Once you add and profile hosts, the mangement console allows you to perform a series of tests to verify that a host meets the minimum requirements to configure a policy server or join a remote host to either a Privilege Manager policy group or an Active Directory domain. Running the readiness checks does NOT require elevated privileges.
To check readiness
-
Select one or more hosts on the All Hosts view of the Hosts tab.
-
Open the Check menu from the Prepare panel of the task bar and choose
- Check Policy Server Readiness
- Check Client for Policy Readiness
- Check Host for AD readiness
- Check QAS agent status
- Check QAS agent status automatically
Note: You must add and profile a Privilege Manager Policy Server to the mangement console and set it as Active before the Check Client for Policy Readiness option is available on the Check menu.
You must be logged on as the supervisor or an Active Directory account in the Manage Hosts Role to perform any task on the Check menu.
See the following topics for more information about these options:
Management Console for Unix simplifies local host management on Unix, Linux, and Mac systems.
Once a you have successfully added and profiled one or more hosts, you can remotely deploy software products to them from the mangement console.
The Install Software dialog displays when you select the Install Software toolbar button.
From this dialog, select the software products you want to deploy and install on the selected hosts.
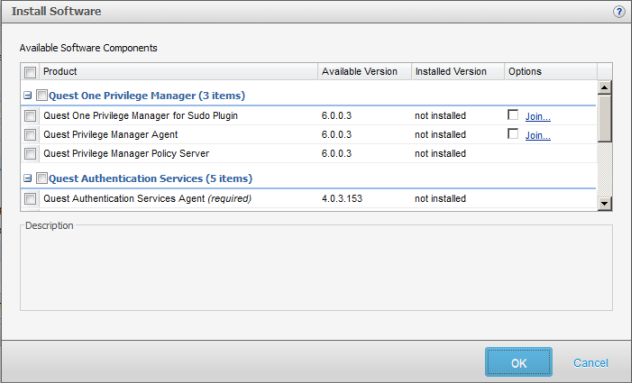
Note: If you do not see all of these software packages, verify that the path to the software packages is correctly set in System Settings. Refer to:
Available software components
You can install the following software products remotely from the mangement console:
- Privilege Manager (3 items)
- Sudo Plugin - Select to install a component that enables the host to use a centrally managed sudoers policy file located on the Privilege Manager primary server from the mangement console.
- Privilege Manager Agent - Select to install a component that enables the host to use a centrally managed pmpolicy policy file located on the primary policy server from the mangement console.
- Privilege Manager Policy Server - Select to install the Privilege Manager Policy Server which provides central policy management, granular access control reporting, as well as the ability to enable, gather, store and playback keystroke logs.
Note: Centralized policy management and keystroke logging are licensed separately.
Note: When you install the Privilege Manager Policy Server it installs all three Privilege Manager for Unix packages on that host. However, once you have installed the Sudo Plugin onto a remote host, the mangement console will not allow you to install the PM Agent on that host; and once you have installed the PM Agent onto a remote host, the mangement console will not allow you to install the Sudo Plugin on that host.
- Authentication Services (5 items)
- Authentication Services Agent (Required) - Select to allow Active Directory users access to selected host. Authentication Services provides centralized user and authentication management. It uses Kerberos and LDAP to provide secure data transport and an authentication framework that works with Microsoft Active Directory. Components include: vasd, nss_vas, pam_vas, and vastool.
- Authentication Services for Group Policy (Required) - Select to install the Group Policy component which provides Active Directory Group Policy support for Unix, Linux, and Mac platforms.
- Authentication Services for NIS - Select to install the NIS Proxy component which provides the NIS compatibility features for Authentication Services. vasyp is a NIS daemon that acts as a ypserv replacement on each host.
- Authentication Services for LDAP - Select to install the LDAP Proxy component which provides a way for applications that use LDAP bind to authenticate users to Active Directory without using secure LDAP (LDAPS). Instead of sending LDAP traffic directly to Active Directory domain controllers, you can configure applications to send plain text LDAP traffic to vasldapd by means of the loopback interface. vasldapd proxies these requests to Active Directory using Kerberos as the security mechanism.
- Dynamic DNS Updater - Select to install the Dynamic DNS Updater component which provides a way to dynamically update host records in DNS and can be triggered by DHCP updates.
- Defender (1 item)
- Defender PAM Module - Select to install the Defender authentication components for PAM based Unix/Linux systems. Includes PAM module, documentation and utilities to appropriately configure the PAM subsystem for Active Directory/Defender OTP authentication.
For more information about installing software components:
Management Console for Unix provides both basic and advanced search options to help you find and select hosts from the All Hosts view or user accounts from the All Local Users tab.

