Configuring Defender AD FS
Configuring Defender AD FS Adapter
This section provides the procedure that you must follow to configure Defender AD FS Adapter.
To configure Defender AD FS Adapter
- On the computer where the Defender AD FS Adapter is installed, run the Defender AD FS Adapter Configuration tool.
NOTE: Configuration is required for all installations of AD FS servers in the farm. - In the dialog box that opens, specify the Defender AD FS Adapter settings, and then click OK.
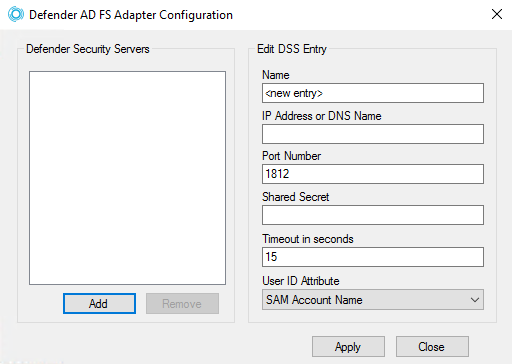
The dialog box looks similar to the following:
- Use this area to set up a list of the Defender Security Servers to which you want the Defender AD FS Adapter to connect.
- Add Adds a new entry to the Server list. After adding a new entry, edit the properties of the server added in the Edit DSS Entry area.
- Remove Removes the selected entry from the list.
- Edit DSS Entry Use this area to specify or edit the name, address, port number, and shared secret of the Defender Security Server to which you want the Defender AD FS Adapter to connect.
- Name Type the name of the Defender Security Server you want to use for user authentication.
- Address Type the IP address of the Defender Security Server.
- Port Type the communication port number configured on the access node you want the Defender AD FS Adapter to use. The default value is set to 1812.
- Shared Secret Type the shared secret configured on the access node you want the Defender AD FS Adapter to use.
- Timeout in seconds Specify the default timeout value in seconds. The default timeout is set to 15 seconds.
- User ID Attribute Select the name of the attribute containing the user ID used to authenticate. User ID value must match with DSS Access Node. The default value is set to SAM Account Name.
Enable LDAP over SSL
Enabling LDAP over SSL enables communication with the Active Directory server.
|
|
NOTE: Enabling LDAP over SSL is required for all installations of AD FS servers in the farm. |
To enable LDAP over SSL for communicating with Active Directory server
On a computer where Defender AD FS Adapter is installed, create the following value in the "HKEY_LOCAL_MACHINE\SOFTWARE\One Identity\Defender\AD FS Adapter" registry key using the Registry Editor:
- Value type: REG_DWORD
- Value name: LdapOverSsl
- Value data: 1
Configuring AD FS Multi-factor Authentication
This section provides information on the configuration of AD FS Multi-factor Authentication on the operating systems listed below.
Windows Server 2012 R2
To configure AD FS Multi-factor Authentication
- Launch the AD FS Management console on the primary AD FS internal server.
-
Navigate to AD FS | Authentication Policies, and click Edit Global Multi-factor Authentication. Alternatively, under Multi-factor Authentication | Global Settings section, click Edit.
-
In the Edit Global Authentication Policy window, click Multi-factor.
-
In Users/Groups section, click Add and select a domain for MFA (for example, Domain Users).
NOTE: The Users or the Groups must be a member of Defender Access Node. -
In the Location section, select Extranet and/or Intranet check boxes depending on the required type of connection.
For example, if you always require two-factor authentication, select both Extranet and Intranet when configuring the multi-factor authentication policy. If you want to enforce two-factor authentication for external users, and if you have configured your network such that external users communicate with an AD FS Web Application Proxy while internal users communicate with the Identity Provider, select only Extranet.
-
Select One Identity Defender AD FS Adapter authentication method to enable multi-factor authentication using Defender.
NOTE: In an advanced multi-factor scenario, you can select Intranet and/or Extranet for each user or for each relying party. For more information, see the Microsoft’s TechNet article Overview: Manage Risk with Additional Multi-Factor Authentication for Sensitive Applications.