When synchronizing the central configuration across nodes, you may want to:
-
Keep certain parts in the configuration of individual nodes unchanged.
-
Customize certain parts of the central configuration to specific needs of individual nodes in the cluster (for example, your nodes may access external services through different network addresses).
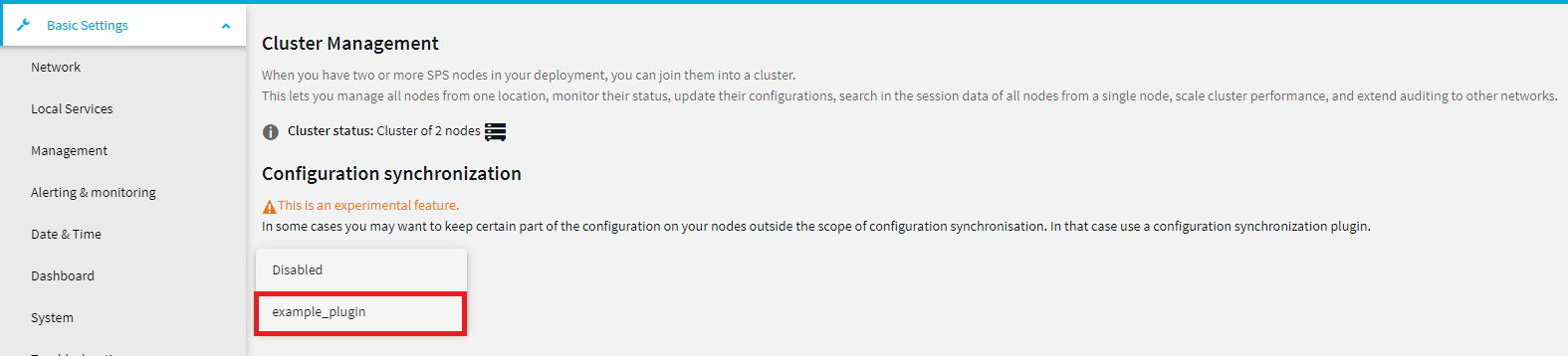
You can achieve all of these by using a configuration synchronization plugin that contains transformations for the problematic parts. The plugin only runs on nodes that have the Managed host role.
Customizing certain parts or features of a node using a configuration synchronization plugin has the same limitations as configuring One Identity Safeguard for Privileged Sessions (SPS) through the REST API. In other words, whatever you can configure through the REST API, you can configure the exact same settings using the plugin. One notable difference between the REST API and the plugin is that using the REST API, you can only read certain types of data (such as keys and passwords), while using the configuration synchronization plugin, you can write these types of data as well.
For details on how to configure SPS using the REST API, see REST API Reference Guide.
Data structures in the plugin are represented as nested JSON objects. For object references, the plugin uses keys.
The plugin works with the following key parameters:
- local_config: The current configuration of a Managed Host node (those parts that can be configured through the REST API).
- merged_config: The configuration of the Central management node that is about to be synced to the Managed host node (those parts that can be configured through the REST API), with settings related to networking, local services, and management whitelisted. These settings are never overwritten by configuration synchronization.
- node_id: The unique ID of the Managed host node in the cluster (you can retrieve this identifier by querying the /api/cluster/nodes endpoint through the REST API).
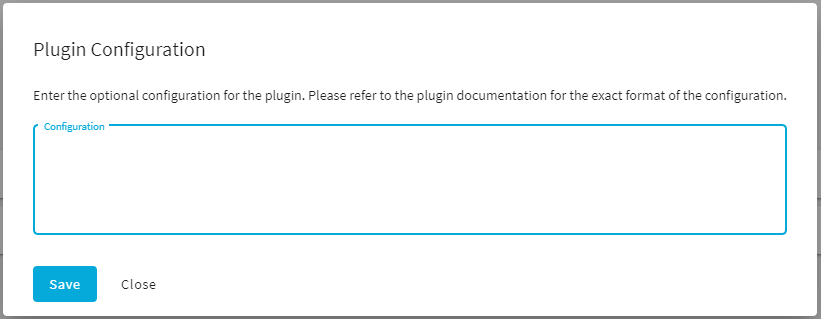
- plugin_config: The configuration of the plugin provided as free-form text. Specifying the configuration of the plugin is optional. It enables you to run configuration synchronization on each cluster with different parameters if you have multiple clusters.
Example: Customizing an IP address in a connection policy
For example, an RDP connection policy on a Managed host node specifies the following client and target addresses:
$ curl ... https://<url-of-Central-Management-node>/api/configuration/rdp/connections/<id-of-the-connection-policy>
{
"body": {
"network": {
"clients": [
"0.0.0.0/0"
],
"ports": [
3389
],
"targets": [
"10.30.255.28/24"
]
},
},
...
}
In the following example, an RDP connection policy is configured with the following details on the Central management node:
$ curl ... https://<url-of-Managed-Node>/api/configuration/rdp/connections/<id-of-the-connection-policy>
{
"body": {
"network": {
"clients": [
"0.0.0.0/0"
],
"ports": [
3389
],
"targets": [
"10.30.255.8/24"
]
},
},
...
