Multiple users and locking
Multiple administrators can access the One Identity Safeguard for Privileged Sessions (SPS) web interface simultaneously, but only one of them can modify the configuration. This means that the configuration of SPS is automatically locked when the first administrator who can modify the configuration opens a configuration page (for example the Basic Settings or the Users & Access Control menu).
The warning message displays the username of the administrator locking the configuration as shown in the image below:
Figure 36: Configuration lock by remote administrator
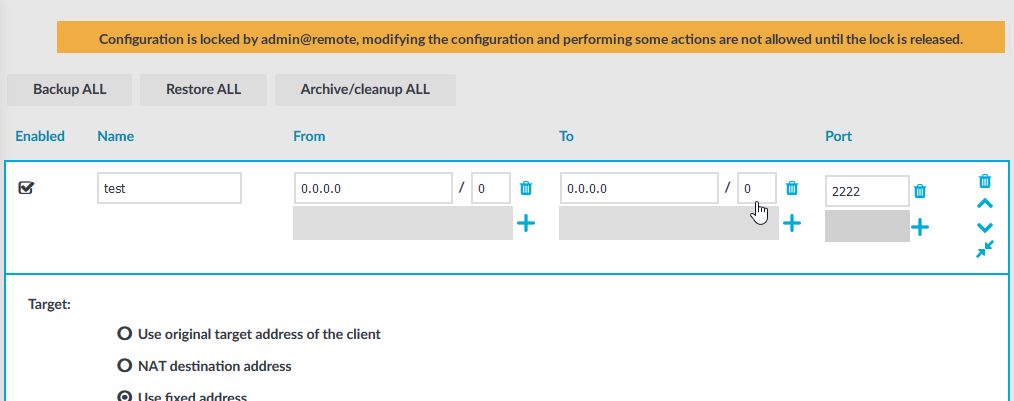
Other administrators can continue as read-only but must wait until the locking administrator navigates to an SPS page that does not require locking, the administrator logs out, or the session of the administrator times out. However, it is possible to access the Search and Reporting menus,
NOTE: Accessing SPS using the RPC API or starting a transaction in the REST API locks the configuration similarly to accessing SPS from the web interface.
However, there can be multiple transactions through REST API, simultaneously.
NOTE: If an administrator logs in to SPS using the local console or a remote SSH connection, the configuration is also locked. Inactive local and SSH connections timeout just like web connections. For details, see Accessing the One Identity Safeguard for Privileged Sessions (SPS) console.
Web interface timeout
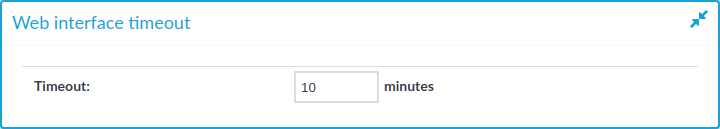
By default, One Identity Safeguard for Privileged Sessions (SPS) terminates the web session of a user after ten minutes of inactivity. To change value of this timeout, adjust the Basic Settings > Management > Web interface timeout option.
Figure 37: Basic Settings > Management > Web interface timeout — Web interface timeout
Authentication banner
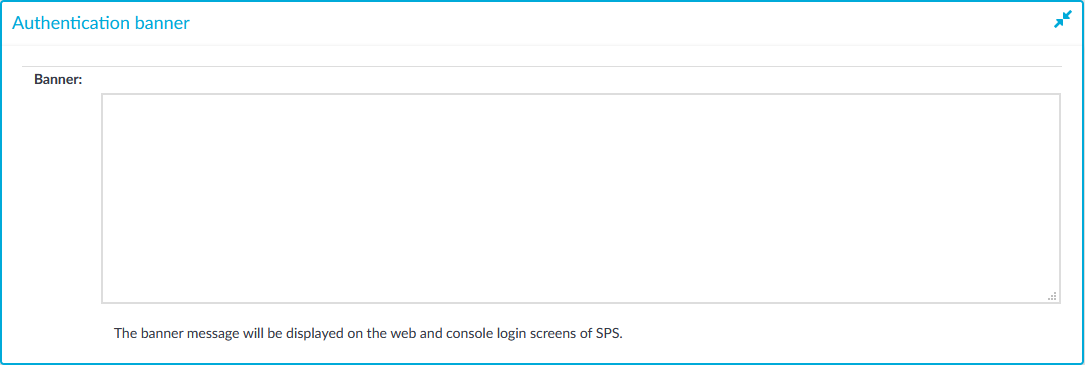
You can display a banner with a configurable text on the web and console login screen of SPS.
