When the YubiKey tokens you have purchased are in the OATH-HOTP mode, to enable their use with Defender you need to import the YubiKey token objects into Active Directory by using the .txt import file (also known as the key file) containing token object definitions. Then, you can assign the imported token objects to users as necessary.
Normally, the .txt import file is provided together with the YubiKey tokens. Before importing token objects, you need to modify the .txt import file so that Defender can read its contents.
To enable the use of YubiKey working in OATH-HOTP mode
- Change the file name extension of the .txt import file to .csv.
- Open the .csv file in Microsoft Excel. The .csv file looks similar to the following:
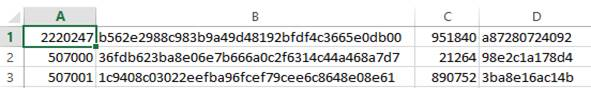
The columns in the file contain the following:
- A YubiKey serial number.
- B 160-bit secret set
- C Moving factor seed value.
- D Configuration password. Contains zeros if configuration password is not set.
- Delete column D.
- Save the .csv file. Now the file is ready for import.
NOTE: Keep the initial .txt file containing the passwords associated with each of the Yubikeys, to program the second slot though the Yubico interface later.
- Import token objects from the .csv file into Active Directory. For instructions, see Importing hardware token objects.
- Assign the imported YubiKey token objects to users as necessary. For instructions, see Assigning a hardware token object to a user.
Defender6.6.0 version supports FIDO2 compatible hardware Yubikey.
- A FIDO2 token
- Can be used for authentication only in ISAPI clients.
- Can be programmed through Management Portal only.
- Cannot be created as a placeholder Token; it is required to program a FIDO2 token to a specific User.
-
It cannot be assigned or unassigned from a user like other tokens because of FIDO2 protocol security.
-
If user’s hardware key is stolen/broken, it can be deleted from Management Portal.
-
FIDO2 tokens will have priority during authentication if multiple other types of Tokens are assigned to user.
-
FIDO2 tokens will have priority while authentication if multiple other types of Tokens are assigned to user.
- A maximum of 12 FIDO2 tokens can be programmed for a single user.
- FIDO2 cannot be programmed using management shell and ADUC.
To Program a FIDO2 Token
-
Open Management Portal, Go to Management Tab and under Users Tab, Search for User to whom you want to assign FIDO2 token.
-
Click on Program option; A window pop up will appear with different options of Software and Hardware Tokens.
-
Choose Hardware Tab and select FIDO2 option and click Program Token.
-
Another window pop-up will appear for user to enter FIDO2 token name:
-
Should be at least four characters.
-
Special character and space are not allowed.
-
Underscore(_) is allowed.
-
Maximum length should be 40 characters.
-
Click on Request and window will display success message.
-
FIDO2 token will appear in assigned token list of user with unique ID.
Operations on FIDO2 Token in Management Portal
-
Each FIDO2 token can be managed from assign token list of user using Manage button next to the token.
-
On clicking Manage, a window will appear with two tabs named EDIT and DELETE.
-
If user chooses EDIT, he can change the name of FIDO2 token.
-
If user chooses DELETE, he can delete the assigned FIDO2 token.

