You can authenticate a password by performing the following steps.
NOTE: This example assumes the system is configured using default settings, Safeguard Authentication Services is configured from a default install/join; and, the user is Safeguard Authentication Services-enabled with a password.
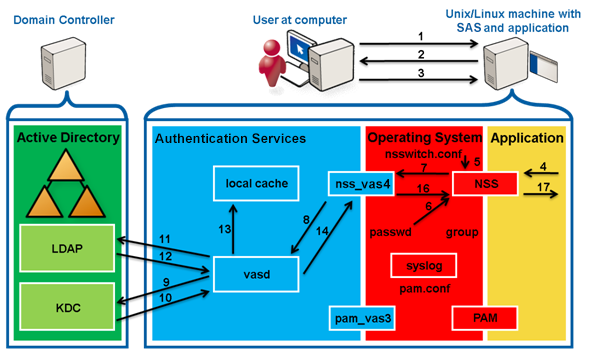
To authenticate a password
-
The user opens a secure connection with the application.
-
The application sends a prompt for the user name.
-
The user sends their user name to the application.
-
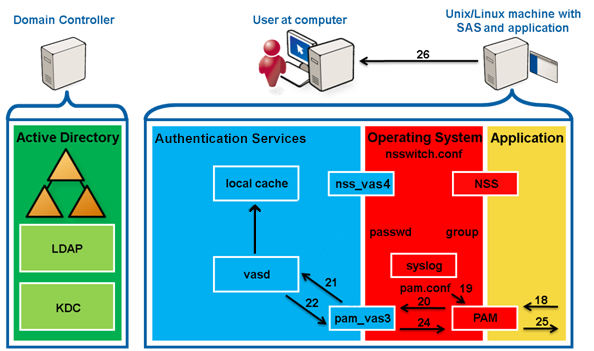
The application queries NSS (using getpwnam) about the user.
-
NSS reads /etc/nsswitch.conf and processes the passwd: files vas4 entry.
-
NSS queries nss_files, which reads /etc/passwd, and returns ENOENT because no matching user entry is found.
-
NSS queries nss_vas4.
-
nss_vas4 sends an IPC to vasd to update the user.
-
vasd uses credentials from the keytab to request a ticket to talk to the LDAP/<DC> service in Active Directory.
-
AD KDC returns the requested service ticket.
-
vasd queries AD LDAP for the user information.
-
The user’s information is returned.
-
vasd writes the user information into the local cache.
-
vasd returns the information about the user to vas_nss.
-
nss_vas4 forms the data into a passwd-stlye response.
-
nss_vas4 returns the passwd info to NSS.
NOTE: There is no password hash since vasd does not have access to that unless you are using a legacy auth setup.
-
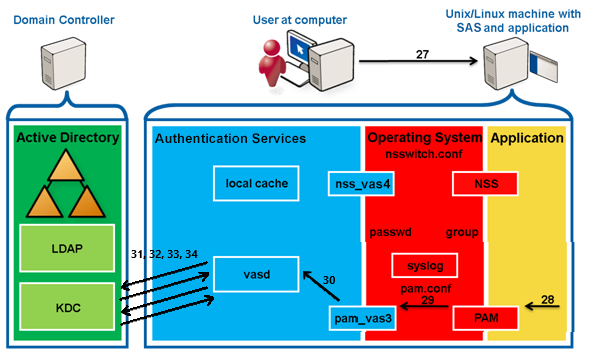
NSS returns the information to the application.
-
The application calls PAM through pam_start then pam_authenticate.
-
PAM reads /etc/pam.conf or the config file relevant to the service from /etc/pam.d and processes the pam_vas3 entry.
-
PAM queries pam_vas3.
-
pam_vas3 asks vasd for the user info.
-
vasd returns the user info from the local cache.
-
The user is a Safeguard Authentication Services user, therefore pam_vas3 will continue to attempt to authenticate the user instead of ignoring and letting the PAM stack fall past pam_vas3.
-
pam_vas3 returns a request for credentials (password) using PAM conversations (including the prompt to use).
-
PAM returns the request to the requesting application.
