In the Manager, you can obtain an overview of all the dynamic roles with conflicting entries in the exclude list. This means that for at least one item in the list the following applies:
-
The dynamic role condition does not apply.
For example, this might occur if the dynamic role condition was changed after a person was entered in the exclude list.
- OR -
-
The excluded person is also assigned to the role in another way
such as through inheritance or direct assignment.
Check these entries and correct the assignments.
To check conflicting entries of business roles in the exclusion list
-
In the Manager, select the Business Roles > Troubleshooting > Dynamic roles with potentially incorrect excluded employees category.
-
Select the dynamic role in the result list.
-
Select the Exclude employees task.
In the exclusion list you can see which employees are affected by the given conditions.
For more information about editing the dynamic roles' exclusion list, see the One Identity Manager Identity Management Base Module Administration Guide.
Related topics
One Identity Manager makes various reports available containing information about the selected base object and its relations to other One Identity Manager database objects. The following reports are available for business roles.
NOTE: Other sections may be available depending on the which modules are installed.
Table 16: Reports about business roles
|
Overview of all assignments |
This report finds all the roles in which employees from the selected business roles are also members. |
|
Show historical memberships |
This report lists all members of the selected business role and the length of their membership. |
|
Show products still to be approved |
The report shows all products for a business role whose requests can be approved by the business role's members. |
|
Business roles with high risk level |
The report lists all business roles with a risk index equal or higher that the configurable risk index. The result can be limited to a specified role class. You can find this report in the My One Identity Manager category. |
Related topics
Business roles can be formed in two ways:
Analyzer uses the One Identity Manager program to make its own tools available for analyzing user accounts and permissions. The Analyzer supports analysis of business roles as well as the analysis of data quality with respect to the question: how well suited is the permissions data to partially automated role mining?
The Analyzer offers:
-
Automatic analysis of permissions assignments base on cluster analysis algorithms with different weighting.
-
Automatic analysis of existing structures and permissions of employees assigned in them
-
Manual analysis of certain staff groups for role mining
The aim of role mining is to replace direct permissions, which previously were only granted to users in individual application systems, with indirect ones. This allows permissions, which users obtain through role association to be defined across the application system. Analyzer’s aim is not only pure role mining but also classification of roles in a simple to administer hierarchical system. This can reduce the administration workload further and increase security for granting permissions.
To user role mining in One Identity Manager
NOTE: To use Analyzer for analyzing permissions, at least the Target System Base Module must be installed.
The basis for role mining is always a cluster analysis when the Analyzer with help of mathematical algorithm tries to find single clusters, meaning employees with similar permissions. In the process, either hierarchical structures are built or predefined structures are applied that can be used for constructing your own role model.
In role mining, you not only try to find single clusters and assign these to business roles, but you also try to develop direct hierarchical role structures that can then be effectively used through standard inheritance mechanisms.
Automatic role mining supports One Identity Manager through two different cluster analysis methods that differ in the way they calculate the distances between individual clusters. The use of existing role structures, for example, organizational structure from ERP systems, is possible. Permissions analysis can then be used to assign permissions to these role structures. Lastly, role structures can be freely defined and assignment of permissions and employees can be manually evaluated based on existing permissions.
Figure 14: Cluster analysis methods in the Analyzer
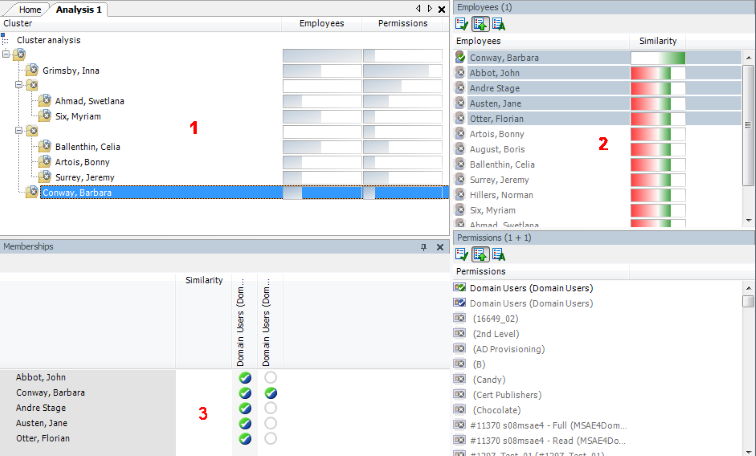
In clustering methods, Analyzer calculates a frequency distribution from user permissions in the different application systems, like Active Directory, HCL Domino, or SAP R/3. Certain permissions may have a higher weighting in comparison to others. The number of a permissions' members can, for example, represent this sort of criteria. This is acknowledged through the Analyzer during calculation and taken into account by weighting the distance between clusters. This allows the hierarchical structures arising from the analysis to be optimized in advance and the smallest possible number of roles to be attained.

