When four-eyes authorization is required for a connection, a user (called authorizer) must authorize the connection on One Identity Safeguard for Privileged Sessions (SPS) as well. This authorization is in addition to any authentication or group membership requirements needed for the user to access the remote server. Any connection can use four-eyes authorization, so it provides a protocol-independent, out-of-band authorization and monitoring method.
The authorizer has the possibility to terminate the connection any time, and also to monitor real-time the events of the authorized connections: SPS can stream the traffic to the Safeguard Desktop Player application, where the authorizer (or a separate auditor) can watch exactly what the user does on the server, just like watching a movie.
NOTE: The auditor can only see the events if the required decryption keys are available on the host running the Safeguard Desktop Player application.
Figure 164: Four-eyes authorization
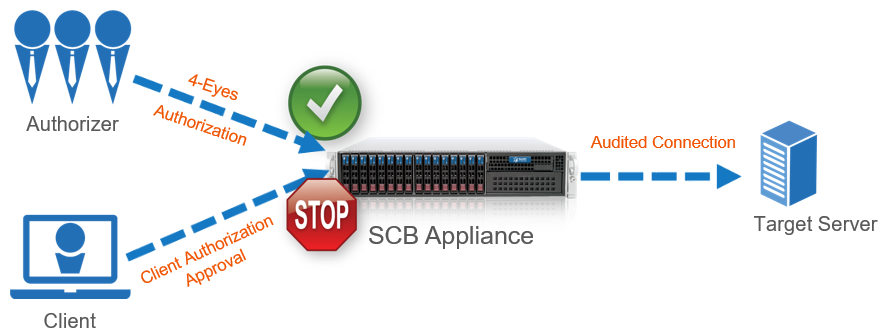
Technically, the process of four-eyes authorization is the following:
NOTE: Four-eyes authorization can be used together with other advanced authentication and authorization techniques like gateway authentication , client- and server-side authentication, and so on.
-
The user initiates a connection from a client.
-
If four-eyes authorization is required for the connection, SPS pauses the connection.
-
The authorizer logs in to the SPS web interface, selects the connection from the list of paused connections, and enables it.
-
The user performs the authentication on the server.
-
The auditor (who can be the authorizer, but it is possible to separate the roles) watches the actions of the user real-time.
