One Identity Manager offers simplified user account administration for Azure Active Directory. One Identity Manager concentrates on setting up and editing user accounts and providing the required permissions. To equip users with the required permissions, One Identity Manager maps subscriptions, service plans, groups, and administration roles. This makes it possible to use Identity and Access Governance processes, including attestation, Identity Audit, user account management and system entitlements, IT Shop, or report subscriptions for Azure Active Directory tenants.
One Identity Manager provides company employees with the user accounts required to allow you to use different mechanisms for connecting employees to their user accounts. You can also manage user accounts independently of employees and therefore set up administrator user accounts.
Additional information about the Azure Active Directory core directory, such as tenants and verified domains, is loaded into the One Identity Manager database by data synchronization. There are limited options for customizing this information in One Identity Manager due to the complex dependencies and far-reaching effects of any changes.
For more information about the Azure Active Directory structure, see the Azure Active Directory documentation from Microsoft.
NOTE: The Azure Active Directory module must be installed as a prerequisite for managing One Identity Manager in Azure Active Directory Module For more information about installing, see the One Identity Manager Installation Guide.
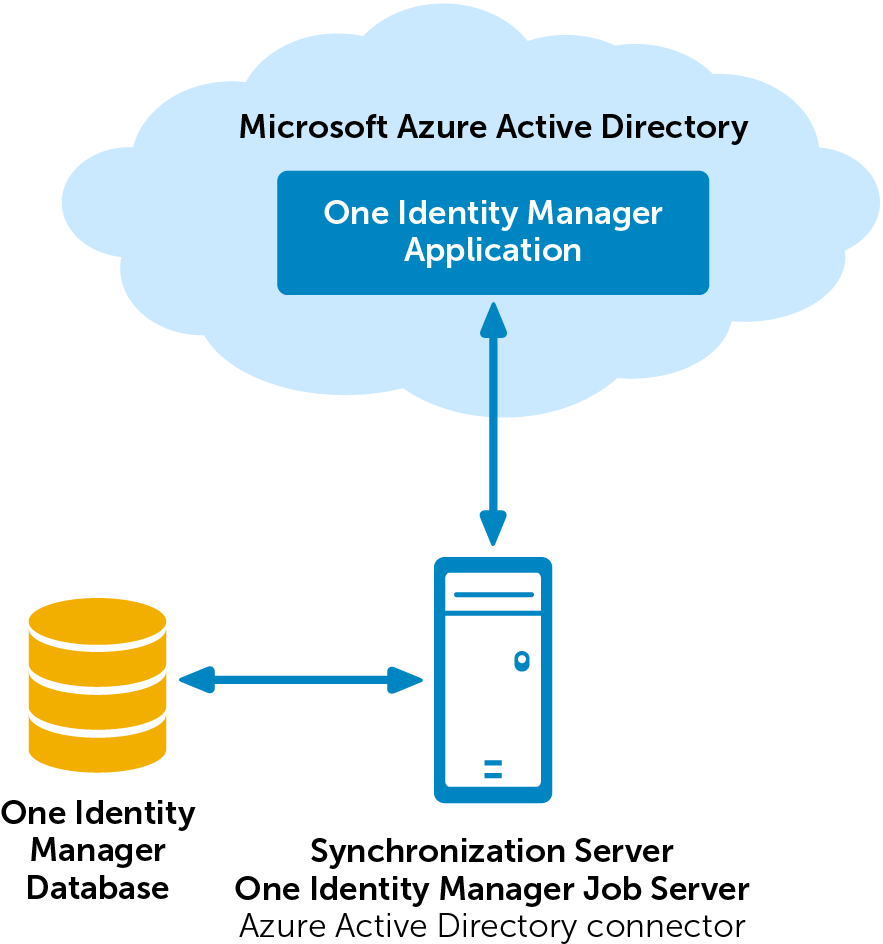
To access Azure Active Directory tenant data, the Azure Active Directory connector is installed on a synchronization server. The synchronization server ensures data is compared between the One Identity Manager database and Azure Active Directory. The Azure Active Directory connector uses the Microsoft Graph API for accessing Azure Active Directory data.
The Azure Active Directory connector must authenticate itself on the Azure Active Directory tenant to access Azure Active Directory tenant data. Authentication is carried out by an application for One Identity Manager that is integrated in the Azure Active Directory tenant and equipped with the respective access permissions.
Figure 1: Architecture for synchronization
The following users are involved in the administration of Azure Active Directory.
Table 1: Users
|
Target system administrators |
Target system administrators must be assigned to the Target systems | Administrators application role.
Users with this application role:
-
Administer application roles for individual target system types.
-
Specify the target system manager.
-
Set up other application roles for target system managers if required.
-
Specify which application roles for target system managers are mutually exclusive.
-
Authorize other employees to be target system administrators.
-
Do not assume any administrative tasks within the target system. |
|
Target system managers |
Target system managers must be assigned to the Target systems | Azure Active Directory application role or a child application role.
Users with this application role:
-
Assume administrative tasks for the target system.
-
Create, change, or delete target system objects.
-
Edit password policies for the target system.
-
Prepare groups to add to the IT Shop.
-
Can add employees who have another identity than the Primary identity.
-
Configure synchronization in the Synchronization Editor and define the mapping for comparing target systems and One Identity Manager.
-
Edit the synchronization's target system types and outstanding objects.
-
Authorize other employees within their area of responsibility as target system managers and create child application roles if required. |
|
One Identity Manager administrators |
administrator and administrative system users Administrative system users are not added to application roles.
administrators:
-
Create customized permissions groups for application roles for role-based login to administration tools in the Designer as required.
-
Create system users and permissions groups for non role-based login to administration tools in the Designer as required.
-
Enable or disable additional configuration parameters in the Designer as required.
-
Create custom processes in the Designer as required.
-
Create and configure schedules as required.
-
Create and configure password policies as required. |
|
Administrators for the IT Shop |
Administrators must be assigned to the Request & Fulfillment | IT Shop | Administrators application role.
Users with this application role:
|
|
Product owners for the IT Shop |
Product owners must be assigned to the Request & Fulfillment | IT Shop | Product owners application role or a child application role.
Users with this application role:
|
|
Administrators for organizations |
Administrators must be assigned to the Identity Management | Organizations | Administrators application role.
Users with this application role:
|
|
Business roles administrators |
Administrators must be assigned to the Identity Management | Business roles | Administrators application role.
Users with this application role:
|
Use configuration parameters to configure the behavior of the system's basic settings. One Identity Manager provides default settings for different configuration parameters. Check the configuration parameters and modify them as necessary to suit your requirements.
Configuration parameters are defined in the One Identity Manager modules. Each One Identity Manager module can also install configuration parameters. In the Designer, you can find an overview of all configuration parameters in the Base data > General > Configuration parameters category.
For more information, see Configuration parameters for managing an Azure Active Directory environment.

