Business roles map company structures with similar functionality that exist in addition to departments, cost centers, and locations. This might be projects groups, for example. Various company resources can be assigned to business roles. For example, authorizations in different SAP systems or Azure Active Directory tenants. You can add employees to single business roles as members. Employees obtain their company resources through these assignments when One Identity Manager is appropriately configured.
NOTE: The Business Roles Module must be installed as a prerequisite for managing business roles in One Identity Manager. For more information about installing, see the One Identity Manager Installation Guide.
The One Identity Manager components for managing business roles are available if the QER | Org configuration parameter is set.
The following users are used for the administration of business roles.
Table 1: Users
|
Business roles administrators |
Administrators must be assigned to the Identity Management | Business roles | Administrators application role.
Users with this application role:
-
Create and edit business roles.
-
Assign company resources to business roles.
-
Administrate application roles for role approvers, role approvers (IT), and attestors.
-
Set up other application roles as required. |
|
Business Role Attestors
|
Attestors must be assigned to the Identity Management | Business roles | Attestors application role or a child application role.
Users with this application role:
NOTE: This application role is available if the module Attestation Module is installed. |
|
Business Role Approvers
|
Approvers must be assigned to the Identity Management | Business roles | Role approvers application role or a child application role.
Users with this application role:
|
|
Business Role Approvers (IT)
|
IT role approvers must be assigned to the Identity Management | Business roles | Role approvers (IT) application role or a child application role.
Users with this application role:
|
|
One Identity Manager administrators
|
administrator and administrative system users Administrative system users are not added to application roles.
administrators:
-
Create customized permissions groups for application roles for role-based login to administration tools in the Designer as required.
-
Create system users and permissions groups for non role-based login to administration tools in the Designer as required.
-
Enable or disable additional configuration parameters in the Designer as required.
-
Create custom processes in the Designer as required.
-
Create and configure schedules as required. |
|
Additional managers |
The additional managers must be assigned to the Identity Management | Business roles| Additional managers application role or to a child application role.
Users with this application role:
|
Business role are arranged hierarchically. Assigned company resources are inherited by members through these hierarchies. Company resource assignments are not made to individual employees, devices or workdesks but centrally and then inherited automatically through a predefined distribution list.
Hierarchies can either be created following the top-down or the bottom-up model in One Identity Manager. In the top-down model, roles are defined based on the area of activity and the company resources required to fulfill the activities are assigned to the roles. In the case of the bottom-up model, company resource assignments are analyzed and the roles result from this.
The direction of inheritance decides the distribution of company resources within a hierarchy. One Identity Manager basically recognizes two directions of inheritance:
-
Top-down inheritance
In One Identity Manager, top-down inheritance maps the default structure within a company. With its help, a company’s multilevel form can be represented with main departments and respective subdepartments.
-
Bottom-up inheritance
Whereas in top-down inheritance, assignments are inherited in the direction of more detailed classifications, bottom-up inheritance operates in the other direction. This inheritance direction was introduced to map project groups in particular. The aim being, to provide someone coordinating several project groups with the company resources in use by each of the project groups.
NOTE: The direction of inheritance is only taken into account in relation to the inheritance of company resources. The direction of inheritance does not have any effect on the selection of the manager responsible. The manager with a parent role is always responsible for all child roles.
The effect on the allocation of company resources is explained in the following example for assigning an application.
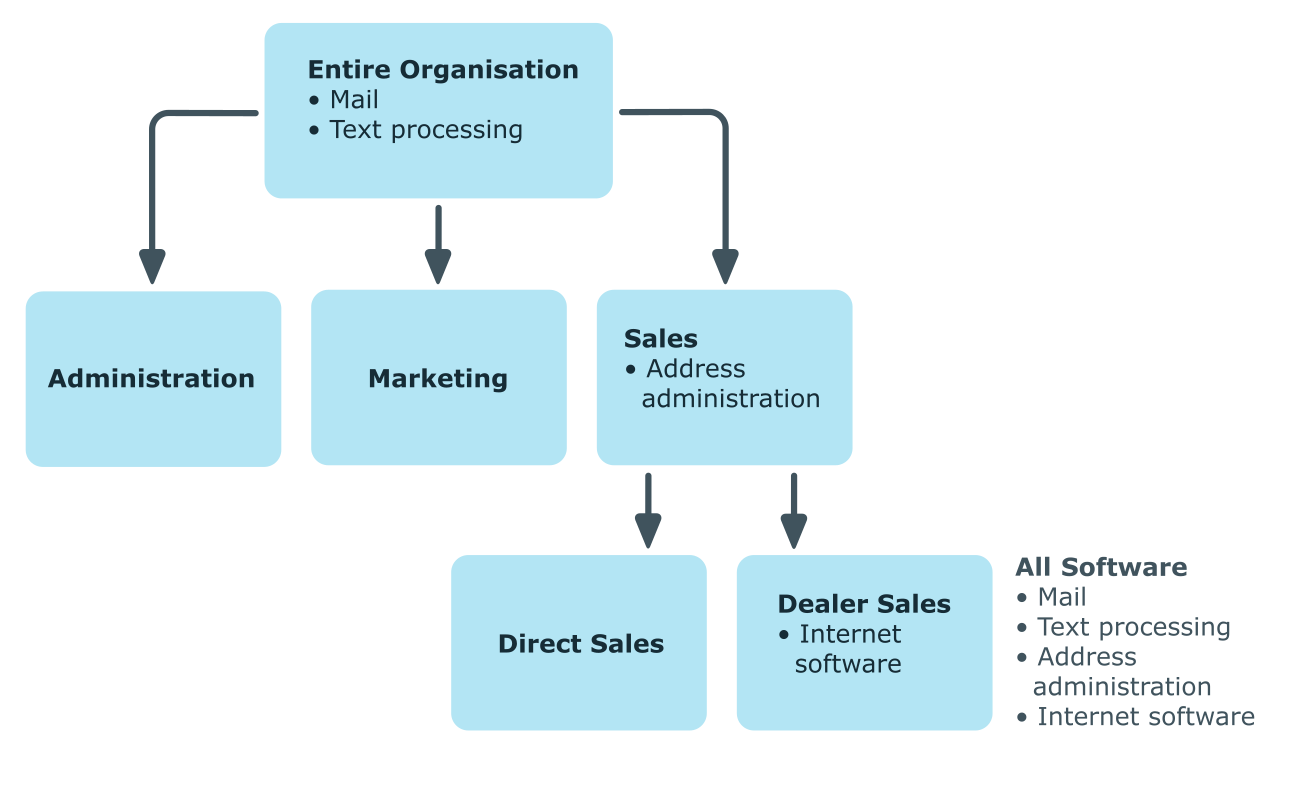
Example: Assigning company resources top-down
In the diagram above a section of a company’s structure is illustrated. In addition, software applications are listed that are assigned to the respective department. An employee in dealer sales is assigned all the software applications that are allocated to their department and all those on the entire organization path. In this case, they are email, text processing, address management and internet software.
Figure 1: Assignment through top-down inheritance
Example: Assigning company resources bottom-up
The next figure shows bottom-up inheritance based on a project framework. In addition, software applications are listed that are assigned to the respective project group. An employee from the "Project lead" project group receives software applications from the project group as well as those from the projects groups below. In this case, it is project management, CASE tool, development environment, assembler tool, and prototyping tool.
Figure 2: Assignment through bottom-up inheritance



