You can set fixed values for function elements in authorization definitions. Otherwise, you can implement variables to use a function definition for different function instances. For this, the following is valid:
You can also use system variables as well as self-defined variables in the authorization definition. System variables have the following syntax: ${character}+ (example: $AUFART).
Variables must be uniquely identifiable by the authorization check. Therefore, names of self-defined variables may not match system variables or begin with system variable name.
Related topics
One Identity Manager uses this task to test whether all authorization objects that belong to an SAP application occur in the authorization definition.
To test an authorization definition for completeness
-
In the Manager, select the Identity Audit > SAP functions > Function definition working copies category.
-
Select the function definition in the result list.
-
Select the Authorization Editor task.
-
Select the Check authorization objects for completeness task.
Missing authorization objects are displayed in a separate window.
-
Enable the Add option on the authorization object you want to add to the authorization definition.
-
When all missing authorization objects are edited, click OK.
The authorization objects can now be edited in the authorizations editor.
Related topics
SAP authorizations are only checked on the basis of active SAP functions. When you enable the working copy, the changes are transferred to the function definition. An active function definition is added to a new working copy.
To transfer changes from a working copy to a function definition
-
In the Manager, select the Identity Audit > SAP functions > Function definition working copies category.
-
Select the function definition in the result list.
-
Select the Enable working copy task.
-
Confirm the security prompt with OK.
Related topics
SAP authorizations are verified on the basis of the SAP applications permitted for an SAP user account and the associated authorization objects. To determine whether potentially dangerous authorizations are assigned within the company, define SAP functions that group together the SAP applications and authorization objects to be checked. One Identity Manager compares all authorization objects assigned to single profiles with the authorization definition in the SAP function. This way, it determines all SAP roles and profiles that have exactly these authorization objects assigned via the sum of their single profiles.
The TargetSystem | SAPR3 | SAPRights | TestWithoutTCD configuration parameter is evaluated by authorization checks. The configuration parameter specifies whether SAP application are ignored and only authorization objects taken into account during the authorization check.
The TestWithoutTCD configuration parameter is not set (default)
The following rules apply to the authorization check:
An SAP role or SAP profile matches an SAP function when
-
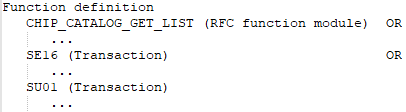
It has at least one of the SAP applications defined in the SAP function.
-
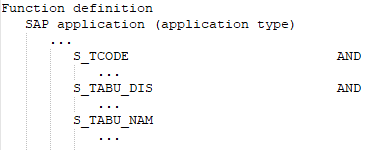
It has all the authorization objects of this SAP application that are defined in the SAP function.
-
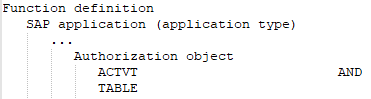
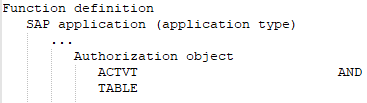
It has all the different function elements of an authorization object that are defined in the SAP function.
-
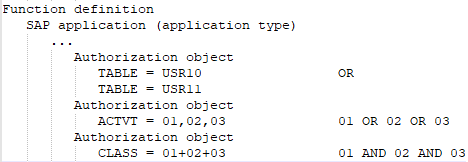
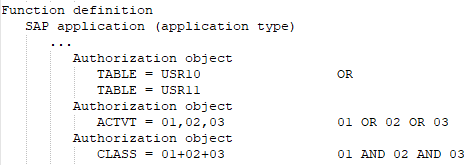
At least one or all of the values of one and the same function element defined in the SAP function are available.
An SAP role matches an SAP function if an SAP profile of this SAP role matches the SAP function.
An SAP profile matches an SAP function if it contains at least one of the SAP applications defined in the SAP function. The SAP profile must have all this SAP application's authorization objects to do this. If a function element with different values is defined for an authorization object, the SAP profile matches the SAP function if it has at least one of these values.
