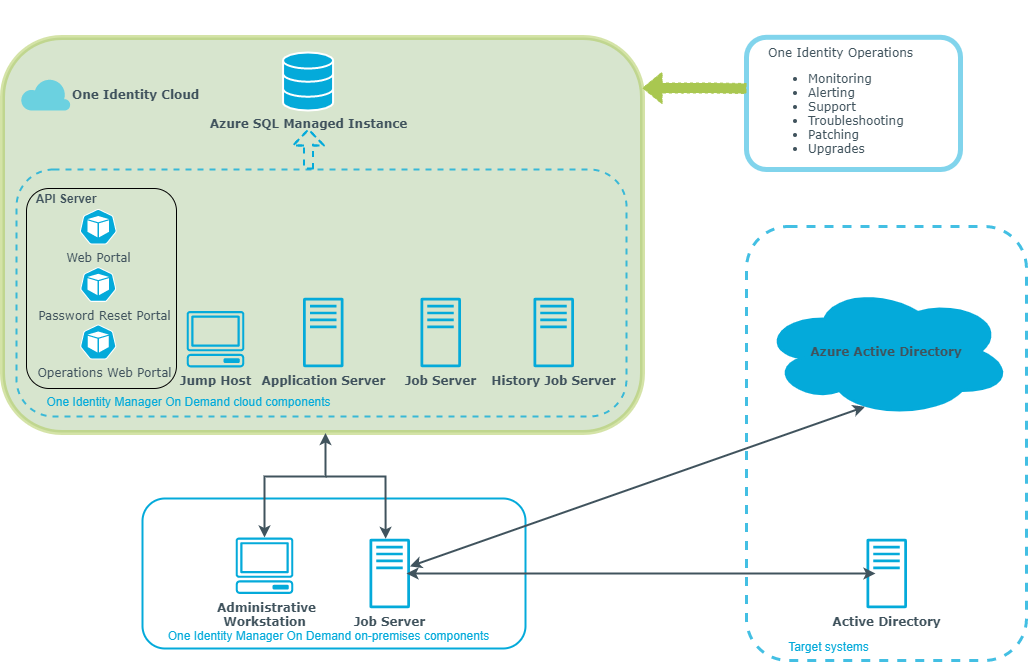
The architecture overview shows the different components of One Identity Manager. One Identity Manager cloud components are managed and monitored by the One Identity operations team. One Identity Manager on-premises components must be installed and configured locally to connect and synchronize on-premises target systems with One Identity Manager cloud components.
Figure 1: Overview of One Identity Manager components
Using One Identity Manager as a Starling service
One Identity Manager is integrated as a Starling service in One Identity Starling (https://cloud.oneidentity.com). One Identity Manager is available as a time-limited trial version and as a paid subscription.
For the One Identity operations team to deploy One Identity Manager, you must first provide One Identity with your configuration data. To do this, use the One Identity Starling portal.
Prerequisites
-
To use One Identity Manager as a Starling service, you require a Starling organization. You can add the Starling service to an existing organization or set up a new one. For more information about organizations, see the One Identity Starling User Guide.
-
To use One Identity Manager for limited period of time, contact One Identity. They can activate a product trial for your organization. One Identity notifies you once the product trial has been added to your organization's account.
-
To configure a subscribed product, you will receive confirmation of your subscription by email from One Identity.
To submit the configuration information to the One Identity operations team
-
Log in to the One Identity Starling portal.
-
Configure your subscription.
-
To configure a product trial, on the Home page, select the View On Demand Services section.
-
Select One Identity Manager On Demand and click Trial.
This creates a trial subscription. One Identity Manager On Demand is shown as a new tile in the My Services section and can be used until trial period ends.
-
On the home page, in the My Services section, click the One Identity Manager On Demand tile.
-
To configure a paid product, click on the One Identity Manager On Demand tile in the My Services section on the home page.
-
In the Contact Information step, you enter details of a technical contact that the One Identity operations team can get in touch with.
-
If you are the technical contact, select I am the technical contact.
-
If you want to specify another contact, select Someone else is the technical contact and invite the contact using the Invite Collaborator.
TIP: You can also invite collaborators on the Collaborators tab.
-
Click Next: Technical Information.
-
In the Technical Information step, enter the information required for your One Identity Manager configuration.
-
To submit the configuration to the One Identity operations team, click Submit Details and confirm the prompt.
-
After configuration is complete, the Setting up step provides information about deployment status. You will be notified by mail when the status changes.
NOTE: If the custom configuration is rejected by the One Identity operations team, you can update the configuration data with Update Details and resubmit.
After successful deployment, the Application tab displays the connection details of your One Identity Manager deployment. You need this information for accessing the One Identity Manager cloud components.

