You can manually update the trusted certificates outside the configured period. For example, to retrieve a recently added trusted certificate, use the -f option with the vastool smartcard trusted-certs command, as follows:
vastool smartcard trusted-certs update -f
This command removes the existing certificates from the NtAuth subdirectory and retrieves all the current trusted certificates from Active Directory.
You can disable certificate bootstrapping and CRL downloading and distribute these items to Safeguard Authentication Services clients by other means, such as Group Policy.
To disable bootstrap and manage certificates and CRLs manually
- Set the auto-crl-download, auto-crl-removal and bootstrap-trusted-certs options to false in the [pkinit] section of the /etc/opt/quest/vas/vas.conf files, as follows:
[pkinit]
auto-crl-download = false
auto-crl-removal = false
bootstrap-trusted-certs = false
- Place the trusted certificates in the /var/opt/quest/vas/certs directory.
- Place CRLs in the /var/opt/quest/vas/crls directory.
The ability to lock the screen saver when a token is removed is a feature and function of the macOS screen saver.
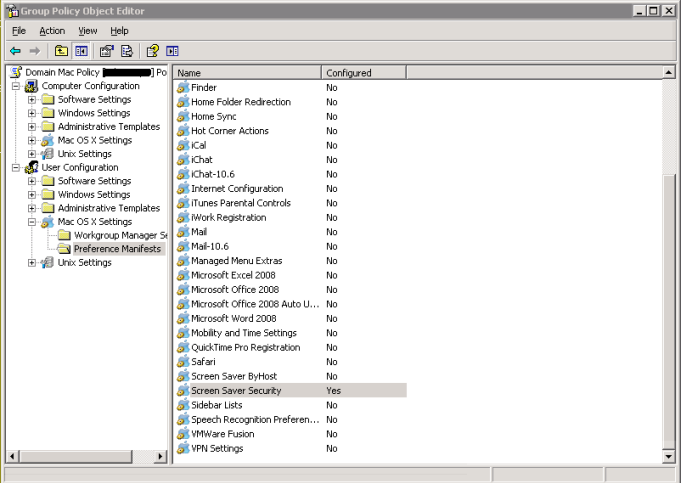
To enforce this setting using Mac OS X Group Policy
-
Navigate to User Configuration | Mac OS X Settings | Preference Manifests | Screen Saver Security from the Windows administrative machine that has the Safeguard Authentication Services components installed.
-
Set the following settings to ensure that the screen saver becomes locked and stays locked once the smart card is removed:
- Screensaver Require Password Delay: 0
- Require Password For Screensaver Unlock: 1
Testing Safeguard Authentication Services for Smart Cards
After you install and configure Safeguard Authentication Services for Smart Cards to work with your vendor's PKCS#11 library drivers, you will want to validate your installation.