Users will see the banner every time they try to log in to SPS. The banner text is displayed as plain text on the login screen and whitespace is preserved.
To enter a banner message, navigate to Basic Settings > Management > Authentication banner.
Figure 38: Basic Settings > Management > Authentication banner — Enter a banner message
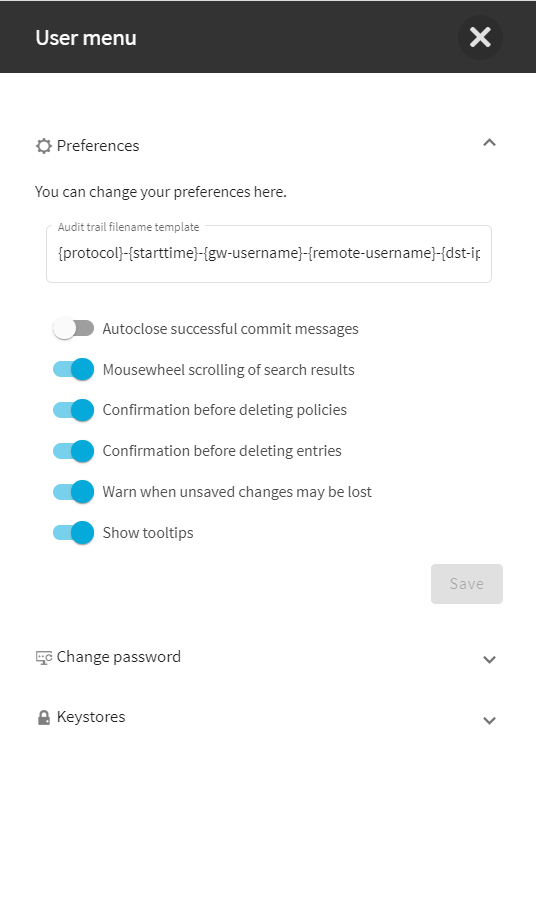
Preferences
To configure your preferences about the web interface, navigate to User Menu > Preferences.
Figure 39: User Menu > Preferences
-
Audit trail filename template:
To change the filename of the audit trails, navigate to User menu > Preferences and change the Audit trail filename template. The default template is {protocol}-{starttime}-{gw-username}-{remote-username}-{dst-ip}.zat. The template can include anything, the keys (inside {} brackets) are replaced with their actual values. These keys are the following:
-
connection-policy: The connection policy
-
dst-ip: Destination IP address
-
dst-port: Destination port
-
gw-username: Gateway username
-
protocol: Protocol
-
remote-username: Remote username
-
session-id: Session ID
-
src-ip: Source IP address
-
starttime: Start time of the session
-
-
Autoclose successful commit messages: General confirmation windows will not appear. (For example, Configuration saved successfully that appears after successfully committing a change). As a result, pop-up windows appear only for failed actions or errors.
-
Mousewheel scrolling of search results: When there are several pages of displayable search results on the Search page, navigate between search result pages with the mousewheel. When turned off, using the mousewheel on the Search page scrolls the whole page.
-
Confirmation before deleting policies: Display a pop-up window when you attempt to delete policies to prevent deleting policies accidentally.
-
Confirmation before deleting entries: Display a pop-up window when you attempt to delete entries to prevent deleting entries accidentally.
-
Warn when unsaved changes may be lost: Display a pop-up window to warn when you navigate to another window without committing your changes to prevent losing unsaved changes.
-
Show tooltips: Display tooltips for user interface elements to help using the product.
