A great tool to use frequently when creating and troubleshooting Privilege Authority Rules is Process Explorer, one of the suite of tools from SysInternal. It can be downloaded
here.
In this example, users are allowed to make changes in Device Manager.
The environment is a Windows 7 workstation logged in as a user with restricted rights.
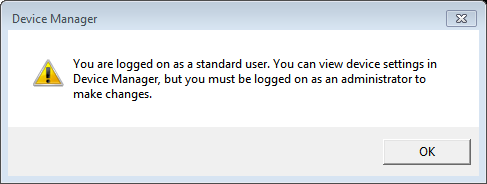
If going to Control Panel | Hardware and Sounds, and then select Device Manager, the message below is displayed:
When running Process Explorer it displays a list of processes running on the local machine. Scrolling down to the bottom of the page you will find the process mmc.exe (Microsoft Management Console). If unsure what the process you are wanting to investigate is called, change the view options via View | Select Columns and select the "Windows Title" column. Then, look for Device Manager.
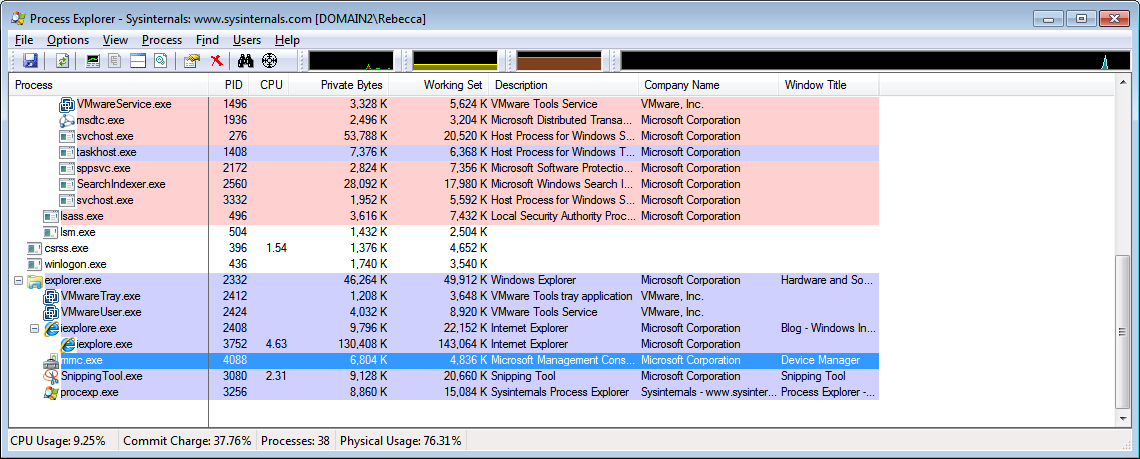
To check what the command line is for the Device Manager MMC snapin, select Properties from the context menu.

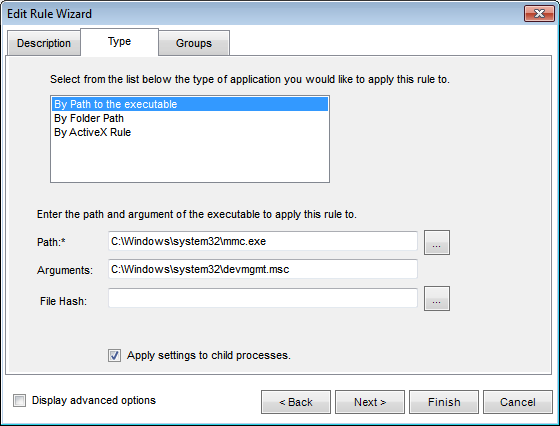
The path to the executable is C:\Windows\system32\mmc.exe and the command line is C:\Windows\system32\devmgmt.msc.
Next, use this information to create a rule for Device Manager in the Privilege Manager console.
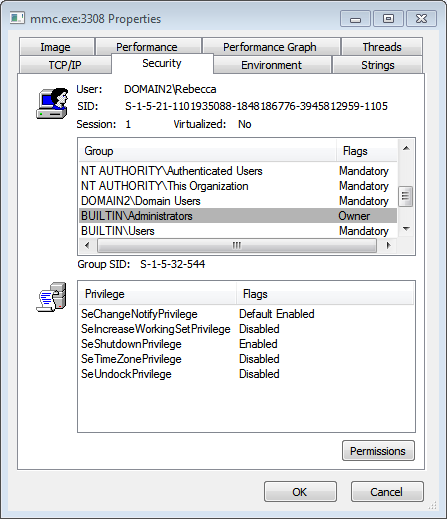
After saving the rule and updating Group Policy the rule is present on the machine. When running Device Manager again, it runs with elevated privileges and I am allowed to make changes.
Check the privileges by selecting the process again in Process Explorer and view the Properties of that process. Under the Security Tab view both the groups on the security token, as well as the privileges. Under groups, see that the BUILTIN\Administrators group was added in this example.
 When running Process Explorer it displays a list of processes running on the local machine. Scrolling down to the bottom of the page you will find the process mmc.exe (Microsoft Management Console). If unsure what the process you are wanting to investigate is called, change the view options via View | Select Columns and select the "Windows Title" column. Then, look for Device Manager.
When running Process Explorer it displays a list of processes running on the local machine. Scrolling down to the bottom of the page you will find the process mmc.exe (Microsoft Management Console). If unsure what the process you are wanting to investigate is called, change the view options via View | Select Columns and select the "Windows Title" column. Then, look for Device Manager. To check what the command line is for the Device Manager MMC snapin, select Properties from the context menu.
To check what the command line is for the Device Manager MMC snapin, select Properties from the context menu.
 After saving the rule and updating Group Policy the rule is present on the machine. When running Device Manager again, it runs with elevated privileges and I am allowed to make changes.Check the privileges by selecting the process again in Process Explorer and view the Properties of that process. Under the Security Tab view both the groups on the security token, as well as the privileges. Under groups, see that the BUILTIN\Administrators group was added in this example.
After saving the rule and updating Group Policy the rule is present on the machine. When running Device Manager again, it runs with elevated privileges and I am allowed to make changes.Check the privileges by selecting the process again in Process Explorer and view the Properties of that process. Under the Security Tab view both the groups on the security token, as well as the privileges. Under groups, see that the BUILTIN\Administrators group was added in this example.
