One Identity Safeguard for Privileged Sessions (SPS) has a search interface for browsing the audit trails. This connection database also contains the various meta-information about connections and connection-requests. The search queries can include only alphanumerical characters.
To access the search interface, navigate to Search. Only users with the following privileges can access the Search page:
-
Members of groups who are configured as Authorizers with the Search or Search&Authorize permission set in the Access Control field of a connection policy. These users can access only the audit trails of the respective connections.
For more information on configuring authorizers for a connection, see Configuring four-eyes authorization.
-
Members of groups who have the Search privilege set.
Assigning the Search privilege to a user on the AAA page automatically enables the Search in all connections privilege, and grants the user access to every audit trail, even if the user is not a member of the groups listed in the Access Control option of the particular connection policy.
For more information on configuring user rights, see Managing user rights and usergroups.
-
The admin user.
Figure 311: Search — Browse the connections database
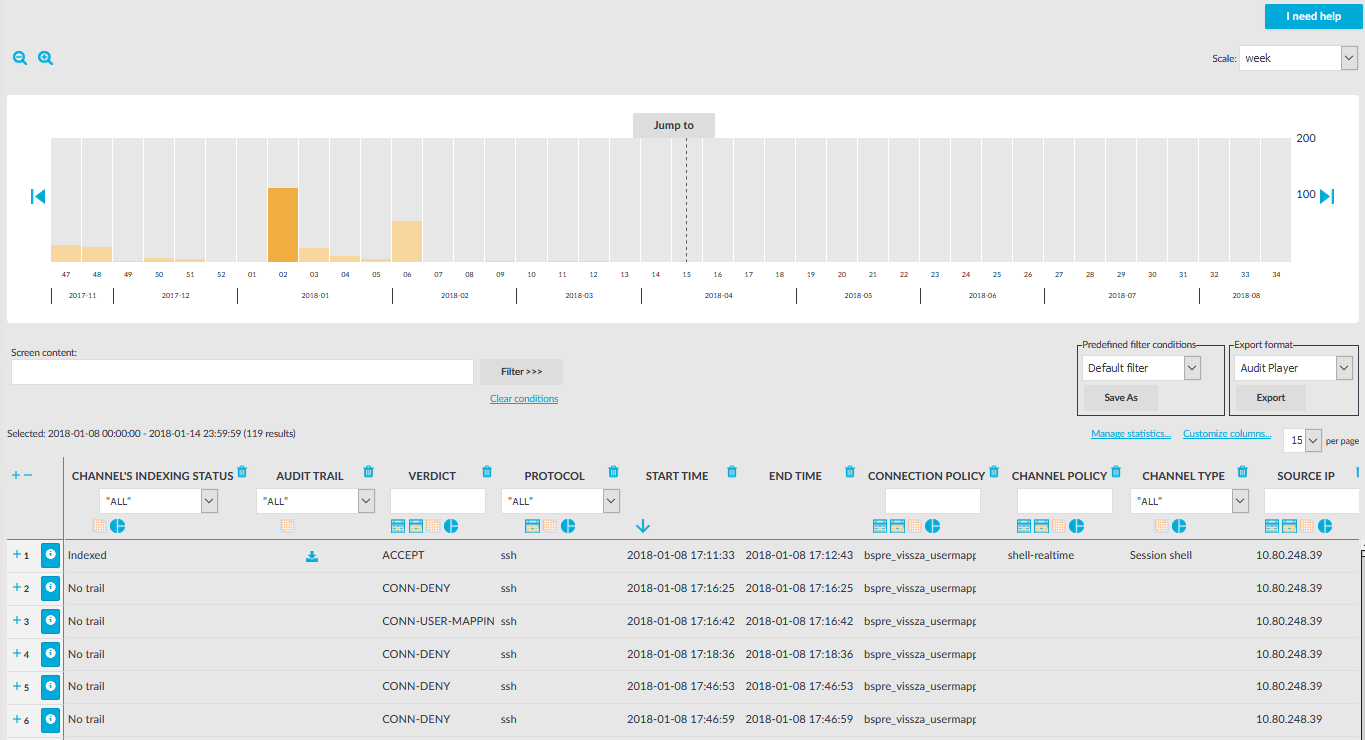
Changing the time interval
The bars display the number of results in the selected interval. Use the  and
and  icons to zoom, and the arrows to display the previous or the next intervals. To explicitly select a date, select Jump to and set the date in the calendar. You can change the length of the displayed interval with the Scale option.
icons to zoom, and the arrows to display the previous or the next intervals. To explicitly select a date, select Jump to and set the date in the calendar. You can change the length of the displayed interval with the Scale option.
Hovering the mouse above a bar displays the number of entries and the start and end date of the period that the bar represents. Click a bar to display the entries of that period in the table. Use Shift+Click to select multiple bars.
Searching connections
To search in the content of the indexed audit trails, enter your search keywords in the Screen content field, and click Filter. Search is case insensitive. You can use complex expressions and boolean operators. For more information, see Using the content search.
Filtering search results
Connection metadata is displayed in customizable columns that you can filter for any parameter, or a combination of parameters. To filter the list of search results, enter the filter expression in the input field of the appropriate column, and press Enter, or click on an entry in the table.
For the description of the available columns, see Connection metadata.
For information on using and saving filters, see Using and managing search filters.
|

