Key Points:
1. TPAM will use RADIUS set to Primary Authentication.
2. Azure MFA server will perform Active Directory (AD) authentication first and then Azure Multi-Factor Authentication.
3. Tested configurations:
a. SMS One-Way OTP + PIN
b. Phone and PIN
c. SMS Two-Way and PIN
4. Confirmed on versions 2.5.916, 2.5.917 and 2.5.918 (as shown in this article).
TPAM ConfigurationExternal Authentication using RADIUS1. From the /admin interface select
System Status/Settings | External Authentication | RADIUS Config.
2. Click the
New System button and enter the required details for the Azure MFA server, as per the below example:
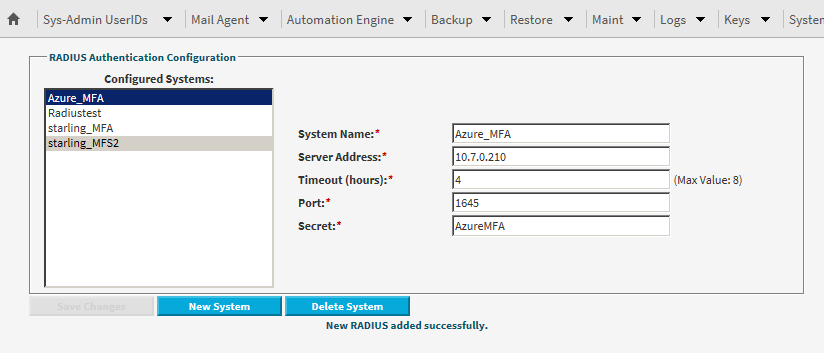
3. Click
Save Changes to save the new system settings.
Please refer to the System Administrator Guide (available
here) for more information on External Authentication with RADIUS.
User Configuration1. From the /tpam interface select
Users & Groups | UserIDs | Manage UserIDs.
2. Select the
Listing tab and select the applicable user from the list.
3. Click the
Details tab and set the Primary authentication to RADIUS, as per the example below:
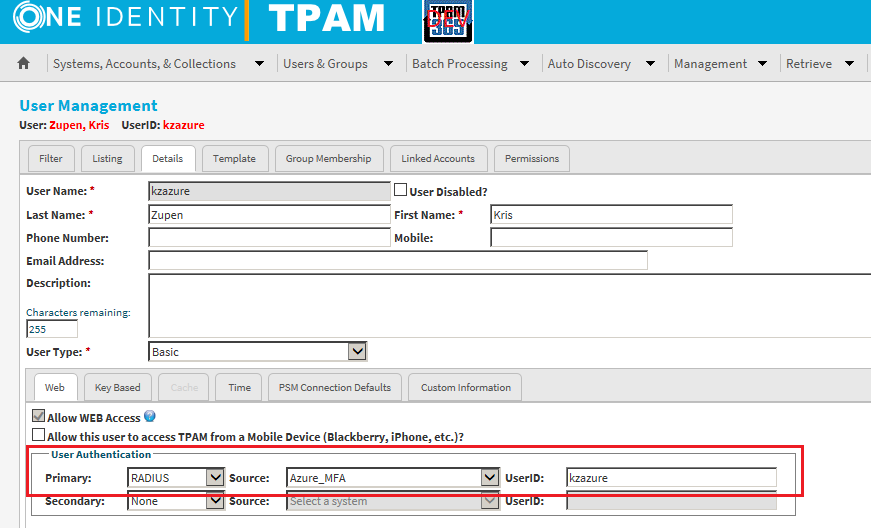
4. Click
Save Changes.
Please refer to the Administration Guide (available
here) for more information on user management.
Azure MFA Configuration
Please refer to the Azure MFA documentation for further information on configuration for RADIUS authentication.
Add a RADIUS client1.
In the Azure Multi-Factor Authentication Server, click the RADIUS Authentication icon in the left menu.
2. Check the
Enable RADIUS authentication checkbox.
3. On the
Clients tab, change the Authentication and Accounting ports if the Azure MFA RADIUS service needs to listen for RADIUS requests on non-standard ports.