}
To ensure that the details of the connection policy on the Managed host node are kept as-is after configuration synchronization, add the following lines to the plugin main.py file:
$ cat main.py
def merge(local_config: dict, merged_config: dict, node_id: str, plugin_config: str, **kwargs):
merged_config['rdp']['connections'][<id-of-the-connection-policy>]['network']['targets'][0] = "10.30.255.8/24"
return merged_config
Due to possible new (as yet undefined) parameters, it is good practice to close the parameter list of the merge function with **kwargs.
If you need assistance with writing customized transformations, contact our Professional Services Team, and a One Identity Service Delivery Engineer will help you.
NOTE: Configuration settings related to networking (Basic Settings > Network) and local services (Basic Settings > Local Services), with the exception of Safeguard for Privileged Analytics, are not overwritten on the nodes by configuration synchronization even if you are not using a plugin.
For the management of SPS (Basic Settings > Management), the following configuration settings are not overwritten:
-
Email settings
-
SSL certificates

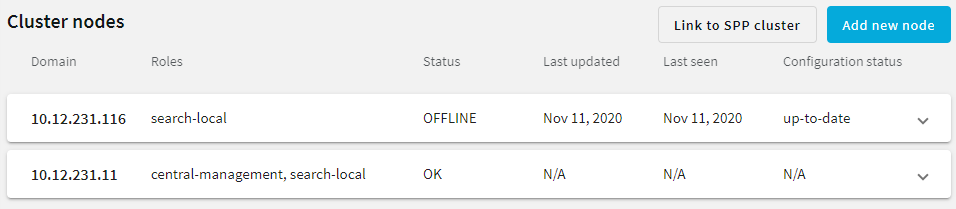
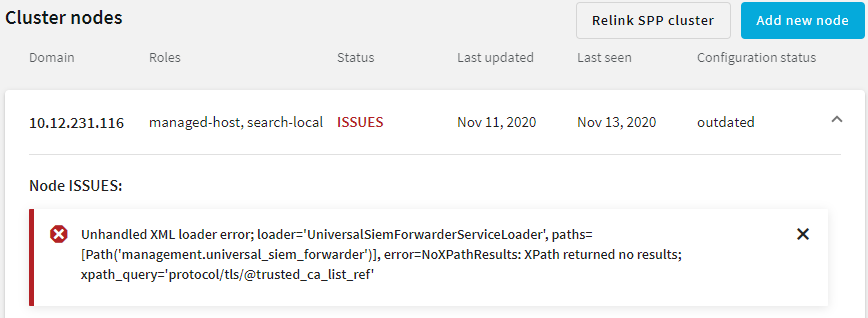
 on the row of the node that node that you want to update.
on the row of the node that node that you want to update.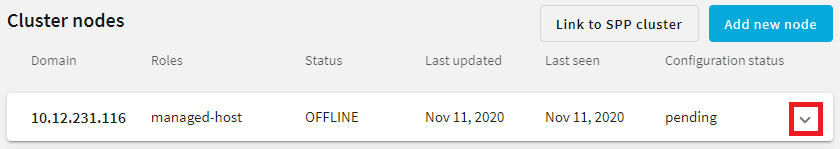
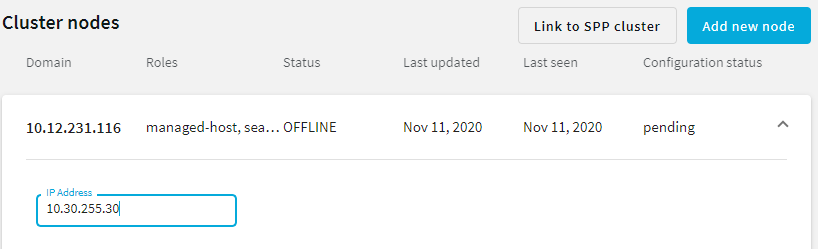

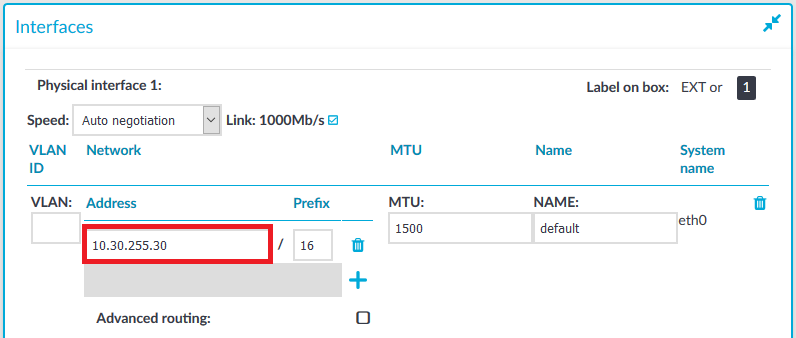
 .
.