The TestWithoutTCD configuration parameter is set
SAP applications are not taken into account during the authorization check. The following rules apply to the authorization check:
An SAP role or SAP profile matches an SAP function when
-
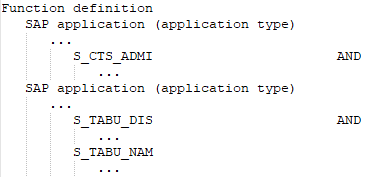
It has all the authorization objects of all SAP applications defined in the SAP function,
except for the authorization objects needed to identify the SAP applications.
-
It has all the different function elements of an authorization object that are defined in the SAP function.
-
At least one or all of the values of one and the same function element defined in the SAP function are available.
Only the authorization objects and their values are of interest for the authorization check. It is irrelevant to which SAP applications these authorization objects belong. That means the authorization objects that are only used to identify the applications are ignored. The following authorization objects and function elements are therefore disregarded:
-
External service: S_Service with SRV_NAME
-
TADIR object: S_START with AUTHOBJNAM, AUTHOBJTYP, and AUTHPGMID
-
RFC function module: S_RFC with RFC_NAME
-
Transaction: S_TCODE with TCD
Examples of authorization checking
An SAP function is defined with the following SAP applications, authorization objects, and function elements.
Figure 3: Authorization definition with transactions
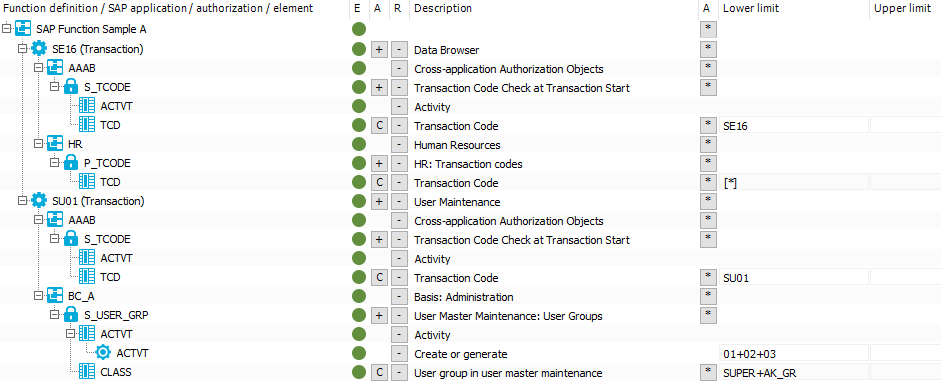
If the configuration parameter is not set, all SAP roles and SAP profiles with the authorizations found by the SAP function shown are listed here:
SAP application SE16 with:
Authorization object S_TCODE with
Function element ACTVT
AND
Function element TCD with the value SE16
AND
Authorization object P_TCODE with
Function element TCD with exactly the value *
OR
SAP application SU01 with:
Authorization object S_TCODE with
Function element ACTVT
AND
Function element TCD with at least the value SU01
AND
Authorization object S_USER_GRP with
Function element ACTVT with at least the values 01 AND 02 AND 03
AND
Function element CLASS with at least the value SUPER AND AK_GR
If the configuration parameter is set, all SAP roles and SAP profiles with the authorizations found by the SAP function are listed here:
Authorization object P_TCODE with
Function element TCD with exactly the value *
AND
Authorization object S_USER_GRP with
Function element ACTVT with at least the values 01 AND 02 AND 03
AND
Function element CLASS with at least the value SUPER AND AK_GR
The following function definition contains various SAP applications with different application types.