4. Click
Add.
5. Enter the IP address of the TPAM appliance that will authenticate to the Azure MFA Server, an application name (optional), and a shared secret (the shared secret must be the same on both the Azure MFA server and in TPAM).
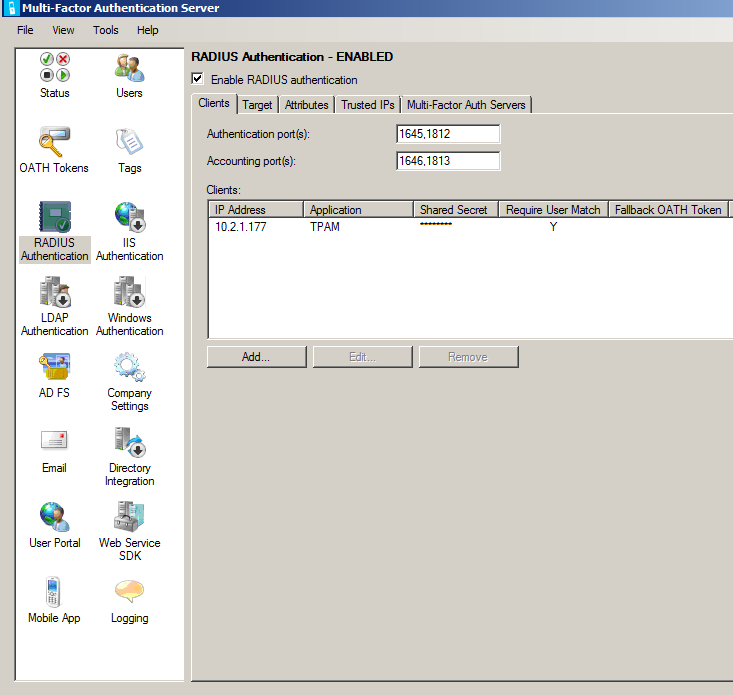
Configure the RADIUS client
1. Click the Target tab.
2. If the Azure MFA Server is installed on a domain member server in an Active Directory environment, select "Windows domain".
