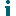Configuring privileged application discovery
- Click Next to use the Filters tab to filter out Application Discovery data according to different application specific criteria.
On the Filters tab, select the checkbox to enable application filters.
Enter filter criteria in at least one of the available boxes (Executable path contains, Product name contains, Publisher name contains, and File description contains).
An application only needs to meet a single filter criteria in order for its Application Discovery data to be filtered out. A comma delimiter can be used to enter multiple criteria in each filter box.
NOTE: The Privilege Manager client will not transmit any Application Discovery data for application(s) that meet any of the existing filter criteria.
Use the Privileged Application Discovery Settings Wizard to collect information about the privileged applications used over your network during a specified time period. By default, once this feature is enabled, it is set to collect information for two weeks, but you can adjust the setting. To access the wizard from the Getting Started screen, select the Setup Tasks tab and then double-click the Privileged Application Discovery Settings Wizard. Follow the prompts or see the Administrator Guide for step-by-step instructions.
Configuring approved privileged applications
Processing discovered privileged applications
Use the Privileged Application Discovery screen under the Discovery & Remediation tab to process the privileged applications that were reported by the client computers. If these applications are approved and need to continue even after the least-privileged environment is in place, use this screen to automatically create and assign elevation rules to appropriate groups. If a discovered application will not be approved for use in the least privileged environment, you can ignore these applications and they will no longer display. Follow the prompts or see the Administrator Guide for step-by-step instructions.
Deploying rules
To create the default rules provided by Privilege Manager, use the Create GPO with Default Rules Wizard. To access the wizard from the Getting Started screen, select the Setup Tasks tab and then double-click Create GPO with default rules. Follow the prompts or see the Administrator Guide for step-by-step instructions.
Removing local admin rights
The last step in preparing your environment for least privileged use is to remove administrative access from users who no longer require it.
Using the Active Directory Users and Computers utility
Use the Windows utility Active Directory Users and Computers, installed on Windows Server operating systems such as Windows 2008, to scrub the Domain Administrators group of users that should no longer be given administrative rights to every computer in the domain. Select Domain Admins Properties > Members tab > Remove.
-
Click the Discover Accounts in local Administrator groups button to discover users and domain groups with local administrator rights. By default, the search results will only include domain users and domain groups. However, you can optionally opt to include local and built-in (for informational purposes only) users as well.
Using the Users with Local Admin Rights screen
Under the Discovery & Remediation tab on the console, select the Users with Local Admin Rights screen to discover which domain users have been assigned to the local Administrators group on client computers and remove them. See the Administrator Guide for step-by-step instructions.
Congratulations - You are now running in a least privileged use environment!
Maintaining a least privileged use environment
Maintain a least privileged use environment by processing self-service elevation requests, using the Console Email Configuration screen, and using group policy settings.