|
NOTE:
When you use filters, the bars display the statistics of the filtered results. |
Filtering displays also partial matches. You can use the  icon to perform an exact search, and the
icon to perform an exact search, and the  icon for inverse filtering ("does not include"). To clear filters from a column, click
icon for inverse filtering ("does not include"). To clear filters from a column, click  .
.
To restore the original table, click Clear conditions.
|

|
TIP:
Use the drop-down menu of the Protocol column to quickly filter the list for a single protocol. |
Exporting the search results
To export the search results as a comma-separated text file, select Export format > CSV, and click Export.
For instructions on displaying statistics about your search results, see Displaying statistics on search results.
Viewing the details of a connection
To display the summary of a connection, click  , or use the
, or use the  shortcuts to view the corresponding connection details (for example, Events). The summary is displayed in the connection details pop-up window. For more information, see Connection details.
shortcuts to view the corresponding connection details (for example, Events). The summary is displayed in the connection details pop-up window. For more information, see Connection details.
To download the audit trail of a session, click the  icon in the Audit-trail column.
icon in the Audit-trail column.
The Details pop-up window provides in-depth information on each of the indexed audit trails stored in the connection database. You can use it to gain contextual insight about the indexed session and its events.
The pop-up window consists of two main parts: the header and the trail details. In the header, you can:
Figure 312: Audit trail details

Trail details
The details section is organized into tabs (left) and screenshots (right). The Details tab is always visible. The All results, Events, and Alerts tabs are displayed dynamically, when there is matching content in the trail.
Details tab: Quick summary of the connection details (user, server, time).
-
User information: remote and gateway username. The gateway username corresponds with the Username field of the connection metadata database, so note the following:
-
If the user performed inband gateway authentication in the connection, the field contains the username from the gateway authentication (gateway username).
-
Otherwise, the field contains the username used on the remote server.
-
Connection information: connection verdict, protocol, connection policy, client and server address.
-
Session time: start and end time of the connection.
-
Trail information: is the trail indexed, or archived.
-
Link: a link that leads to the Search page filtered to show only this connection. Note that if you share this link, other users can access the audit trail only if they have the required privileges, and can access One Identity Safeguard for Privileged Sessions (SPS) using the IP address in the link (SPS can be configured to be accessible using multiple IP addresses).
Figure 313: Details tab

All results tab: Matching results for your search on the Search page (or in the trail contents), in chronological order.
-
Date and time of the matching event.
-
Search rank. The displayed Rank indicates how closely the result matches your search query.
-
Screenshots. If screenshots are available for the trail, you can click each search result to view the corresponding screenshot.
Figure 314: All results tab

Events tab: Connection events, in chronological order.
-
Date and time of the event.
-
Event type (command, screen content, window title).
-
Event details.
Figure 315: Events tab

Alerts tab: Content policy alerts triggered in the session, in chronological order.
An event is listed as alert only if the Actions > Store in Connection Database option is selected in the Content Policy used to handle the session.
-
Date and time of the alert.
-
The type of the alert (command, screen content, credit card, window title).
-
The matching content.
-
Terminal buffer contents. If the alert is not visible on the screenshot, you can click the  icon to view the contents of the full terminal buffer.
icon to view the contents of the full terminal buffer.
-
Screenshots. If screenshots are available for the trail, you can click each alert to view the corresponding screenshot.
Figure 316: Alerts tab

