Assigning assets or accounts to a password profile and SSH key profile
You can assign an asset or an account to a password profile, an SSH key profile, or both. The assets and accounts must be in the scope of the partition to be assigned to a profile.
You can also configure Safeguard for Privileged Passwords to run automatic Asset Discovery or Account Discovery jobs. For more information, see Discovery.
Only associate accounts to a profile that you want Safeguard for Privileged Passwords to manage. For example, a directory can be added to any partition as an asset and any profile can be assigned. If directory user accounts are associated with a profile, Safeguard for Privileged Passwords will automatically change the user passwords or SSH keys according to the change password schedule or change SSH key schedule in the profile. Depending on the settings, this could prevent a directory user from logging in to Safeguard for Privileged Passwords.
To add assets or accounts to a profile
- Navigate to Administrative Tools | Partitions.
- Select a partition from the object list and click the Password Profiles or SSH Key Profiles tab.
- Select a profile and click the
 Details icon.
Details icon.
- To add an asset to the selected profile, switch to the Assets tab of the profile's details window.
- Click
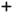 Add Asset.
Add Asset.
- On the Asset dialog, select the assets to be added.
- Click OK.
- To add an account to the selected profile, switch to the Accounts tab of the profile's details window.
- Click
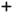 Add Account.
Add Account.
- On the Account dialog, select the accounts to be added.
- Click OK.
If you do not see the account you are looking for, it might be assigned to a different partition. If you have have Asset Administrator permissions to create assets and accounts, you can click 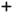 Create New to add an account. For more information, see Adding an account.
Create New to add an account. For more information, see Adding an account.
Modify a partition
To modify a partition
- Navigate to Administrative Tools | Partitions.
- In Partitions, select a partition from the object list.
-
Select the view of the partition's information you want to modify (General, Assets, Accounts, Profiles or SSH Key Profiles).
For example:
- To change a partition's name or description, or delegate partition management to a user, click the
 Edit icon.
Edit icon.
Note: You can also double-click a partition name to open the General settings edit window.
- To assign assets to the partition, open the Assets tab.
Note: You can multi-select items to assign more than one asset to a partition.
- To modify the password validation and reset settings, open the Password Profiles tab, select a profile, and click the
 Edit icon.
Edit icon.
- To modify the SSH key validation and rest settings, open the SSH Key Profiles tab, select a profile, and click the
 Edit icon.
Edit icon.
- To set the default partition, select the partition, then click
 Set as Default from the toolbar or context menu.
Set as Default from the toolbar or context menu.
- To view or export the details of each operation that has affected the selected partition, open the History tab. For more information, see History tab.
Delete a partition
When deleting a partition, you must designate another partition to transfers all assets and accounts. The profiles and associated profile settings, discovery jobs, and history data for the partition you are deleting are deleted along with the profile.
To delete a partition
- Navigate to Administrative Tools | Partitions.
- In Partitions, select a partition from the object list.
- Click
 Delete Selected.
Delete Selected.
-
In the Asset Partition dialog, select the partition where assets and accounts are to be reassigned.
- Click OK to reassign the assets and accounts and remove the selected partition.
Settings
 (web client) Settings
(web client) Settings
In the web client, click the  Settings menu on the left to go to the Settings page.
Settings menu on the left to go to the Settings page.
The following Settings are available. See each section for a description of the functions available.
 (desktop client) Settings
(desktop client) Settings
Using the desktop client, the Settings page in the  Administrative Tools is where you configure Safeguard for Privileged Passwords to run backups, install updates, manage clusters, manage certificates, enable event notifications, enable external integration, define profile configuration settings, define user password and SSH key rules, define discovery rules, and run troubleshooting tools.
Administrative Tools is where you configure Safeguard for Privileged Passwords to run backups, install updates, manage clusters, manage certificates, enable event notifications, enable external integration, define profile configuration settings, define user password and SSH key rules, define discovery rules, and run troubleshooting tools.
You must have administrator permissions to access the Settings page and the administrator permissions you have determine what you can do.
Use the Search control at the top of the Settings page to locate a particular setting. For example, if you type password and press the Enter key, a list of all the password settings appears; select an entry from this list to display the selected settings page.
The following Settings are available. See each section for a description of the functions available.
Details icon.
Add Asset.
Add Account.
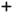

 Edit icon.
Edit icon.
 Set as Default from the toolbar or context menu.
Set as Default from the toolbar or context menu.
 Delete Selected.
Delete Selected.
 (web client) Settings
(web client) Settings Settings menu on the left to go to the Settings page.
Settings menu on the left to go to the Settings page. 






 (desktop client) Settings
(desktop client) Settings