Introduction
This guide describes how to configure Microsoft SharePoint for use with Cloud Access Manager. Cloud Access Manager now supports two configuration options for Microsoft SharePoint, the Cloud Access Manager WS-Federation application template supports both SharePoint 2010 and SharePoint 2013 to simplify and automate application configuration.
In addition, you can configure the Cloud Access Manager reverse proxy to provide Single Sign-On (SSO) to web applications by automatically filling in the login form, or using either Integrated Windows Authentication (IWA) or Basic Authentication. You can also use the reverse proxy to enable secure access to internal web apps from the internet. For further information, please refer to the One Identity Cloud Access Manager Security and Best Practices Guide.
Topics:
Cloud Access Manager configuration prerequisites
Adding Microsoft SharePoint to Cloud Access Manager using WS-Federation
Protecting your SharePoint website with Cloud Access Manager
Enabling SharePoint People Picker functionality
Using the SharePoint People Picker
Adding Microsoft SharePoint to Cloud Access Manager using the reverse proxy
Cloud Access Manager configuration prerequisites
To install Cloud Access Manager as a standard two host production system
- Install Cloud Access Manager as described in the One Identity Cloud Access Manager Installation Guide and configure an Active Directory front-end authentication method as recommended in the One Identity Cloud Access Manager Configuration Guide.
- Verify your configuration by confirming that a user on a domain connected workstation can sign on to the portal using their Active Directory credentials and that the browser shows the portal is using a trusted Secure Sockets Layer (SSL) certificate. The ability to authenticate and an SSL certificate signed by a recognized Trusted Certification Authority are required to perform SSO to SharePoint 2013.
Adding Microsoft SharePoint to Cloud Access Manager using WS-Federation
To add SharePoint to Cloud Access Manager using the WS-Federation application template
- Add the SharePoint application to One Identity Cloud Access Manager using the SharePoint 2010/2013 template.
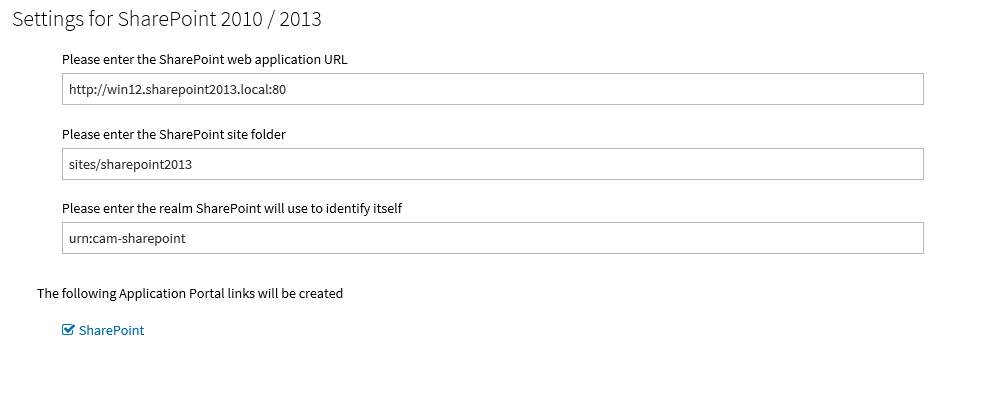
- Set the SharePoint server web application URL and the site folder.
- Configure a realm name to later identify this connection in SharePoint.
-
Click Save & Next.
NOTE: While SharePoint server may include multiple sites, the Cloud Access Manager template will only auto-configure one of them for you. You can add others manually as extra application portal links when the initial SharePoint application has been created.
NOTE: The relying party realm may be any value you choose, with urn: as its prefix, for example urn:cam-sharepoint. You will enter this value in SharePoint later when you create the new authenticator.
-
In Subject Mapping you must specify the attribute that Cloud Access Manager will use to derive the user's name for log in. The default attribute is mail. Click Next.
