Relayed authentication methods
For the server-side connection (between One Identity Safeguard for Privileged Sessions (SPS) and the target server), the following authentication methods are available.
NOTE: Even though these settings refer to the server-side connection, the client must support the selected authentication method and have it enabled. For example, to use publickey authentication on the server side, the client must support publickey authentication as well as provide a fake publickey, even if a different authentication method is used on the client side.
The Connection Policy will ignore the settings for server-side authentication (set under Relayed authentication methods for SSH protocol) if a Credential Store is used in the Connection Policy.
Figure 236: SSH Control > Authentication Policies — Configuring relayed authentication methods
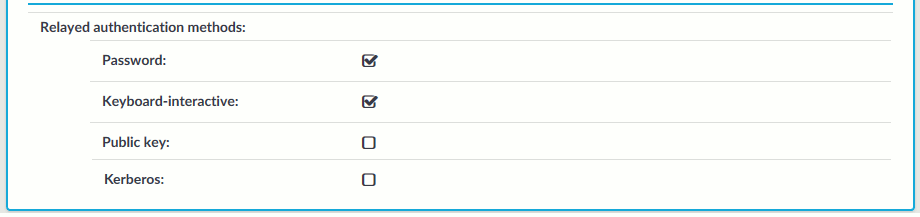
-
Password: Authentication based on username and password. The server will request a password from the user, even if a password-based authentication was already successful on the client-side.
-
Keyboard-Interactive: Authentication based on exchanging messages between the user and the server. This method includes authentication schemes like S/Key or TIS authentication. Note that depending on the configuration of the SSH server, password-based authentication can also require using the keyboard-interactive authentication method.
-
Public Key: Authentication based on public-private encryption keypairs. SPS supports the following public-key authentication scenarios:
-
Publish to LDAP: SPS generates a keypair, and uses this keypair in the server-side connection. The public key of this keypair is also uploaded to the LDAP database set in the LDAP Server of the connection policy. That way the server can authenticate the client to the generated public key stored under the user's username in the LDAP database.
-
Fix: Uses the specified private key in the server-side connection.
-
Agent: Allow the client to use agent-forwarding, and use its own keypair on the server-side.
During agent-forwarding, the following keys are accepted:
- rsa
-
ed25519
-
ecdsa-sha2-nistp256
-
ecdsa-sha2-nistp384
-
ecdsa-sha2-nistp521
If this option is used, SPS requests the client to use its SSH agent to authenticate on the target server. Therefore, you must configure your clients to enable agent forwarding, otherwise authentication will fail. For details on enabling agent forwarding in your SSH application, see the documentation of the application.
TIP: Some clients may override agent forwarding requests for SFTP and SCP by default. For further information about ensuring access to the server in this case, see Using SCP with agent-forwarding.
TIP: One Identity recommends using 2048-bit RSA keys (or stronger).
-
Kerberos: Authentication based on Kerberos. Only available if you selected Kerberos as the gateway authentication method. For more information, see Kerberos authentication settings.
Configuring your Kerberos environment
To integrate One Identity Safeguard for Privileged Sessions (SPS) with your Kerberos environment, so that your clients can authenticate on the target servers using Kerberos tickets, you have to configure your environment appropriately.
To configure your Kerberos environment
-
Configure your DNS server.
-
On your Domain Name Server (DNS), add SRV records that describe which Key Distribution Center (KDC) belongs to the domain. Add both TCP and UDP entries for each domain. For example, if your domain is example.com and the hostname of your KDC server is kdc.example.com, this entry looks like:
_kerberos._tcp.example.com 0 0 88 kdc.example.com
_kerberos._udp.example.com 0 0 88 kdc.example.com
-
If your environment uses multiple realms, repeat the previous step for every realm.
-
Verify that the servers that your clients will connect to via SPS have proper reverse-dns entries. Otherwise, your clients cannot access the target servers if you use the Inband destination selection feature of SPS.
-
Create a keytab file for SPS.
-
On your KDC server, create a principal for the SPS host, using the domain name of your SPS. For example:
host/scb.example.com@EXAMPLE.COM
-
If your environment uses multiple realms, repeat the previous step on the KDC of every realm.
-
Export the key of the principal into a keytab file.
-
If your environment uses multiple realms, merge the keytab files of the different realms into a single file, for example, using the ktadd or the ktutil utilities.
-
If your environment uses multiple realms, repeat the previous step on the KDC of every realm.
-
Configure the SSH application of your client hosts to enable Kerberos (GSSAPI) ticket forwarding. (In most applications this is disabled by default.)
Expected result
You have configured your environment to use Kerberos authentication with SPS, and created a keytab file for your SPS host. For details on uploading the keytab file and configuring SPS see Kerberos authentication settings.
Kerberos authentication settings
The following describes how to perform authentication with Kerberos. One Identity Safeguard for Privileged Sessions (SPS) supports both end-to-end Kerberos authentication, when the client authenticates on SPS gateway and on the target server using Kerberos, and also the half-sided Kerberos scenario when Kerberos is used only on the SPS gateway.
Prerequisites
Before configuring Kerberos authentication on One Identity Safeguard for Privileged Sessions (SPS), make sure you have configured your Kerberos environment correctly and have retrieved the keytab file. For details, see Configuring your Kerberos environment.