-
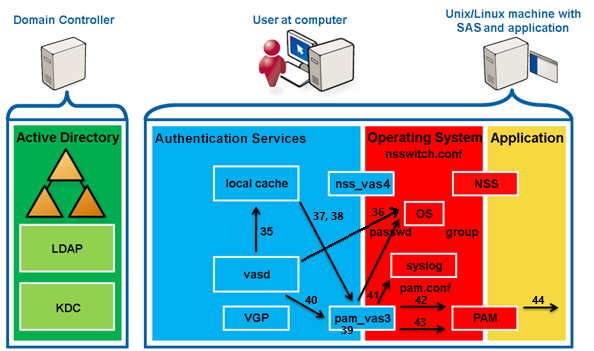
The application presents the user with the prompt for their password. (If the application is PAM conversation-aware, it uses the prompt pam_vas3 set).
-
The user enters their password.
-
The application passes the password to PAM.
-
The password is passed back to pam_vas3 through the conversation mechanism.
-
pam_vas3 sends the password to vasd through a secure IPC asking for authorization.
-
vasd requests a Kerberos TGT (Ticket Granting Ticket) for the user using a user key derived from the user’s samaccountname@realm and the supplied password.
NOTE: Kerberos does not actually use passwords; it uses keys derived from them for security.
-
AD KDC returns the TGT (AS-REP).
-
vasd decrypts the response using the user key, obtaining a TGT and Session key. TGT and Session key are used to request a service ticket (TGS-REQ) from the AD KDC for the user to authenticate against the host/ (local machine) service.
-
The AD KDC returns the service ticket (TGS-REP), which is decrypted using both the Session key (user portion) and the host/ key (service portion) that is stored in the host.keytab file.
-
vasd processes the payload of the service portion of the service ticket, which is the PAC (Privileged Access Certificate), a list of SIDs of groups of which the user is a member and modifies the local cache to set the current group memberships.
-
vasd creates the user's home directory if needed.
-
vasd reads the user account information from the local cache. It verifies the user is within any configured logon hours and has a valid shell (not /bin/false in AD).
-
vasd verifies the user's group membership information and confirms that the user has access based on any configured access control.
-
vasd performs UID and GID conflict checking.
-
vasd returns success to pam_vas3.
-
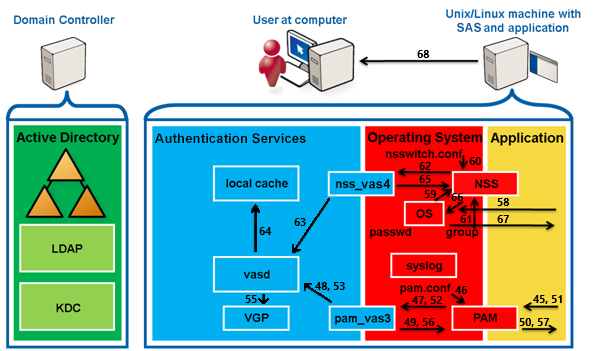
pam_vas3 writes a syslog entry that the authentication succeeded.
-
pam_vas3 sets a PAM stack variable to note that it has already processed the above.
-
pam_vas3 pam_authenticate returns PAM_SUCCESS.
-
Because the pam_vas3 entry is configured with sufficient, PAM_SUCCESS is returned to the querying application, ignoring the rest of the PAM stack.
-
The application calls PAM through pam_setcred and PAM_ESTABLISHED_CRED.
-
PAM reads /etc/pam.conf and processes the pam_vas3 entry.
-
PAM queries pam_vas3 for pam_sm_setcred.
-
pam_vas3 asks vasd to store the user's TGT and host/service ticket a local file-based cache for the user to use again if desired.
-
pam_vas3 returns PAM_SUCCESS.
-
PAM returns PAM_SUCCESS to the application for both calls.
-
Similarly, the application calls PAM through pam_open_session.
-
PAM queries pam_vas3.
-
pam_vas3 asks vasd through the IPC to create a login session for the user.
-
vasd fills the ~<user>/.vas_logon_server file with the server name.
-
vasd runs VGP to apply any user policies if configured so.
-
pam_vas3 returns PAM_SUCCESS to PAM.
-
PAM returns PAM_SUCCESS to the application.
-
The application starts the user's shell, which then sets up their environment.
-
The OS/shell calls NSS getgroups for the user's group memberships.
-
NSS reads /etc/nsswitch.conf and processes the group: files vas4 entry.
-
NSS queries nss_files, which reads etc/group and adds no groups if no local groups contain the user.
-
NSS queries nss_vas4.
-
nss_vas4 queries vasd to compute the user's group memberships.
-
vasd reads the group memberships from the local cache and returns them.
-
nss_vas4 returns the memberships to NSS.
-
The shell uses the groups to set the process space group memberships.
-
The OS presents the shell to the application.
-
The application presents the shell to the user, and they are now logged in.