3. If users should be authenticated against an LDAP directory, select LDAP bind (The target will normally be a Windows domain, but in this configuration example the Azure MFA server was installed on a device that was not a domain member, which is why LDAP bind was required to reach Active Directory).
 Configure the user for One-Way OTP + PIN
Configure the user for One-Way OTP + PIN 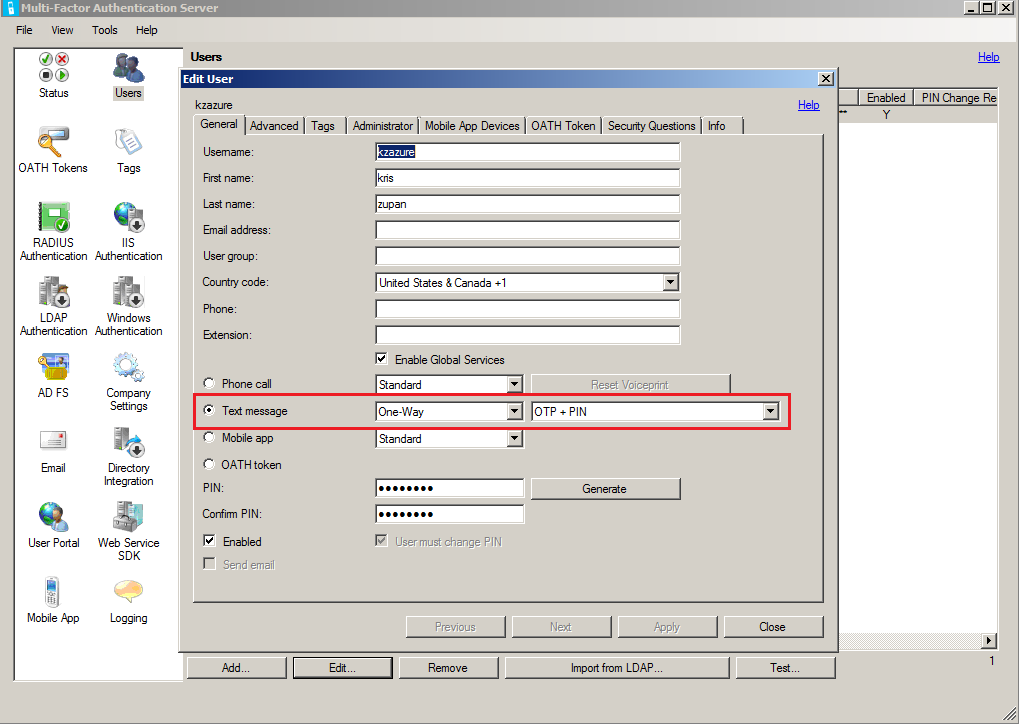
Configure Company Settings Configure Username Resolution
