Installation
Prerequisites
Make sure the following prerequisites are met before you attempt to install Dell™ One Identity Cloud Access Manager, please refer to Proxy host and STS host for component specific requirements.
| |||||
1 Supported for Integrated Windows Authentication (IWA).
2 Supported for Cloud Access Manager Administration.
3Internet Explorer® version 9 and above supported for Cloud Access Manager Administration.
Ensure the following prerequisites are met before installation:
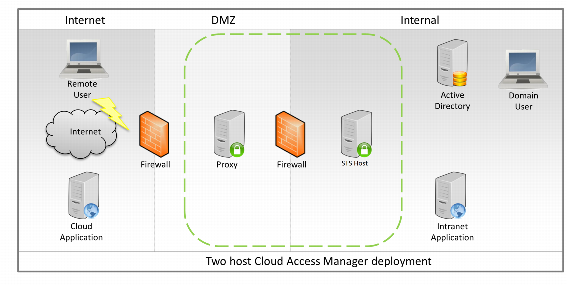
To support the scenario illustrated in Figure 1 where you need to expose internal applications to external users, the host should be deployed within the DMZ network.
Ensure that the following hardware requirements are met:
Ensure that the following operating system requirements are met with the latest Microsoft® Hotfixes applied.
|
Microsoft® Windows Server® 2008 R2 Microsoft® Windows Server® 2008 R2 Server Core |
|
Microsoft® Windows Server® 2012 Microsoft® Windows Server® 2012 Server Core |
|
Microsoft® Windows Server® 2012 R2 Microsoft® Windows Server® 2012 R2 Server Core |
A signed wildcard Secure Sockets Layer (SSL) certificate is required to cover the wildcard DNS subdomain used by the Cloud Access Manager Proxy. The wildcard SSL certificate must be obtained using the Certificate Signing Request (CSR) generated by Cloud Access Manager during configuration. For example, if you created a wildcard DNS subdomain called webapps within your domain company.com, then you would need to obtain a signed wildcard SSL certificate for *.webapps.company.com for full instructions, please refer to Managing your SSL Certificate in the Dell One Identity Cloud Access Manager Configuration Guide.
The host should be deployed within the internal network.
Ensure that the following hardware requirements are met:
|
|
If Active Directory® will be used to source users for SSO, the Security Token Service (STS) host must be a member of the Active Directory domain containing these users. Dell™ One Identity Cloud Access Manager can also use federated identities from third party domains using SAML 2.0 or WS-Federation.
Ensure that the following database requirements are met:
|
Microsoft® SQL Server® 2008 or above | |
When you install Dell™ One Identity Cloud Access Manager using the Dell Autorun, as described in Installing Cloud Access Manager, the following software is automatically installed. This software is required for support purposes only.
|
• |
Microsoft® .NET |
|
• |
Windows® Identity Foundation v3.5 (Pre 2012) |
|
• |
Microsoft® System CLR Types for SQL Server 2012 |
|
• |
|
• |
IIS (/online /enable-feature /featurename:IIS-WebServerRole/featurename:IIS-StaticContent /featurename:IIS-DefaultDocument /featurename:IIS-DirectoryBrowsing /featurename:IIS-HttpErrors /featurename:IIS-ISAPIExtensions /featurename:IIS-ISAPIFilter /featurename:IIS-HttpLogging /featurename:IIS-RequestFiltering /featurename:IIS-HttpCompressionStatic /featurename:IIS-ManagementConsole) |
|
• |
IIS, Server Core (/online /enable-feature /featurename:IIS-WebServerRole/featurename:IIS-StaticContent /featurename:IIS-DefaultDocument /featurename:IIS-DirectoryBrowsing /featurename:IIS-HttpErrors /featurename:IIS-ISAPIExtensions /featurename:IIS-ISAPIFilter /featurename:IIS-HttpLogging /featurename:IIS-RequestFiltering /featurename:IIS-HttpCompressionStatic /featurename:IIS-ManagementService) |
