When creating home folders, Active Roles operates in the security context of the service account under which the Administration Service is running. This means that the service account must have sufficient rights to create home folders. Normally, the service account has administrative rights on an entire file server, which enables Active Roles to create home folders in any folder on any network file share that exists on that server. To restrict Active Roles to create home folders only on a specific list of network file shares and folders, use the Home Folder Location Restriction policy.
The Home Folder Location Restriction policy determines the folders on the network file shares in which Active Roles is allowed to create home folders, and prevents Active Roles from creating home folders in other locations. The restrictions imposed by this policy do not apply if the home folder creation operation is performed by an Active Roles Admin role holder (normally, these are the users that have membership in the Administrators local group on the computer running the Active Roles Administration Service). Thus, when an Active Roles Admin role holder creates a user account, and a certain policy is in effect to facilitate home folder provisioning, the home folder is created regardless of the Home Folder Location Restriction policy settings.
By default, no network file shares and folders are listed in the policy. This means that Active Roles cannot create a home folder unless the user management operation that involves creation of the home folder is performed by the Active Roles Admin role holder. In order to allow delegated administrators to create home folders, you have to configure the policy so that it lists the folders on the network file shares in which creation of home folders is allowed.
For more information on configuring this Policy Object, see Configuring the Home Folder Location Restriction policy in the Active Roles Administration Guide.
Property Generation and Validation policies automate the configuration of directory object properties. You can configure these policies to:
-
Populate new directory objects with default property values (for example, when creating new user accounts or groups).
-
Validate the compliance of directory property values against corporate rules.
For example, you can configure a policy to enforce a certain type of telephone number formatting in the contact information properties for your directory.
Policy-controlled properties and default values
In the Object Creation Wizard and Properties dialogs, the properties that are controlled by the policy are displayed as hyperlinks.
Example: Default values configured for a property
If you have a policy configured to populate a property with a certain value (generate the default value), the property field is unavailable for editing, as you can see in the following example.
Figure 11: Object creation
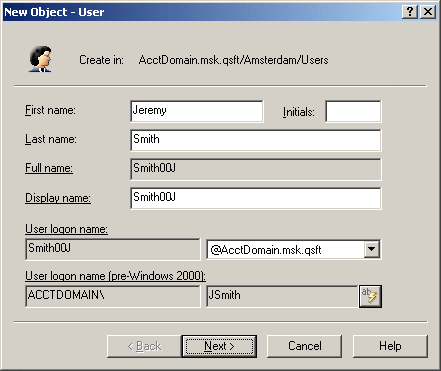
To display the policy details, click the hyperlink.
Policy-controlled acceptable values
With a policy that is configured to display only a set of acceptable values for a given property, the Active Roles Console displays a drop-down list of values when you modify that property. This saves the effort of having to type the value, or the issue of typing it incorrectly.
Example: Selecting acceptable values that are defined by a policy
In the following example, the Office drop-down displays a list of acceptable values that are prescribed by policy.
Figure 12: Acceptable values for a policy
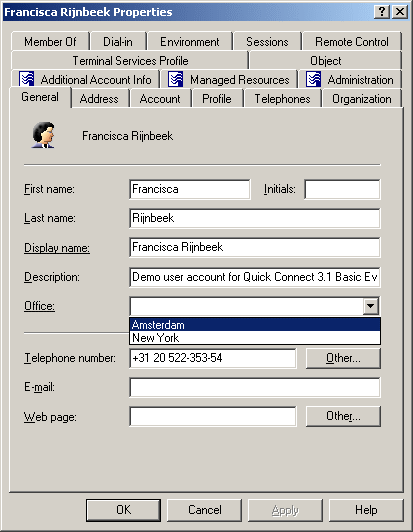
Property validation
When creating or modifying an object, Active Roles checks whether the property values satisfy the criteria that were defined in the policy. If they do not, Active Roles prevents you from creating or modifying the object.
For more information on configuring this Policy Object type, see Property Generation and Validation in the Active Roles Administration Guide.
Script execution policies help you to run supplementary PowerShell, or other script modules in Active Roles during or after performing certain administrative operations. When linking a custom script to an administrative operation via a Script Execution policy, the script will receive control in Active Roles either when the operation is requested or when it is completed.
Use Script Execution policies to set up custom scripts (residing in Script Modules in the Active Roles Console) to:
-
Trigger additional actions when performing directory object provisioning.
-
Regulate object data format and requirements (such as for generating user passwords).
-
Further automate administrative tasks.
Example use case for a Script Execution policy
Consider a scenario where employees of an organization are frequently transferred among its office branches temporarily due to various projects.
To administer such temporary assignments quickly and efficiently, write and apply a custom script that automatically reassigns the employee's user account from the OU of their original office to the OU of their new office, whenever their City or Office Location attributes are updated in Active Roles.
TIP: Consider the following when planning to use custom scripts for your provisioning policies:
-
To help you configure Script Execution policies, Active Roles also ships with several built-in Script Modules that you can use to set up your own Script Execution policies. Find these built-in Script Modules in the following node of the Active Roles Console:
Configuration > Script Modules > Builtin
-
If the directory of your organization contains any cloud-only Azure users, then use the built-in Generate User Password - Azure only script module to set up a password generation policy for cloud-only Azure users that meets the password strength criteria of both your organization and Microsoft Azure Active Directory (Azure AD).
For more information on configuring this Policy Object, see Configuring a Script Execution policy in the Active Roles Administration Guide.
O365 and Azure Tenant Selection policies help you:
-
Manage Azure tenant selection for Azure users, guest users, groups and contacts.
-
Microsoft 365 (M365) license and role selection.
-
OneDrive provisioning for hybrid Azure users in the Azure tenant.
This is a unified policy for Azure AD-specific and Microsoft 365 management, controlled or restricted by creating a new provisioning policy and applying the policy to the Organizational Unit.
For more information on configuring this Policy Object, see Configuring an O365 and Azure Tenant Selection policy in the Active Roles Administration Guide.