Configure Username ResolutionMost usernames will use SIDs from Active Directory, but as the Azure MFA server is not a domain member in this example, we just do a string match:
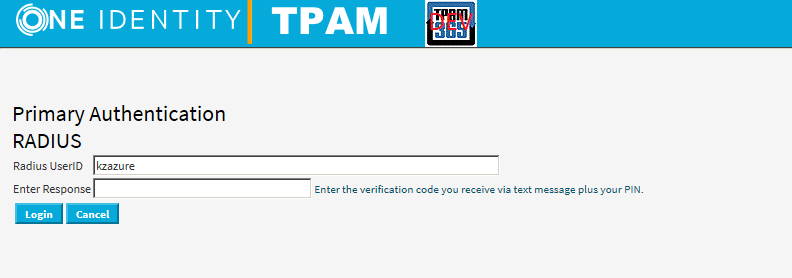
 To test, log in using SMS One-Way and PIN:
To test, log in using SMS One-Way and PIN:
Upon clicking Login you will receive text with code and message, "Use this code for TPAM verification".
Enter the verification code plus PIN in the
Enter Response field then click
Login:
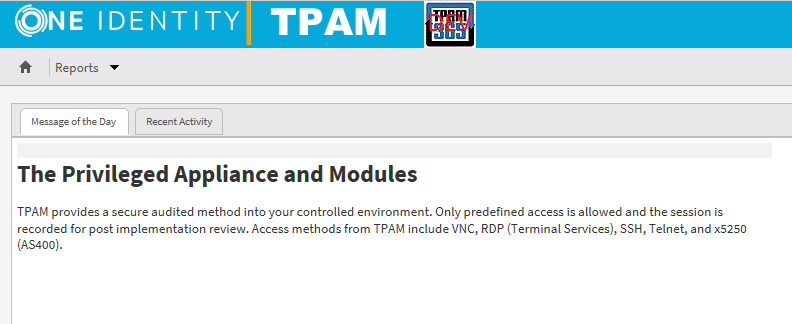
Followed by a successful login:
Test with Phone