Screenshots are generated for search results and alerts when the trail is opened, and for subsequent searches. You can scroll between screenshots using the carousel, and view each screenshot in full size. Selecting a screenshot highlights the corresponding search result or alert.
Screenshots are not available for:
|

|
NOTE:
For SSH and Telnet trails, trail data is aggregated for each second. The screenshot you see reflects the terminal buffer as it was visible at the end of that second. If data was pushed off-screen during this second, the search still finds it, but it will not be visible on the generated screenshot. |
|

|
Caution:
You can replay audit trails in your browser, or using the Safeguard Desktop Player application. Note that there are differences between these solutions.
| Works without installation |
✔ |
- |
| Works on any operating system |
✔ |
Windows, Linux, Mac |
| Can replay audit trails recorded with SPS 5 F4 and newer |
✔ |
✔ |
| Can replay TN5250 sessions |
✔ |
✔ |
| Can extract files from SCP, SFTP, HTTP and RDP sessions |
- |
✔ |
| Can replay HTTP sessions |
- |
Only exports raw files from the command line |
| Can replay X11 sessions |
✔ |
✔ |
| Can start replay while rendering is in progress |
- |
✔ |
| Can follow 4-eyes connections |
- |
✔ |
| Can replay live streams in follow mode |
- |
✔ |
| Can export to PCAP |
- |
✔ |
| Can display user input |
✔ |
✔ |
| Can display subtitles for video |
- |
✔ |
| Export audit trail as video |
- |
✔ |
| Export screen content text |
- |
✔ |
| Can search in the contents of the audit trails |
- |
✔ |
For details on the Safeguard Desktop Player application, see Safeguard Desktop Player User Guide. |
To replay an audit trail in your browser
-
On the Search page, find the audit trail you want to replay.
Figure 317: Search — Browse the connections database

-
(Optional) To replay encrypted audit trails, upload your permanent or temporary keys to the User menu > Private keystore. For more information, see Replaying encrypted audit trails in your browser.
-
Click  to display the details of the connection.
to display the details of the connection.
-
Click  to generate a video file from the audit trail that you can replay. Depending on the load of the indexer and the length and type of the audit trail, this can take several minutes (to cancel processing the audit trail, click
to generate a video file from the audit trail that you can replay. Depending on the load of the indexer and the length and type of the audit trail, this can take several minutes (to cancel processing the audit trail, click  ). The Video status field shows the progress of the this process.
). The Video status field shows the progress of the this process.
When the video is available,  changes to
changes to  .
.
Figure 318: Search — Audit trail details

-
To replay the video, click  . The Player window opens.
. The Player window opens.
-
The Player window has the following controls.
Figure 319: Replaying audit trails in your browser

-
 : Play, Pause
: Play, Pause
-
 ,
,  : Jump to previous event, Jump to next event
: Jump to previous event, Jump to next event
-
 : Adjust replay speed
: Adjust replay speed
-
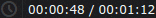 : Time since the audit trail started / Length of the audit trail. Click on the time to show the date (timestamp) of the audit trail.
: Time since the audit trail started / Length of the audit trail. Click on the time to show the date (timestamp) of the audit trail.
-
 : List of keyboard events. Special characters like ENTER, F1, and so on are displayed as buttons. If the upstream traffic is encrypted, upload your permanent or temporary keys to the User menu > Private keystore to display the keyboard events.
: List of keyboard events. Special characters like ENTER, F1, and so on are displayed as buttons. If the upstream traffic is encrypted, upload your permanent or temporary keys to the User menu > Private keystore to display the keyboard events.
-
 : Active mouse button
: Active mouse button
-
 : Create a screenshot
: Create a screenshot
-
 : Show / hide events. Select the types of events to display. Depending on the protocol used and how the audit trail was processed, SPS can display keyboard events, commands, mouse events, and window titles. Commands and window titles are displayed as subtitles at the top of the screen.
: Show / hide events. Select the types of events to display. Depending on the protocol used and how the audit trail was processed, SPS can display keyboard events, commands, mouse events, and window titles. Commands and window titles are displayed as subtitles at the top of the screen.
-
 : Fullscreen mode
: Fullscreen mode
-
 : Progress bar
: Progress bar
-
 : Shows the distribution of events. Blue - commands, green - keyboard events, yellow - mouse events, orange - window title.
: Shows the distribution of events. Blue - commands, green - keyboard events, yellow - mouse events, orange - window title.
-
 : Close the player, and return to the Connection details page.
: Close the player, and return to the Connection details page.
To view screenshots generated for encrypted audit trails, and replay encrypted audit trails in your browser, you have to upload the necessary certificates and corresponding private keys to your private keystore. Depending on the encryption, decrypting the upstream part of an audit trail might require an additional set of certificates and keys.
Only RSA keys (in PEM-encoded X.509 certificates) can be uploaded to the private keystore.
|

|
NOTE:
Certificates are used as a container and delivery mechanism. For encryption and decryption, only the keys are used. |
One Identity recommends using 2048-bit RSA keys (or stronger).
For more information on audit trail encryption, see Encrypting audit trails.
You can upload certificates permanently or temporarily. The temporary certificates are deleted when you log out of One Identity Safeguard for Privileged Sessions (SPS).
The certificates and private keys in your keystore can be protected with a passphrase. To use the certificates and private keys in a passphrase-protected keystore for decrypting audit trails, you have to unlock the keystore first by providing the security passphrase. The keystore then remains unlocked for the duration of your session.
To replay encrypted audit trails in your browser
-
Click on User menu > Private keystore.
Figure 320: User menu > Private keystore — The private keystore

