Dell™ One Identity Cloud Access Manager 8.1.2 - SonicWALL Integration Overview
|
• |
Overview
Functional highlights
|
3 |
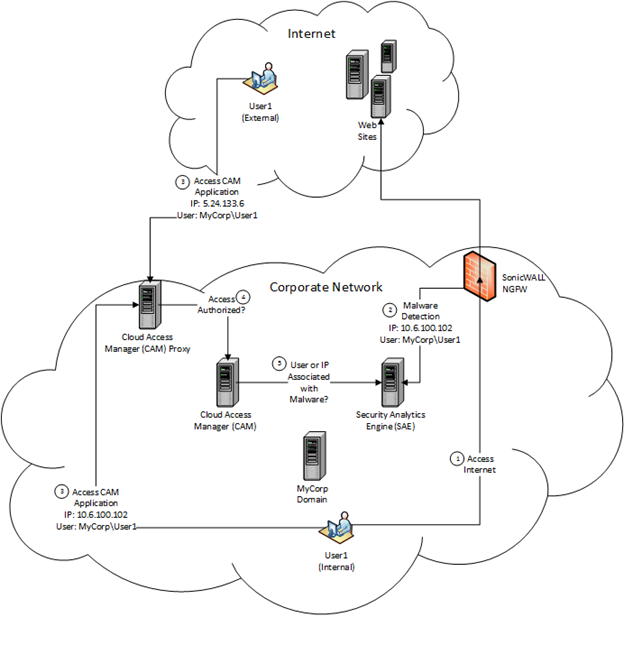
The following is a high level overview of the user actions and information flow; this is illustrated in Figure 1 with further details provided in Functional details:
Functional details
The following sections provide a detailed breakdown of functionality related to the user authentication, malware detection and risk assessment steps highlighted in Functional highlights, this includes: