Use this task to maintain rule supervisors for the selected rule. To do this, assign identities that are allowed to edit this rule to the applications roles entered for exception approvers on the main data form.
NOTE: Changes apply to all the rules assigned to this application role.
To authorize identities as rule supervisors
-
In the Manager, select the Identity Audit > Rules category.
-
Select the rule in the result list.
-
Select the Maintain rule supervisors task.
-
In the Add assignments pane, add identities.
TIP: In the Remove assignments pane, you can remove assigned identities.
To remove an assignment
- Save the changes.
Related topics
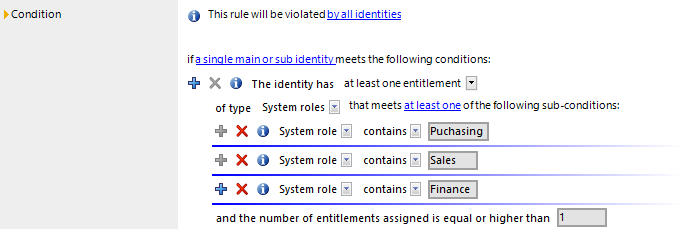
In the rule condition, you combine all the entitlements that lead to a rule violation. In the rule condition, the identities and the entitlements affected are separately restricted. The affected identities are used to determine which identities and sub-identities the rule condition is applied to. The affected entitlements are used to define the properties that result in the affected identities violating a rule. The entitlements are determined through the object relations of the affected persons (PersonHasObject table).
The Rule Editor is there to help you formulate rule conditions. You can use predefined condition type and operator for this. The complete database query is composed internally. If the QER | ComplianceCheck | SimpleMode | ShowDescriptions configuration parameter is set, additional input fields are displayed in the simplified definition, providing a more detailed description of each rule block.
Figure 2: Rule Editor for simple definition of rules
The Rule Editor control elements supply operators and properties that you need for formulating partial conditions. You can only select one entry from the drop-down menu. You can select more entries from extended drop-down menus, where the properties are displayed hierarchically and then added to the condition using an "or" operator. You may enter text directly into input fields. Pop-up menus and input fields are shown and hidden dynamically.
A rule condition is made up of several rule blocks. A rule violation is detected when an person, with properties and assignments, can be matched to all the rule blocks.
There are two types of rule blocks:
-
Affected identities
Each rule must obtain exactly one rule block that determines the identities that the rule should be applied to. By default, all identities with all subidentities are taken into account. You can, however, restrict the identities further.
-
Entitlements affected
You need to define at least one rule block that finds affected entitlements. The properties that result in a rule violation in the identities affected are defined here. You can check the following entitlements in the rule block: roles, target system groups, system entitlements, system roles, software, resources.
You can add any number of partial conditions within one rule block and link them with each other using the Rule Editor. Use the options All and At least one to specify whether one or all partial conditions in the block have to be fulfilled.
Table 21: Meaning of icons in the Rule Editor
|

|
Add another partial condition or another rule block. A new line is displayed for entering the condition. |
|

|
Delete the partial condition or rule block. The line is removed. |
|

|
Opens the preview window. Affected objects are shown. |
|

|
The list of affected objects is shown in the preview window. |
To display a preview of affected objects
-
Click the condition or partial condition Rule Editor in the  .
.
-
Click  in the preview window to display the list of affected objects.
in the preview window to display the list of affected objects.
Each rule has to contain exactly one rule block which specifies the identities.
Figure 3: Rule block for the identities affected
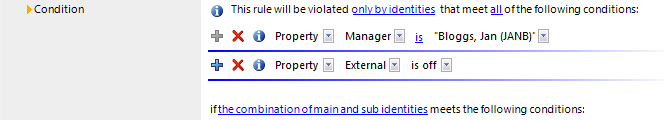
Use the following to options to limit the affected identity groups.
-
By all identities
All identities are taken into account.
-
only by identities that fulfill all|at least one of the following conditions:
You can limit the affected identities with a condition, for example, "All identities in group A" or "All external identities". To determine the affected identities, formulate the appropriate partial conditions.
You can specify a condition type in the first menu of the partial condition which restricts the affected identities.
-
Property: Identity properties. The permitted properties menu is already limited to the most important identity properties.
-
For the user account with target system type: Properties of the user accounts to which the identities are connected, having the selected target system type.
-
SQL Clause: Freely defined SQL condition (WHERE clause). For more information about the WHERE clause wizard, see the One Identity Manager User Guide for One Identity Manager Tools User Interface.
Specify whether the main or subidentities are taken individually or collectively into account by the rule check.
-
A single main or subidentity
If an identity has subidentities, they are considered individually and independently of another by the rule check. The rule is violated if the main identity or a subidentity satisfies the rule condition.
The rule is not violated if the main identity satisfies the rule condition only because of its subidentities.
-
The combination of main and subidentities
If an identity has subidentities and the main identity belongs to the affected identities, they are considered collectively in the rule check. The rule is violated if:
If the subidentity alone belongs to the affected identities, the rule is only violated if the subidentity fulfills the rule condition itself. If the main identity or another subidentity fulfills the rule condition, the rule for the determined subidentity is not violated.
For more information about main and subidentities, see the One Identity Manager Identity Management Base Module Administration Guide.
Related topics
.






