-
Title
Troubleshooting authentication issues with TPAM and RSA SecurID -
Description
If users experience system-wide issues authenticating against RSA SecurID, you can troubleshoot the issue(s) using the following steps: -
Resolution
Confirming the Authentication Agent Address and DNS
- IF DNS is being used verify that the DNS server is pointing to correct IP, otherwise use IP address instead of DNS
Test communication from Net Tools in the /config Interface to RSA server
- Can you Ping the RSA server? (For more information on the "Net Tools" functionality, please refer to the Systems Administrator Guide. A copy of the guide may be downloaded here: TPAM Appliance - Release Notes and Guides.)
- If changes have been made on the RSA SecurID server, it is important to generate and upload a new sdconf.rec file.Confirming the IP Address of RSA SecurID server
- The Agent Host IP Address must match the IP address configured in the sdconf.rec file generated on the RSA server and loaded on the TPAM device.
Ensuring the network path is open between TPAM and RSA SecurID server
- If you are seeing packets leaving the TPAM appliance, you need to confirm that the packets are reaching the RSA SecurID server. Ideally, you want to capture the traffic at the hop closest to the RSA SecurID server or by using a network sniffer if one is available. Ports are listed on RSA . Make sure the Firewall is allowing this traffic through: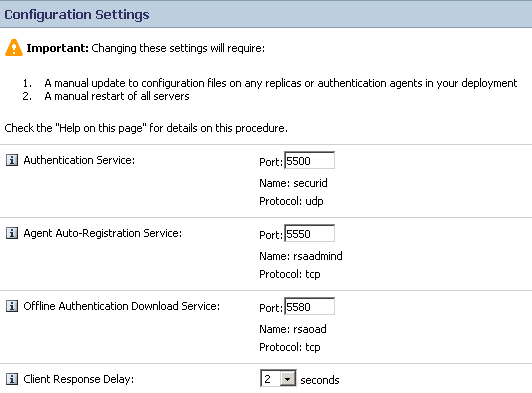
Checking the time on systems
- RSA is time sensitive. Verify time on the RSA server and TPAM server are the same. Ideally they would use the same NTP server, but that is not necessary as long as the time on both devices is the same.Non Matching Hash
- Problems created when the embedded hash of the Check Points IP address (that is sent to the ACE SERVER within the authentication request) being different than the hash of the Check Point`s IP address that is generated by the ACE SERVER. This can be caused by multi-homed or NAT configurations. Create a text file with name rdopts.rec. In the sdopts.rec file, insert the line CLIENT_IP=x.x.x.x, where "x.x.x.x" is the Cluster member's primary IP address, as defined on the ACE. Upload file to TPAM. As seen on Real Time Monitoring.
Reviewing the RSA SecurID Server Real Time Monitoring
- RSA has Real Time Monitoring to view authentication problems. Most RSA SecurID servers provide some kind of log or monitoring facility which can show you authentication attempts. It may be helpful to watch either the log or monitor in real time as someone attempts to authenticate. If no logs are generated, that most likely indicates that the TPAM and RSA SecurID server are not communicating. If logs are generated, the logs should give you an idea of why the authentication is being rejected. The three things to closely inspect in the RSA SecurID configuration are the Agent Host IP address it is expecting traffic from, the clients that are allowed, and the assignment of tokens. For information about viewing those configurations, refer to your RSA SecurID vendor's documentation.
Real Time Monitoring
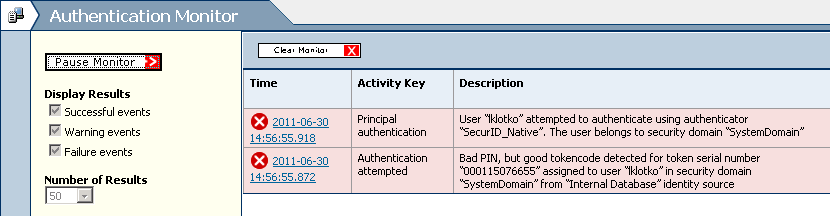
Cont.: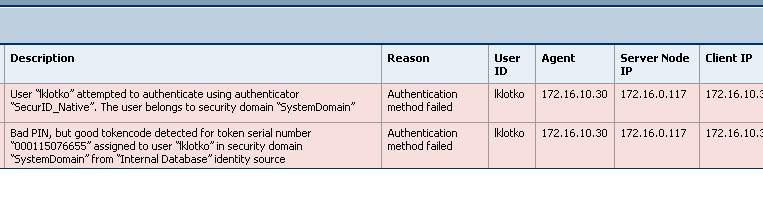
Error Messages
The following errors indicate communication failures between TPAM and RSA. Check Network Settings, IP etc.
Communication with Authentication Manager Failed:
Unable to Complete SecurID Authentication:
Access Denied
The User is not Granted Permission. Look at the Reporting on RSA server to determine why the Access was denied. Verify the User has Access in TPAM.
Configuration File
Definitionssdconf.rec
Generated by the ACE SERVER. Uploaded to TPAM
sdopts.rec
Allows you to force the ACE AGENT to use a specific IP address when generating its hash. Created by client and uploaded to TPAM
sdstatus.12
Automatically created at point of communication between the ACE AGENT and SERVER
securid
Automatically created at point of successful communication between the ACE AGENT and SERVER (Node Secret File)
-
Additional Information
For setup/configuration steps, please refer to Knowledge Article 124123, SecurID External Authentication: Enable an ACE server with TPAM. Please refer to the RSA website for more information about RSA: http://www.emc.com/domains/rsa/index.htm.
