-
Title
How do you provide the UNIX password hash to legacy systems using vasyp? -
Description
Some legacy systems require the UNIX password hash to be available via NIS. These systems use a crypt and compare authentication method.
-
Resolution
This setup is outside the scope of Technical Support as it is configuring NIS and Microsoft Windows Servers. Also providing password hashes by implemented these instructions is not considered secure. One Identity Software does not recommend this option, but it is available for when its need outweighs the security concerns.
Note: This solution involves changing a registry setting and rebooting all Active Directory Domain controllers.
Active Directory changes
1. Configure AD to store the password hash
Install the Identity Management for UNIX role on the AD server.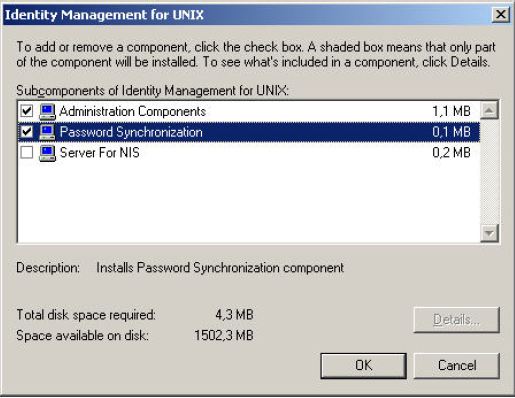
Select Password Synchronization
Click on OK2. Modify the following registry setting using regedit:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PswdSync\SNISPasswordSyncEnable
Change the value to "1"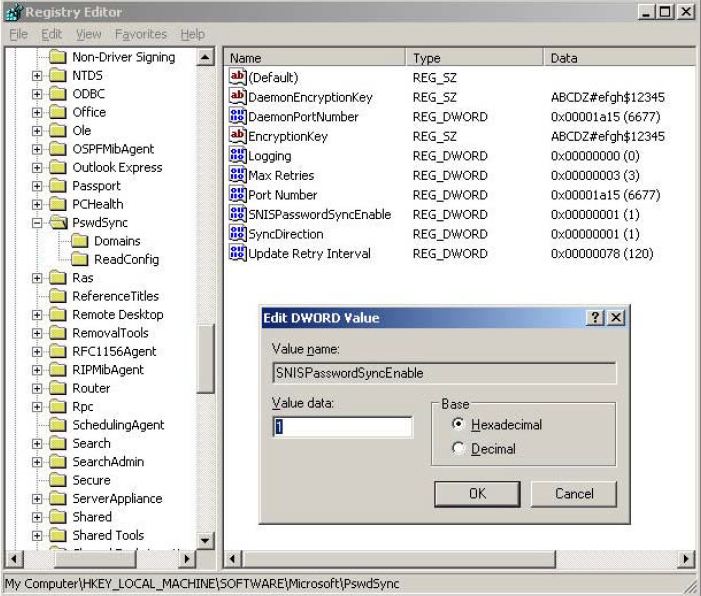
3. Restart the Domain Controller.
Now execute all of the above steps on all Domain Controllers or password change requests processed by other domain controllers will not update the password hash stored in the "UnixUserPassword" hash attribute.
4. Set the mssfu30nisdomain value for each user that requires the password hash to be synchronized.
This value can be set by running the following vastool command on any UNIX host:
vastool -u <admin> setattrs <username> mssfu30nisdomain <domainname>
e.g vastool -u administrator setattrs mbtest10 mssfu30nisdomain bly.com
Note that the hash value will not be populated until the user's password is changed for the first time after synchronization is configured
Changes on the UNIX host
1. Install vasypd as per instructions in the Quest Authentication Services administration guide (Installing and Configuring the QAS NIS Components)
2. Run the following vastool commands to enable password hash via vasypd:
vastool configure vas vasd cache-unix-password true
vastool configure vas vasypd provide-password-hash trueLogin as the user and reset the password
The user will now have a value against the unixUserPassword attribute in Active Directory.
For Example: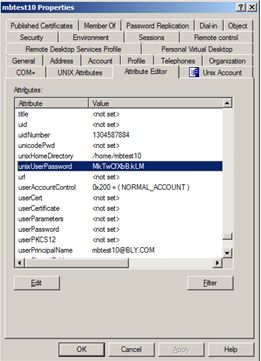
Test that the attribute is available on the UNIX server by running the following command:
ypcat passwd
The output should show the hash after the user name, for example:
mbtest10:MkTwCfXbB.kLM:1304587884:1000::/home/mbtest10:/bin/shNIS Disclaimer:
One Identity does not recommend using NIS as it is not secure.
Windows Registry Disclaimer:
One Identity does not provide support for problems that arise from improper modification of the registry. The Windows registry contains information critical to your computer and applications. Make sure you back up the registry before modifying it. For more information on the Windows Registry Editor and how to back up and restore it, refer to Microsoft Article ID 256986 "Description of the Microsoft Windows registry" at Microsoft Support
