Setting up the front-end authenticator in sp-cam.demo.local
To set up the front-end authenticator in sp-cam.demo.local
- Log in to the Cloud Access Manager instance on sp-cam.demo.local as the fallback administrator.
- From the main menu in the Front-end Authentication section, click + Add New.
- On the Authenticator Type page choose SAML Federated.
-
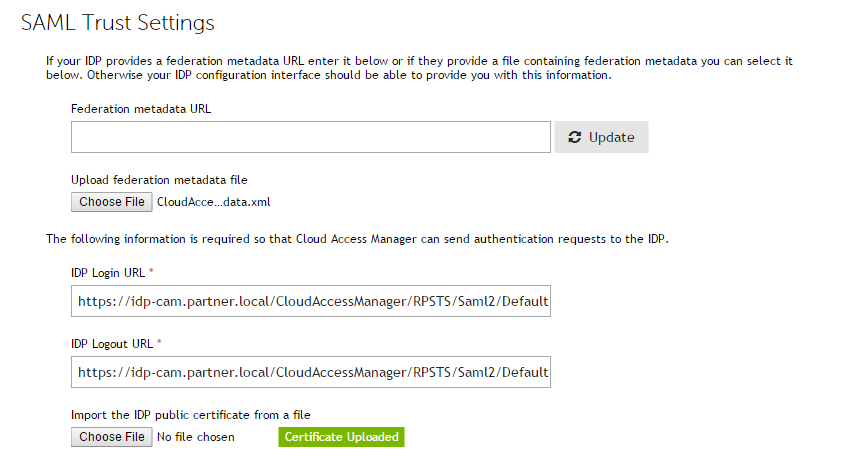
Click Next. On the SAML Trust Settings page, upload the Federation metadata file which you downloaded from the Federation Settings page of the Application Configuration wizard. Please refer to step 15 of Configuring the SAML application manually in the section Configuring the SAML application on idp-cam.partner.local for details.
- We have used metadata to configure our Service Provider so there is no need to enter an IDP Login URL, IDP Logout URL or import the Identity Provider (IDP) public certificate manually. This information is loaded automatically when the metadata file is imported.
-
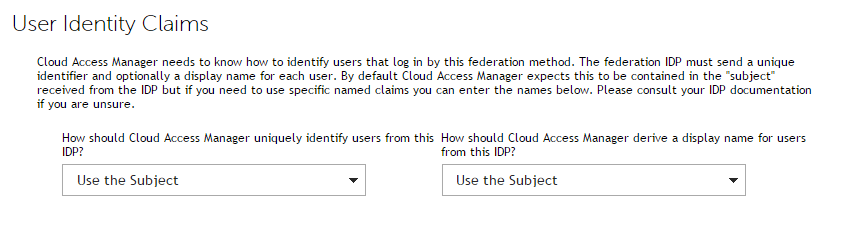
The User Identity Claims page is displayed. Here you can specify how Cloud Access Manager will uniquely identify users and derive the display name of users from this IDP. In this example, we allow both to default to Use the Subject.
- In the Authenticator Name field enter CAM IDP.
- Click Finish.
-
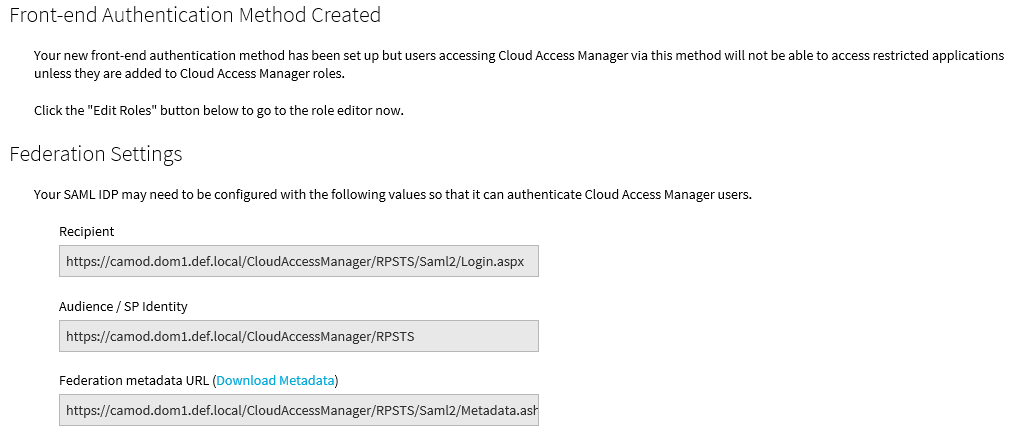
The federation settings for the Service Provider are displayed.
