For the client-side connection, One Identity Safeguard for Privileged Sessions (SPS) can authenticate the client inband (within the SSH protocol) using the following authentication methods:
Figure 155: Traffic Controls > SSH > Authentication Policies — Configuring client-side authentication methods
-
Local user database: Authenticate the client locally on the SPS gateway. For details, see Local client-side authentication.
-
LDAP: SPS will authenticate the client to the LDAP database set in the LDAP Server of the connection policy. To use LDAP authentication on the client side, select LDAP, and select the permitted authentication methods (Password, Public key). More than one method can be permitted.
NOTE:
-
SPS will authenticate the client-side connection to the LDAP server configured in the connection policy. This is not necessarily the same as the LDAP server used to authenticate the users accessing the SPS web interface.
-
The public keys of the users stored in the LDAP database must be in OpenSSH format.
-
-
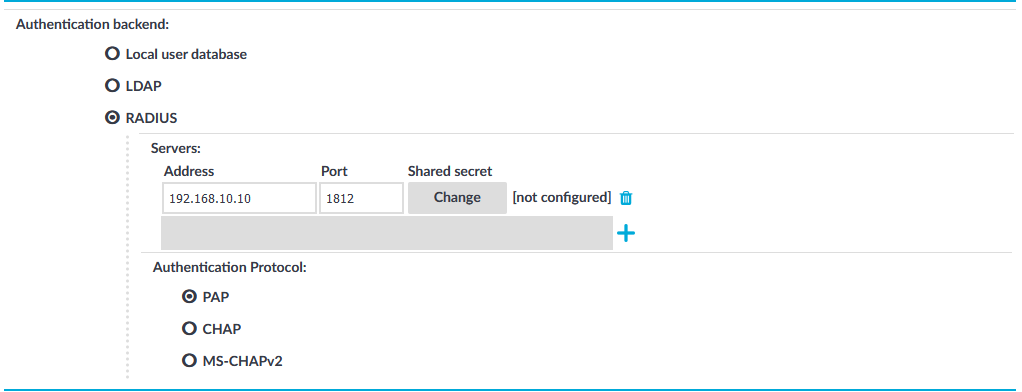
RADIUS: SPS will authenticate the client to the specified RADIUS server. Select RADIUS, enter the IP address or hostname of the RADIUS server into the Address field, the port number of the RADIUS server into the Port field, and the shared secret of the RADIUS server into the Shared secret field. Only password-authentication is supported (including one-time passwords), challenge-response based authentication is not.
To use the:
-
Password Authentication Protocol, select PAP.
-
Challenge-Handshake Authentication Protocol, select CHAP.
-
Microsoft version of the Challenge-Handshake Authentication Protocol, select MS-CHAPv2.
Use an IPv4 address.
To add more RADIUS servers, click
and fill in the respective fields.
-
To use certificates to authenticate the client, you can use the LDAP and the Local user database backends.
Figure 156: Client-side inband gateway authentication with different certificates

