Mounting an alternate share at login
If you cannot use the shares specified in Profile Path or Home Folder for some reason (for example, if your Windows home shares are DFS shares), you can specify an alternate share at join time by specifying a network home path expression.
To specify a network home path expression
- From the Join Domain dialog, click the disclosure triangle to expand the dialog.
- Select the User Home Config tab to display the home folder mounting options.
-
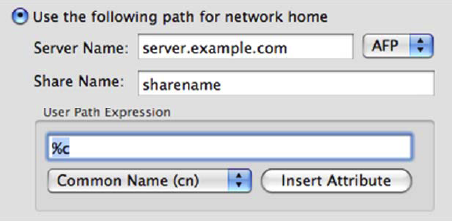
Select Use the following path for network home and enter the Server Name and Share Name to be used.
Selecting this option configures the network home for all users on the machine. Because of this you must specify how the path name will be resolved for each user.
- Under User Path Expression, use the drop-down and Insert Attribute button to specify the appropriate user attributes in the path portion of the server URL.
For example, if you selected Common Name (cn) and then clicked Insert Attribute, the expansion macro for Common Name (%c) is inserted into your path expression. The path expression may have text and expansion macros, or it may just be a single expansion macro with no other text.
Configure automatic home folder mounting using Group Policy
During deployment, installation and join usually happen in a scripted fashion from the command line. It is still possible to configure home folder mounting without using the graphical join interface, either through modification of the vas.conf file or by setting the appropriate options in group polices that apply to your macOS machines.
The two options that have bearing upon home directory mount behavior are nethome and nethome-mount-protocol. These options are set in the vas.conf policy.
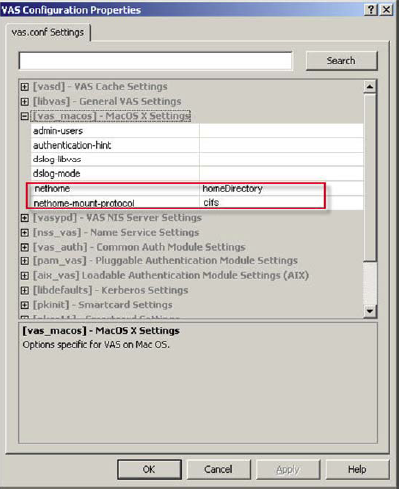
The nethome is either the name of the user attribute where the UNC path is stored ("homeDirectory" or "profilePath"), or it is the server URL expression for all users (that is, cifs://servername/sharename/%c).
If the nethome is specified as an attribute name, you can specify whether the path is mounted by means of AFP or CIFS using the nethome-mount-protocol setting.
Setting either of these options has no effect on any Safeguard Authentication Services platform other than macOS, so you can safely set it on a domain-wide Unix settings policy. Creation or modification of group policies is accomplished using the Microsoft GPOE on any Windows administrative workstation.
Group permissions on auto-mounted home directories
For Safeguard Authentication Services to resolve to a Windows SID to a Unix UID or GID, the user or group to whom that SID belongs must have had a UID or GID manually assigned to them. Or, in other words, you must Unix-enable the user or group on the Unix Account tab in Active Directory Users and Computers. If a group or user has not been Unix-enabled, the macOS machine will still assign a UID or GID to the user or group, but the Safeguard Authentication Services agent software will not be able to resolve the a UID or GID.
To log in to a macOS machine, all users must be Unix-enabled so this normally only causes problems when dealing with group permissions on SMB-mounted home directories. It is not uncommon for the group owner of a network home location to be a group WITHOUT a Unix GID assigned. When a user's ability to access this directory relies on correct group membership, problems can arise. It is, therefore, best practice to Unix-enable all groups that are used for SMB File level permissions on network mounted home directories.
Mounting AFP shares
To mount AFP shares, you must have an AFP file server that knows about all your Active Directory users and credentials. You can easily accomplish this using third-party software that shares files from a Windows machine joined to your domain.