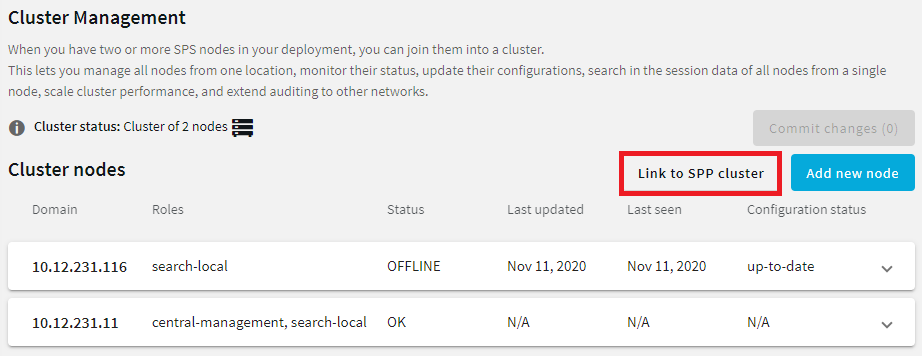
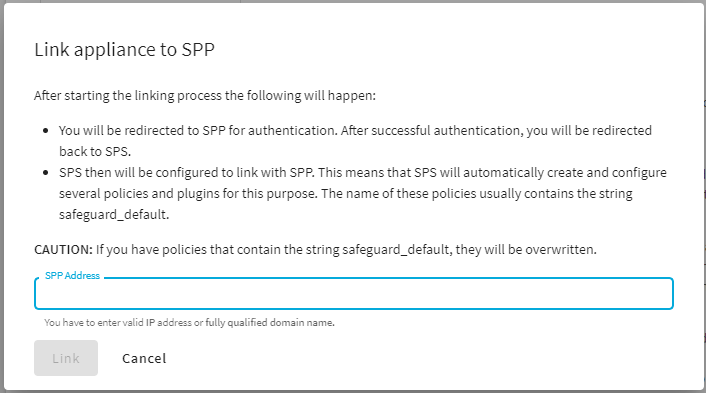
To configure SPP to use the linked SPS in Sessions-initiated (SPS-initiated) workflows, complete the following steps. For details on the workflow, see Using SPS with SPP.
Prerequisites
-
Minimum versions:
-
SPP version 2.8
-
SPS version 6.2 and newer, including 6.0.2 and newer versions of the 6.0.x branch, but excluding 6.1.x
-
-
You must have built an SPS cluster by promoting an SPS node to the role of the Central Management node, even if it is a single node. For more information, see Creating a cluster.
|
|
CAUTION: When linking your One Identity Safeguard for Privileged Sessions (SPS) deployment to your One Identity Safeguard for Privileged Passwords (SPP) deployment, ensure that the SPS and SPP versions match exactly, and you keep the versions synchronized during an upgrade. For example, you can only link SPS version 6.6 to SPP version 6.6, and if you upgrade SPS to version 6.7, you must also upgrade SPP to 6.7. Make sure that you do not mix Long Term Supported (LTS) and feature releases. For example, do not link an SPS version 6.0 to an SPP version 6.1. |
To configure SPP for Sessions-initiated workflow
-
On SPP, navigate to Administrative Tools > Settings > Session Management.
-
Click Session Module Password Access Enabled to enable this feature. A dialog opens.
-
Type Enable.
-
Ensure that SPP can access the usernames that will authenticate on the SPS gateway either from a local user database, or from an Active Directory.
-
Ensure that these users have the proper Entitlements to access the passwords to their target servers. Otherwise, SPS will reject their sessions.