|
• |
HTTP Activation, 2008 R2 (/online /enable-feature /featurename:NetFx3 /featurename:IIS-NetFxExtensibility /featurename:WAS-ProcessModel /featurename:WAS-WindowsActivationService /featurename:WAS-NetFxEnvironment /featurename:WAS-ConfigurationAPI /featurename:WCF-HTTP-Activation) |
|
• |
HTTP Activation, 2008 R2 Server Core (/online /enable-feature /featurename:NetFx3-ServerCore /featurename:IIS-NetFxExtensibility /featurename:WAS-ProcessModel /featurename:WAS-WindowsActivationService /featurename:WAS-NetFxEnvironment /featurename:WAS-ConfigurationAPI /featurename:WCF-HTTP-Activation) |
|
• |
HTTP Activation, 2012 and above (/online /enable-feature:WCF-HTTP-Activation45 /all) |
|
• |
WCF Services, 2012 and above (/online /enable-feature:WCF-Services45) |
|
• |
ASP .NET 4.5, 2012 and above (/online /enable-feature: NetFx4Extended-ASPNET45 /all) |
If you want to install this software using a local path, rather than the default internet sourcing use the DismSource switch to specify where the Cloud Access Manager bootstrapper will instruct the DISM tool to look for the required files. For example, if the installation CD is in drive D then you could specify:
“Cloud Access Manager Setup.exe" DismSource=d:\sources\sxs
As an example, this will result in a call to DISM similar to the following:
dism.exe /online /enable-feature:Windows-Identity-Foundation /source:d:\sources\sxs
Installing Cloud Access Manager
|
2 |
|
3 |
|
5 |
|
6 |
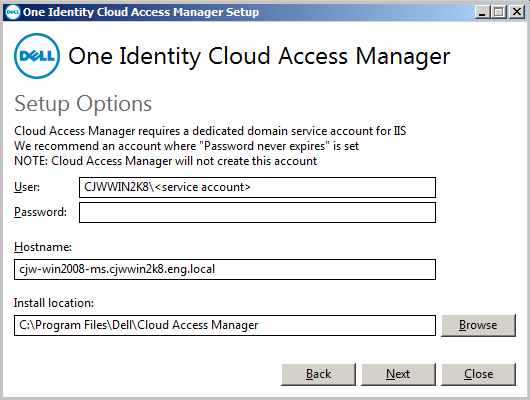
Choose the account to run the STS components, enter the username and password of an Active Directory® domain account. This account does not require special administrative privileges but a dedicated service account is recommended, ideally with Password never expires set. |
|
7 |
|
NOTE: The STS host requires Microsoft® .NET framework version 4.5. If this is not already installed on the host, the installer will download and install .NET framework from the internet. |
|
8 |
When the installation is complete, click Launch to start the configuration wizard. |
|
9 |
The configuration wizard can take a while to open when accessed for the first time. This is due to Internet Information Services (IIS) initializing and starting the web applications. Please wait while Internet Explorer® opens and displays the Cloud Access Manager Welcome page.  |
|
12 |
Enter credentials that have administrative privileges for the Microsoft® SQL Server® instance, typically a member of the administrators group, that will be used by Cloud Access Manager. The credentials will be used to create a new database for Cloud Access Manager. Click Next. |
|
13 |
Click Download Proxy Installer and save the installer to a temporary location on the STS host. When the download is complete, transfer the installer to the proxy host. |
|
14 |
Switch to the proxy host and double-click the proxy installer Cloud Access Manager Proxy Setup.exe to start the proxy install. |
|
16 |
|
18 |
Return to the STS host. In the Cloud Access Manager browser window, click Next on the Install the Proxy page. 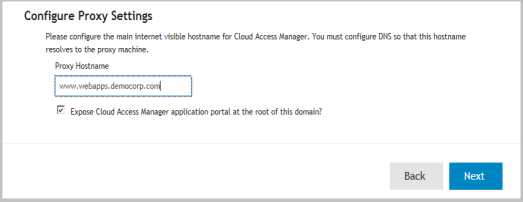 |
|
20 |
Configuring Cloud Access Manager
Now that you have successfully installed Dell™ One Identity Cloud Access Manager, you need to:
Please refer to the Dell™ One Identity Cloud Access Manager Configuration Guide for further information.