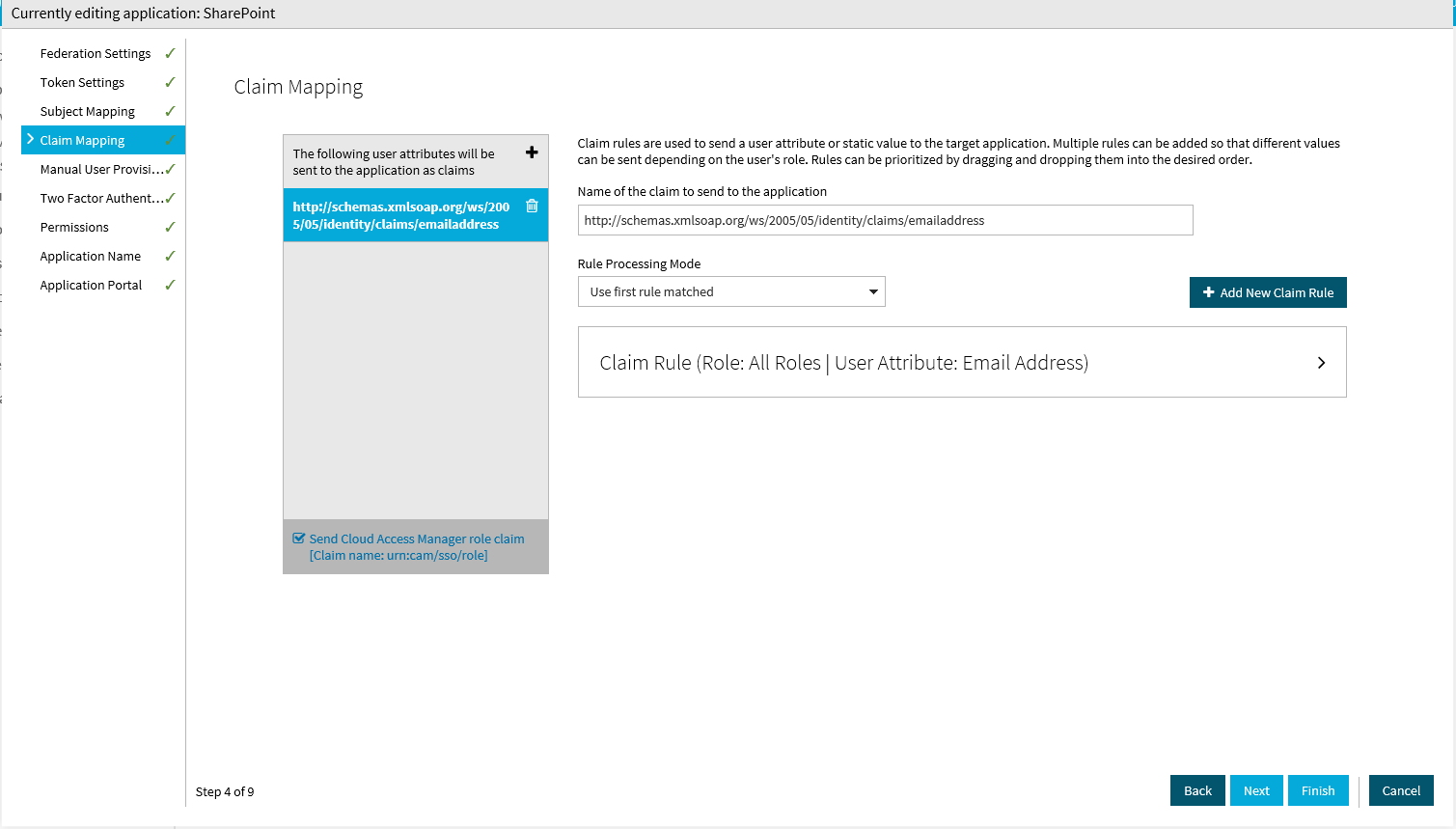
On the Claim Mapping page you can configure the values Cloud Access Manager will pass to SharePoint in the form of claims. By default only a user’s email address is required to successfully authenticate. If you need to pass other values, for example employee id, you can add further claims on the Claim Mapping page and populate them with the appropriate values from the relevant front-end authenticator.
You will also need to create the associated claim type mappings when you create the new claims-based authenticator in SharePoint. The Cloud Access Manager for Microsoft SharePoint utility will do this for you automatically, or you can add the claim type mappings manually using the New-SPClaimTypeMapping command. For further details, please refer to Manual configuration of a SharePoint 2013 Server WS-Federation Trust.
-
When complete, click Next.
-
You will now see the Permissions page. This enables you to control which users can access the application. By default, all Cloud Access Manager users have access to the application. You can restrict access to the application to users who belong to a specific role, but for this example click Next to allow all users to access the application.
-
Enter an Application Name, for example SharePoint 2013, then click Next.
-
To configure how the application is displayed on the Cloud Access Manager Portal, enter the Title and Description you want to display on the Cloud Access Manager Portal.
-
Enter the URL that you want your users to be initially redirected to.
-
Click Get Application Icon to locate and display the icon of the application or upload an icon of your choice.
-
Click Finish to complete the configuration of the application.
-
Cloud Access Manager will now generate a certificate that you must download and add to the SharePoint server.
Configuring a SharePoint 2010 or 2013 WS-Federation Trust using the Cloud Access Manager for Microsoft SharePoint utility
This section describes how to install the Cloud Access Manager for SharePoint utility and how to use it to establish a trust between Cloud Access Manager and SharePoint Server 2010 or 2013.