Configuring host access control
The mangement console allows you to modify Authentication Services access settings. You can add Active Directory users or groups to the users.allow file for a single host or a selected group of hosts. This allows you to control Active Directory user access on Authentication Services hosts.
Note: The mangement console does not allow you to view or modify the users.deny file.
To view the users.allow file for a single host
- From the All Hosts view, right-click a host that is joined to an Active Directory domain.
- Select the Host Access Control option from the context menu.
The Host Access Control tab lists the content of the users.allow file.
Note: Users and Groups displayed in red text indicate that Authentication Services could not resolve the user/group in Active Directory.
To allow additional Active Directory users or groups to access a single host
- From the Host Access Control tab, click Manage Access.
- On the Host Access Control dialog, specify the names you want to allow access to the selected host.
You can either:
Once you have the names listed on the Host Access Control dialog, click OK.
- On the Log on to Host dialog, enter the user credentials to access the selected host and click OK.
The console updates the users.allow file and the database accordingly.
To add or remove access for Active Directory users or groups on multiple hosts
- From the All Hosts view, select and right-click multiple hosts that are joined to an Active Directory domain.
- Select the Host Access Control option from the context menu.
The Host Access Control dialog displays two list boxes: one in which to add users or groups, the other to specify users and groups to remove from the users.allow file.
- Specify or select names to add or remove and click OK.
- On the Log on to Host dialog, enter the user credentials to access the selected hosts and click OK.
The console updates the users.allow file and the database accordingly.
Check QAS Agent Status
You can either check the health status of Authentication Services agents manually, or you can configure the mangement console to automatically check the QAS agent status and report any warnings or failures to the console.
Note: Running the Check QAS Agent Status commands requires:
- you are logged on as an Active Directory account in the Manage Hosts role
- the hosts have Authentication Services 4.0.3.78 (or later) Agent software installed
For more information, see Check QAS agent status commands not available.
Manually checking QAS agent status
To check QAS agent status
-
Select one or more hosts on the All Hosts view, open the Check menu from the Prepare panel of the toolbar and choose Check QAS agent status.
-
In the Log on to Host dialog, enter the user credentials to access the selected hosts and click OK.
A progress bar displays in the task progress pane and the Host Notifications tab indicates the number of hosts with warnings or failures detected.
Note: This task requires elevated credentials.
If you select multiple hosts, you are asked if you want to use the same credentials for all the hosts (default) or enter different credentials for each host.
- If you selected multiple hosts and the Use the same credentials for all selected hosts option, enter your credentials to log on to access the selected hosts and click OK.
- If you selected multiple hosts and the Enter different credentials for each selected host option, it displays a grid which allows you to enter different credentials for each host listed. Place your cursor in a cell in the grid to activate it and enter the data.
-
Select the Host Notifications tab to view the reported warnings or failures.
See Viewing the QAS status errors for details.
Automatically checking QAS agent status
To have updated information about the status of Authentication Services agents, you can configure the mangement console to periodically check the QAS agent status automatically. If it detects a status change on the host, it reports the following warnings or failures to the Host Notifications tab:
- Critical Failure
- Failure
- Warning
To configure the console to automatically check the QAS agent status
-
Select one or more hosts on the All Hosts view, open the Check menu from the Prepare panel of the toolbar, and choose Check QAS agent status automatically...
Note: This option is only available for multiple hosts if all hosts are in the same "Check QAS agent status" state; that is, they all have automatic status checking turned on, or they all have automatic status checking turned off.
-
Select the Check status automatically option, set the frequency for the health status check, and click OK.
Note: Use standard crontab syntax when entering Advanced schedule settings.
-
On the Log on to Host dialog, enter the user credentials to access the selected hosts and click OK.
Note: This task requires elevated credentials.
When configured for automatic checking, the QAS state column on the All Hosts view displays the 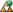 icon. Then, if the server does not receive a heartbeat in over 4 hours (by default), it displays the
icon. Then, if the server does not receive a heartbeat in over 4 hours (by default), it displays the  icon. No icon in the QAS state column indicates the host is not configured to check the QAS agent status automatically.
icon. No icon in the QAS state column indicates the host is not configured to check the QAS agent status automatically.
If you select multiple hosts, you are asked if you want to use the same credentials for all the hosts (default) or enter different credentials for each host.
- If you selected multiple hosts and the Use the same credentials for all selected hosts option, enter your credentials to log on to access the selected hosts and click OK.
- If you selected multiple hosts and the Enter different credentials for each selected host option, it displays a grid which allows you to enter different credentials for each host listed. Place your cursor in a cell in the grid to activate it and enter the data.
-
View the QAS Agent status for each host on the Host Notification tab.
See Viewing the QAS status errors for details.
When you configure a host to check the QAS agent status automatically, the mangement console,
- Creates "questusr" (the user service account), if it does not already exist, and, a corresponding "questgrp" group on the host that the mangement console uses for automatic QAS agent status checking.
- Adds questusr as an implicit member of questgrp.
- Adds the auto-check SSH key to questusr's authorized_keys, /var/opt/quest/home/questusr/.ssh/authorized_keys.
- Verifies the user service account can login to the host.
- Creates a Authentication Services cron job that runs QAS status according to the specified interval.
Note: If you receive an error message saying you could not log in with the user service account, please refer to Service account login fails to troubleshooting this issue.
The questusr account is a non-privileged account that does not require root-level permissions. This account is used by the console to gather information about existing users and groups in a read-only fashion, however, the mangement console does not use the questusr account to make changes to any configuration files.
Note: If questusr is inadvertently deleted from the console, the console will not be updated. To recreate the "questusr" account, re-configure the host for automatic QAS agent status checking.
To disable automatic status checking
- Select one or more hosts on the All Hosts view and choose Check QAS agent status automatically....
- Clear the Check status automatically option on the Check QAS Agent Status Automatically dialog and click OK.
- On the Log on to Host dialog, enter the user credentials to access the selected hosts and click OK.
When you disable auto-status checking for a host, the mangement console
- Leaves the "questusr" and the corresponding "questgrp" accounts on the host.
- Leaves questusr as an implicit member of questgrp.
- Removes the auto-check SSH key from that user's authorized_keys file.
- Removes the cron job on the host.

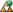 icon. Then, if the server does not receive a heartbeat in over 4 hours (by default), it displays the
icon. Then, if the server does not receive a heartbeat in over 4 hours (by default), it displays the  icon. No icon in the
icon. No icon in the