-
(Optional) Create a security passphrase, if you have not configured one yet.
-
In Security passphrase, click Change.
-
In the New field, enter your new security passphrase. Repeat the same passphrase in the Confirm field.
|

|
NOTE:
One Identity Safeguard for Privileged Sessions (SPS) accepts passwords that are not longer than 150 characters. The following special characters can be used: !"#$%&'()*+,-./:;<=>?@[\]^-`{|} |
-
Click Apply.
If you forgot your security passphrase, contact our Support Team.
-
Click  to add a new certificate.
to add a new certificate.
Figure 321: Adding certificates

-
Click the first  to upload the new certificate. A pop-up window is displayed.
to upload the new certificate. A pop-up window is displayed.
Figure 322: Uploading certificates

-
Select Browse, select the file containing the certificate, and click Upload. Alternatively, you can also copy-paste the certificate into the Certificate field and click Set.
-
To upload the private key corresponding to the certificate, click the second  icon. A pop-up window is displayed.
icon. A pop-up window is displayed.
Figure 323: Uploading the private key

-
Select Browse, select the file containing the private key, provide the Password if the key is password-protected, and click Upload. Alternatively, you can also copy-paste the private key into the Key field, provide the Password there, and click Set.
-
To add more certificate-key pairs, click  and repeat the steps above.
and repeat the steps above.
-
To finish uploading certificates and keys to your private keystore, click Apply.











 and
and  buttons.
buttons. button. For details on using search expressions, see
button. For details on using search expressions, see  button to follow an ongoing connection. The trail data is exported in
button to follow an ongoing connection. The trail data is exported in 



 icon to view the contents of the full terminal buffer.
icon to view the contents of the full terminal buffer.

 to generate a video file from the audit trail that you can replay. Depending on the load of the indexer and the length and type of the audit trail, this can take several minutes (to cancel processing the audit trail, click
to generate a video file from the audit trail that you can replay. Depending on the load of the indexer and the length and type of the audit trail, this can take several minutes (to cancel processing the audit trail, click  ). The Video status field shows the progress of the this process.
). The Video status field shows the progress of the this process. .
.
 : Play, Pause
: Play, Pause ,
,  : Jump to previous event, Jump to next event
: Jump to previous event, Jump to next event : Adjust replay speed
: Adjust replay speed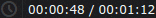 : Time since the audit trail started / Length of the audit trail. Click on the time to show the date (timestamp) of the audit trail.
: Time since the audit trail started / Length of the audit trail. Click on the time to show the date (timestamp) of the audit trail. : List of keyboard events. Special characters like ENTER, F1, and so on are displayed as buttons. If the upstream traffic is encrypted, upload your permanent or temporary keys to the User menu > Private keystore to display the keyboard events.
: List of keyboard events. Special characters like ENTER, F1, and so on are displayed as buttons. If the upstream traffic is encrypted, upload your permanent or temporary keys to the User menu > Private keystore to display the keyboard events. : Active mouse button
: Active mouse button : Create a screenshot
: Create a screenshot : Show / hide events. Select the types of events to display. Depending on the protocol used and how the audit trail was processed, SPS can display keyboard events, commands, mouse events, and window titles. Commands and window titles are displayed as subtitles at the top of the screen.
: Show / hide events. Select the types of events to display. Depending on the protocol used and how the audit trail was processed, SPS can display keyboard events, commands, mouse events, and window titles. Commands and window titles are displayed as subtitles at the top of the screen. : Fullscreen mode
: Fullscreen mode : Progress bar
: Progress bar : Shows the distribution of events. Blue - commands, green - keyboard events, yellow - mouse events, orange - window title.
: Shows the distribution of events. Blue - commands, green - keyboard events, yellow - mouse events, orange - window title. : Close the player, and return to the Connection details page.
: Close the player, and return to the Connection details page.
 to add a new certificate.
to add a new certificate.
 to upload the new certificate. A pop-up window is displayed.
to upload the new certificate. A pop-up window is displayed.