To perform authentication with Kerberos
-
Navigate to SSH Control > Authentication Policies.
-
Create a new Authentication Policy.
-
Select the authentication methods to use on the SPS gateway and on the target server.
-
To use Kerberos authentication on the target server, you must use Kerberos authentication both on the SPS gateway and on the target server. Select Gateway authentication method > Kerberos and Relayed authentication methods > Kerberos.
-
To use Kerberos authentication only on the SPS gateway (that is, in the client-side connection), select Gateway authentication method > Kerberos. If required, you can select other gateway authentication methods in addition to Kerberos, and also authentication backends and related to the selected gateway authentication methods.
Select the authentication methods you want to use on the target server in the Relayed authentication methods field.
-
Click  .
.
-
Navigate to SSH Control > Global Options > GSSAPI.
-
Browse for the Kerberos keytab file, and click Upload. The uploaded principals are displayed in Currently uploaded principals.
If a Connection Policy uses an SSH Authentication Policy with Kerberos authentication together with a Usermapping Policy, then SPS stores the user principal as the gateway user, and the target username as the server username in the session database. If you want to allow your users to use a username on the target server that is different from their principal, configure a Usermapping Policy for your SSH connections. For details, see "Configuring usermapping policies" in the Administration Guide.
Click  .
.
-
(Optional) If more than one realm is deployed on your network, you have to specify the mapping from the server's DNS domain name to the name of its realm. To map hostnames onto Kerberos realms, click  .
.
-
Navigate to SSH Control > Connections and configure the SSH connection as follows. For details on configuring connections in general, see Configuring connections.
-
Select Use fixed address or Inband destination selection as Target.
-
Select the Kerberos Authentication policy.
-
Click  .
.
Server host keys
The host keys of the trusted servers can be managed on the SSH Control > Server Host Keys page. When a client tries to connect to a server, One Identity Safeguard for Privileged Sessions (SPS) verifies the host key of the server. SPS allows connections only to the servers listed on this page, unless the Accept key for the first time or the Accept certificate for the first time option is enabled in the connection policy.
Figure 237: SSH Control > Server Host Keys — Server host keys
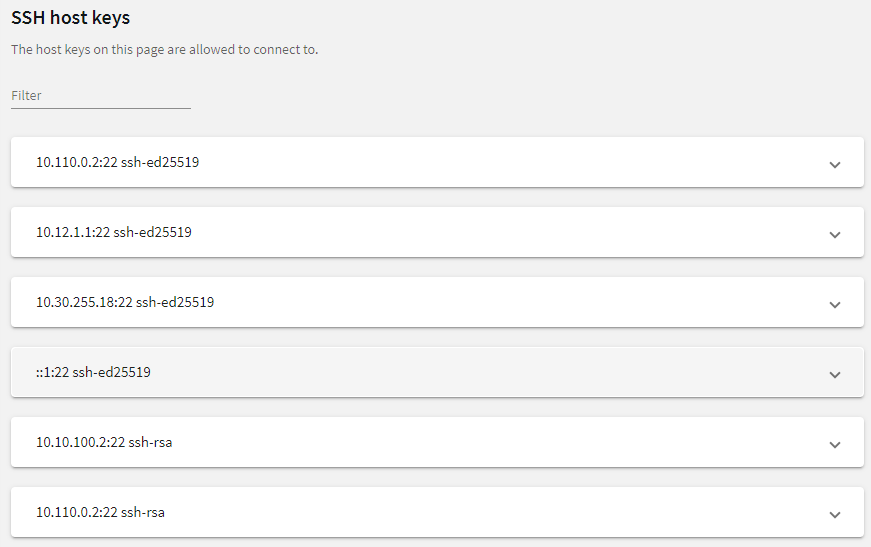
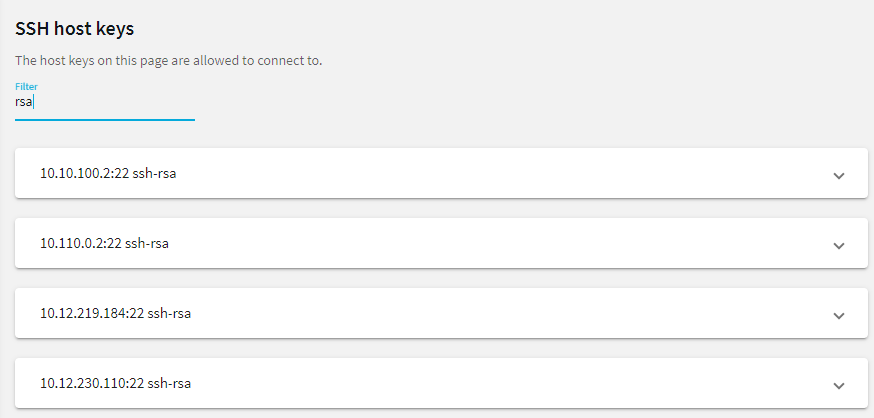
To filter, start typing into the Filter field. For example, enter rsa or an IP address and only relevant results are displayed.
Figure 238: SSH Control > Server Host Keys — Filtered RSA host keys


 .
. .
.