Figure 4: Authorization definition with different application types
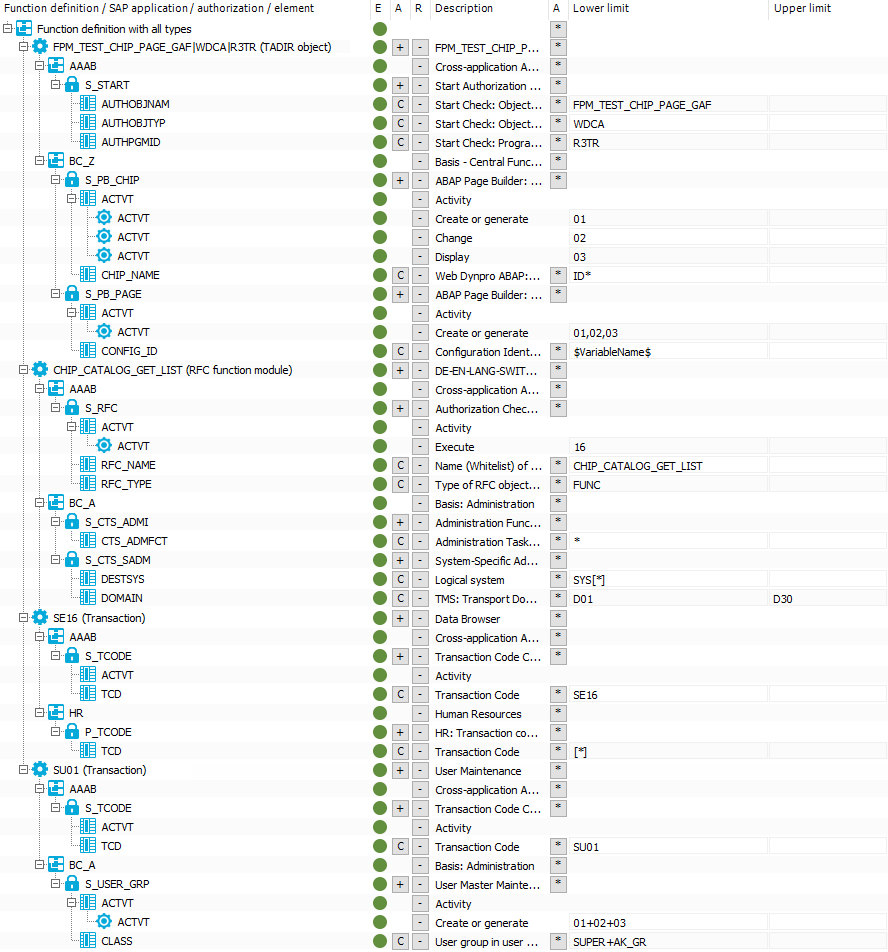
If the configuration parameter is set and without taking the SAP applications into account, the SAP function shown will determine all SAP roles and SAP profiles that have the following authorizations:
Authorization object S_PB_CHIP with
Function element ACTVT with at least one of the values 01 OR 02 OR 03
AND
Function element CHIP_NAME with an value that starts with ID
AND
Authorization object S_PB_PAGE with
Function element ACTVT with at least one of the values 01 OR 02 OR 03
AND
Function element CONFIG_ID with the instance that is specified as a value in the $VariableName$ variable
AND
Authorization object S_CTS_ADMI with
Function element CTS_ADMFCT with any value
AND
Authorization object S_CTS_SADM with
Function element DESTSYS with at least the value of exactly SYS*
AND
Function element DOMAIN with at least one value in a range from D01 to D30
AND
Authorization object P_TCODE with
Function element TCD with exactly the value *
AND
Authorization object S_USER_GRP with
Function element ACTVT with at least the values 01 AND 02 AND 03
AND
Function element CLASS with at least the value SUPER AND AK_GR
If the configuration parameter is not set, the SAP function shown will determine all SAP roles and SAP profiles with the authorizations. The evaluation at the level of the function elements is identical to the evaluation when the configuration parameter is set and is therefore not shown again.
SAP application FPM_TEST_CHIP_PAGE_GAF with:
Authorization object S_START
AND
Authorization object S_PB_CHIP
AND
Authorization object S_PB_PAGE
OR
SAP application CHIP_CATALOG_GET_LIST with:
Authorization object S_RFC
AND
Authorization object S_CTS_ADMI
AND
Authorization object S_CTS_SADM
OR
SAP application SE16 with:
Authorization object S_TCODE
AND
Authorization object P_TCODE
OR
SAP application SU01 with:
Authorization object S_TCODE
AND
Authorization object S_USER_GRP
Related topics