- The Cloud Access Manager Identity Provider is now configured. You may want to configure the roles for the FEA at this point to control user access to applications. If so, click Edit Roles and carry out the remaining steps, otherwise click Finish.
- If you have followed the instructions in the section Configuring Cloud Access Manager roles to be returned then the roles from the IDP will be available when logging in using the newly created FEA. The Admin and Users roles will work automatically, any other roles you have created on the IDP you will have to add manually. To start, click Add Role.
- In the Edit Role section enter a name and description for the role.
- Click Add User.
- Select the new FEA from the User’s Authenticator list if it is not already selected.
- Edit the Include users with a claim named field to contain urn:cam/sso/role. This is the claim type for roles returned from the IDP.
- In the Having value field enter the name of the role as defined in the IDP roles, for example if you have created a role on the IDP with the name Sales, then you should enter Sales here.
- Click Save.
- Repeat steps 11 to 17 for any additional roles that are required.
Testing your configuration
You have now configured both Cloud Access Manager instances. When users attempt to access sp-cam.demo.local they are redirected to idp-cam.partner.local for authentication.
To test the configuration
-
Log onto any machine in the idp-cam.partner.local forest.
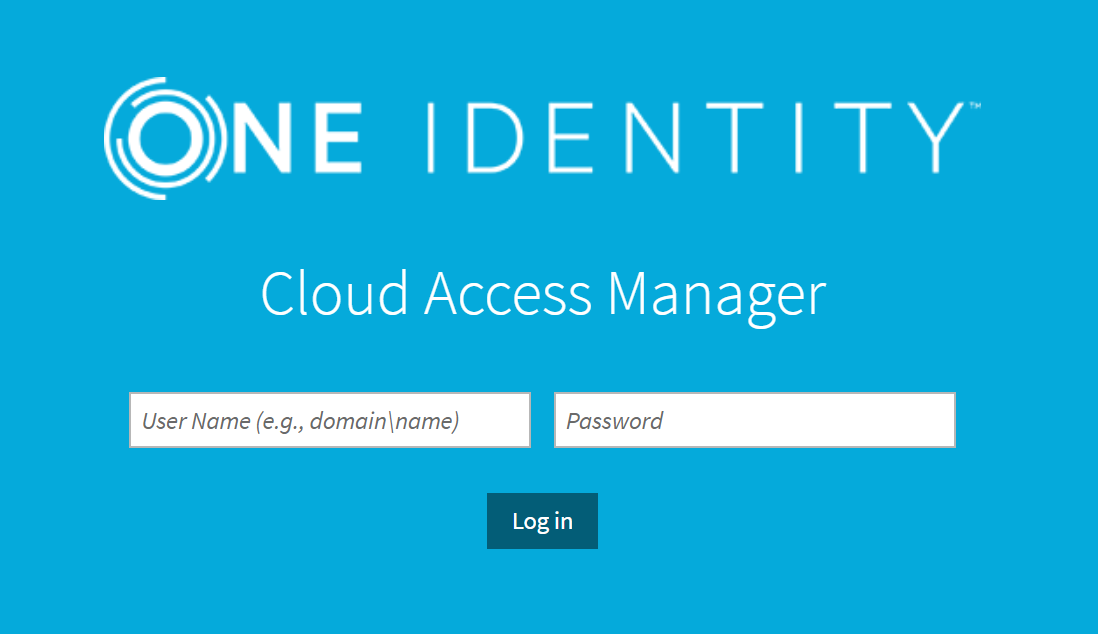
Open a browser and navigate to the Cloud Access Manager application portal on sp-cam.demo.local https://sp-cam.demo.local/CloudAccessManager
-
The browser is redirected to the Identity Provider’s log in page. Enter the credentials for a user defined in the idp-cam.partner.local forest.
- The user is authenticated by the Identity Provider. If the authentication is successful, the browser is redirected to sp-cam.demo.local and the Application Portal is displayed.