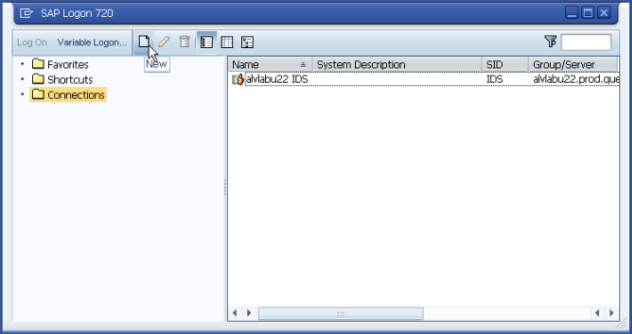
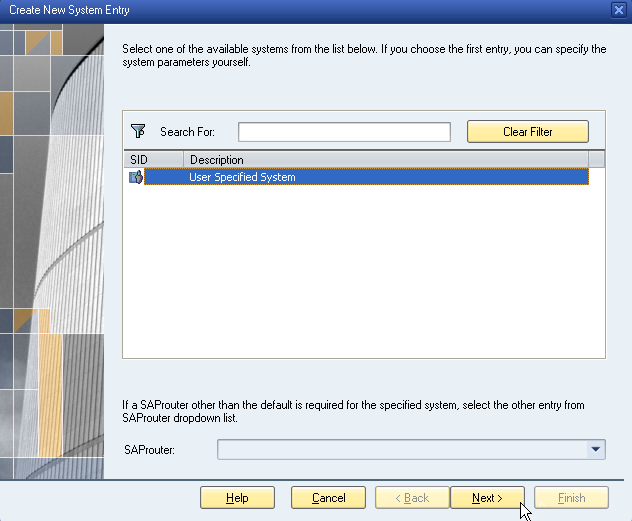
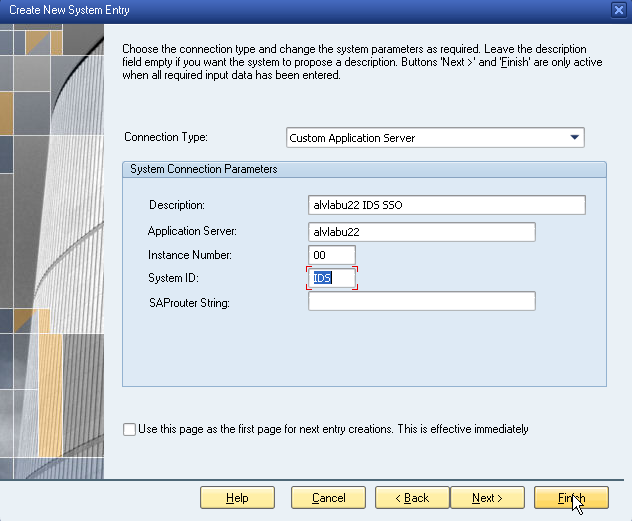
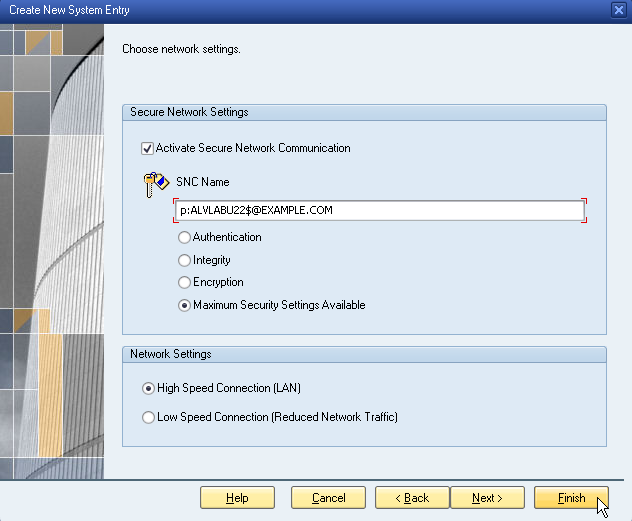
NOTE: For more details on installing and joining the Safeguard Authentication Services client, see the Safeguard Authentication Services Administration Guide. Commands prefixed with $ must be run by the SAP instance owner account. Commands prefixed with # must be run by root.
To install the Safeguard Authentication Services client and join the UNIX system to Active Directory
-
Mount the product media or extract the product archive, and change directory to the base directory. For example:
# mount /mnt/cdrom; cd /mnt/cdrom
-
Run the preflight program to check for proper connectivity and patch requirements. If failures are reported, see the Safeguard Authentication Services Administration Guide for requirements and troubleshooting instructions.
# ./preflight example.com
Replace example.com with your Active Directory domain name.
-
Install the Safeguard Authentication Services client.
# ./install.sh vasclnt
-
Join the system to Active Directory.
# /opt/quest/bin/vastool -u Administrator join --skip-config example.com
Where Administrator is an Active Directory user with rights to join and example.com is your Active Directory domain name.
NOTE: Ignore any license warnings reported from the join process. These are not relevant to SSO for SAP.