Reporting is available only in Safeguard Privilege Manager for Windows Professional Edition or an active Professional Evaluation Edition. Once your trial evaluation license expires, reporting no longer collects data, and no longer generates reports.
Detailed information about this topic
Temporary Session Elevation Request Report
Temporary Session Elevation Usage Report
Advanced Policy Settings Report
Using the Applied Filters Wizard
You can build five types of reports on activities from client computers:
-
Blacklist Activity Report: Lists how frequently a rule is used.
-
Rule Deployment Report: Lists rules deployed on the client computer.
-
Instant Elevation Report: Lists processes that are elevated using Instant Elevation.
-
Rule Details Report: Lists rules that are configured.
-
Advanced Policy Settings Report: Lists Advanced Policy Settings, except those set to the Not Configured option.
In addition to these out of the box reports, you can create custom reports using third-party tools to query the SQL-based Safeguard Privilege Manager for Windows reporting database. Use this database schema to create your own custom reports or data analysis:
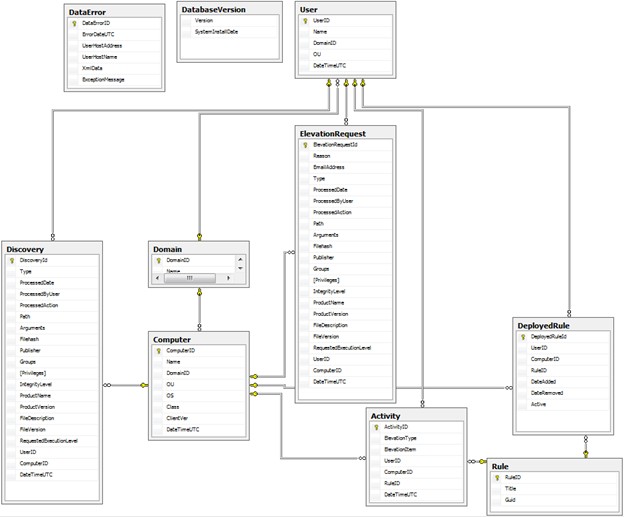
A PAReporting database is created when you set up the server and is configured to work with the ScriptLogic PA Reporting Service, the data collection web service running on a Console host.
Before you generate reports, ensure the following components are set up
-
The Server is configured and you can successfully join the data collection web service running on it.
-
Client data collection settings are configured for the GPOs you will report on. You can generate reports on GPOs for which you have read/write access in Windows.
To learn how to create this type of report and manage the data, see Generating and using reports.
