Management Policy and other Password Manager settings
The following diagram illustrates how several Management Policies interact with other Password Manager settings.
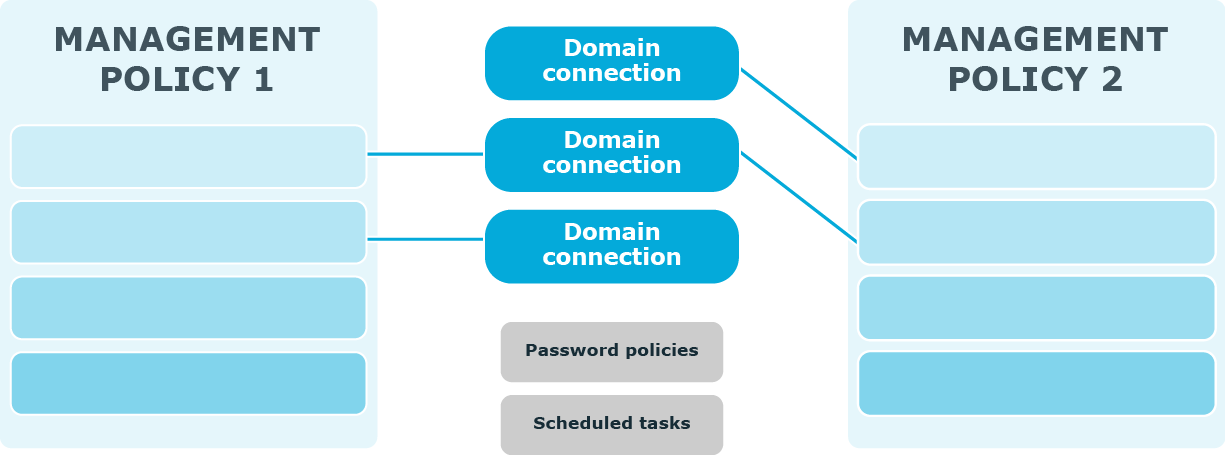
In a single Password Manager instance, you can create multiple Management Policies. Different Management Policies may use the same domain connections (specified in the user and Helpdesk scopes). If a user is included in the user scopes of both Management Policies, the settings from the first Management Policy in which scope the user is found will be applied to the user.
Settings from each Management Policy use the same scheduled tasks and password policies.
The Invitation to Create/Update Profile, Reminder to Create/Update Profiles, Reminder to Change Password scheduled tasks allow notifying users from scopes of user enforcement rules configured in Management Policies. For more information, see Scheduled tasks and User enforcement rules.
To set password policies for users from user scopes of Management Policies, you need to configure password policies and include corresponding users to the password policy scope. For more information about password policies, see Creating and Configuring a Password Policy.
Password policy overview
Password Manager provides the opportunity to apply and manage custom One Identity password policies and Windows fine-grained password policies.
The following diagram shows available password policies and their structure.
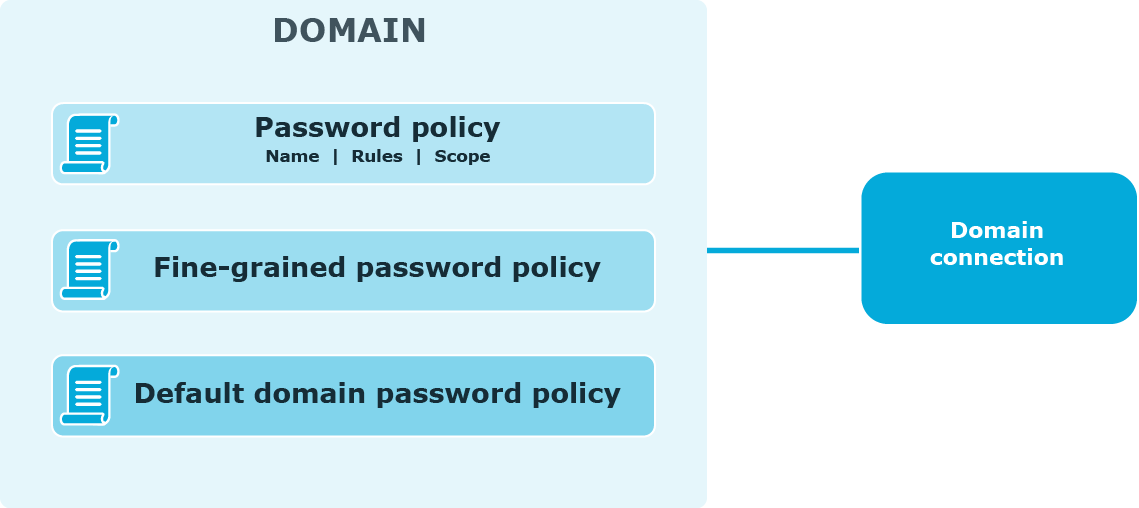
Using One Identity password policies
With Password Manager, you can create custom password policies that extend the system password policy rules.
To create and manage One Identity password policies, you need to add a domain connection on the Password Policies tab of the Administration Site. When adding the domain connection, you specify the domain to which password policies will be applied and the credentials that will be used to access the domain.
After you have added the domain connection, you can create password policies for this domain. For each password policy, you can specify a name, a set of policy rules, and a scope.
NOTE: Password policy rules are applied and displayed on the Self-Service Site when users change or reset passwords only after you have added the domain connection and created policies for the corresponding domain.
Using fine-grained password policies
By default, existing fine-grained password policies are applied to users from fine-grained password policies’ scopes. But to be able to manage fine-grained password policies and to have the Self-Service Site display the password policy rules when users reset or change passwords, you need to add a domain connection on the Password Policies tab of the Administration Site.
When adding the domain connection, you specify the domain to which password policies will be applied and the credentials that will be used to access the domain.
NOTE: The default domain password policy is applied to users from the policy scope, but the policy itself is not displayed in the policy list on the Administration Site.
NOTE: Creating a new Windows fine-grained password policies, does not contain a Policy Scope by default. Hence, by clicking Edit on the newly created Windows fine-grained password policies and configuring the required Policy Scope in the Password Policy Properties window, one can view these policies for the configured users in the Self-Service Site.