Azure MFA Configuration:
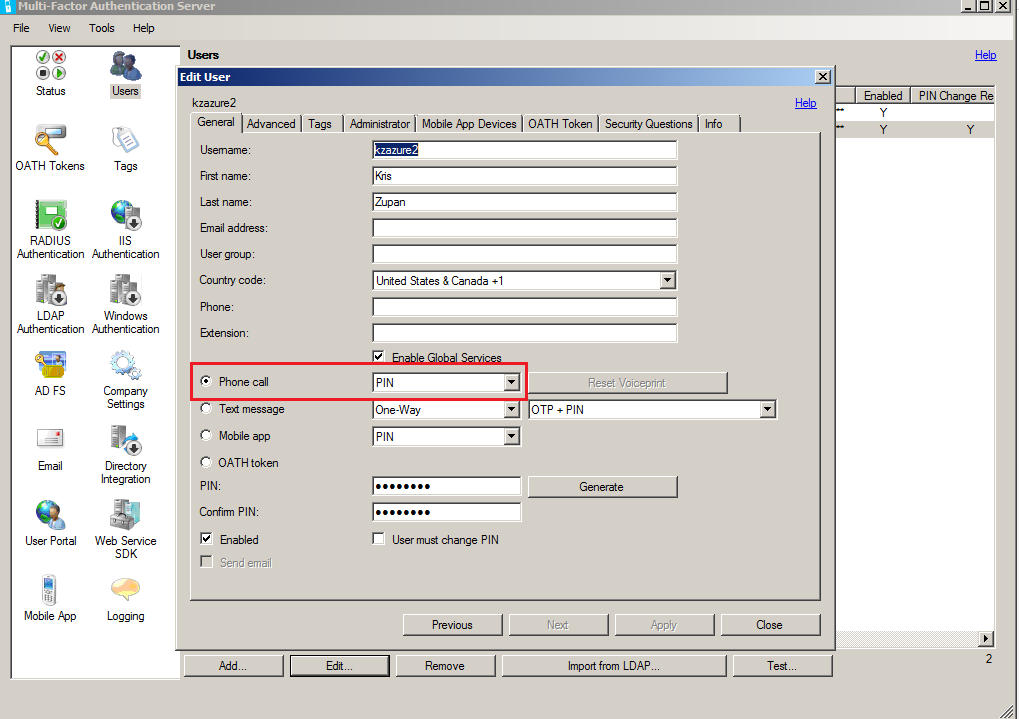
In TPAM the user settings stay the same:
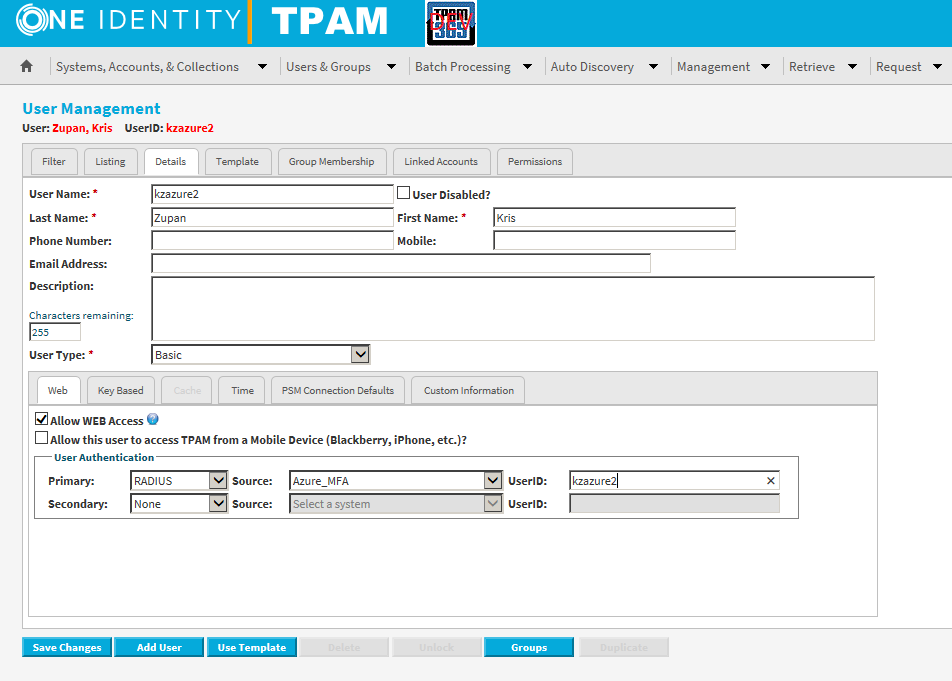
Test:

Call received, required to enter PIN. Login successful:
 Two way SMS & PIN:
Two way SMS & PIN: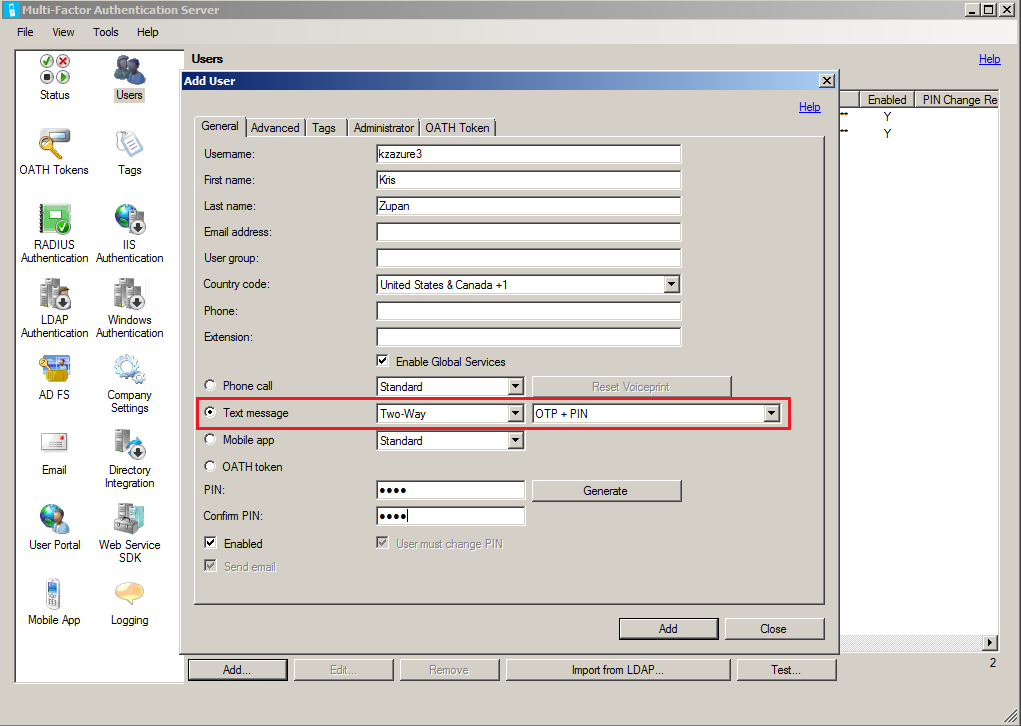
Again, TPAM user settings remain the same:
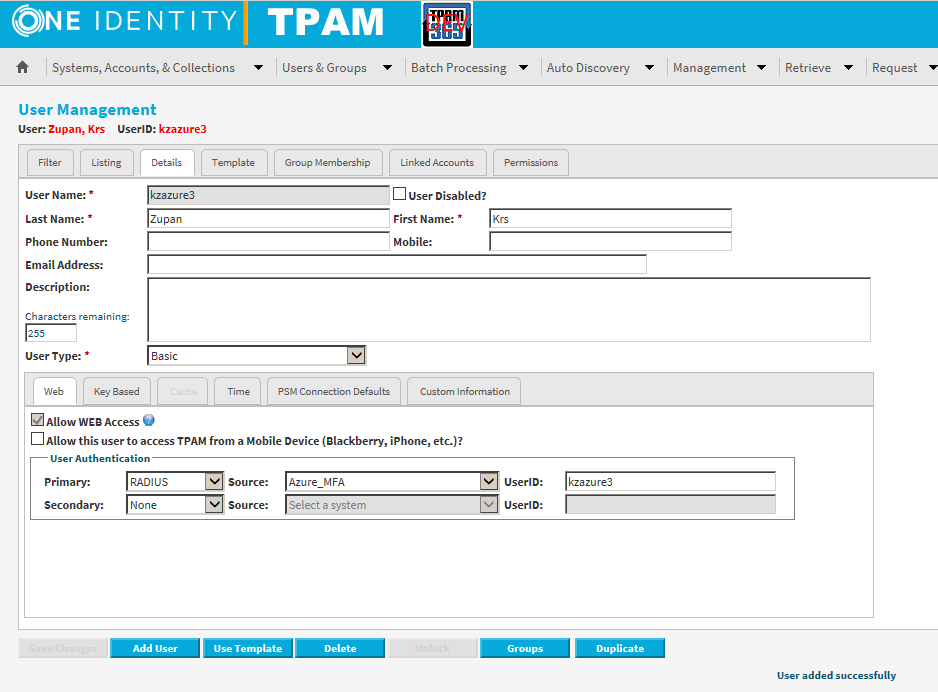
Test again:

Received text that requested verification code and PIN to be texted via reply. Following that, login is successful: