Companies have varying requirements that they need for regulating internal and external employee access to company resources. They also have to demonstrate that they adhere to legal requirements. Such requirements can be defined as policies.
One Identity Manager allows you to manage these company policies and thus to assess the risk involved. Assuming the appropriate data is stored in the One Identity Manager database, One Identity Manager determines all the company resources that violate these company policies. You can also define company policies for the purpose of providing reports that do not have any connection with One Identity Manager.
Figure 1: Company policies in One Identity Manager
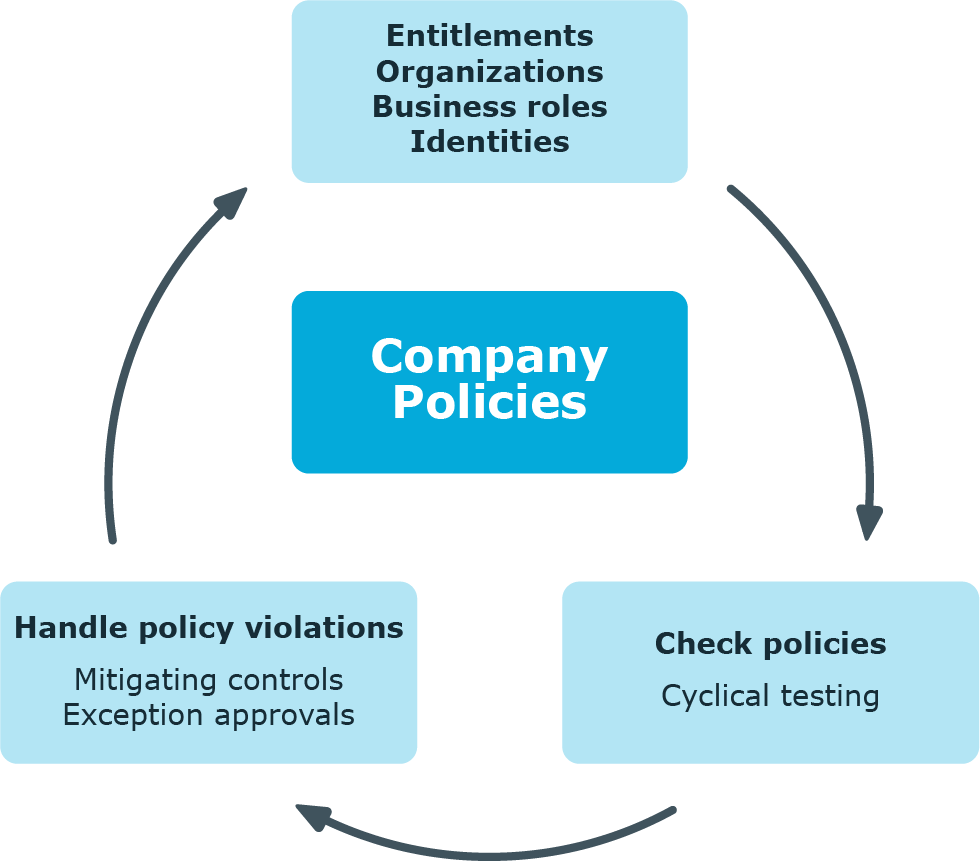
Adherence to company policies is checked regularly using scheduled tasks. You can incorporate company policies into the regular attestation of your company resources to decide on further handling of any violated ones. Risk assessment can be run for all company policies. Different reports and statistics provide you with an overview of violated policies.
Example of company policies are:
-
All cost centers are assigned a manager.
-
All departments are assigned identities.
-
All identities are attested.
-
Deactivated identities do not have any enabled user accounts.
NOTE: Prerequisite for the using company policies in One Identity Manager is the installation of the Company Policies Module. For more information about installing, see the One Identity Manager Installation Guide.
To be able to map company policies
If you disable the configuration parameter at a later date, model components and scripts that are no longer required, are disabled. SQL procedures and triggers are still carried out. For more information about the behavior of preprocessor relevant configuration parameters and conditional compiling, see the One Identity Manager Configuration Guide.
The following users are used for setting up and administration of company policies.
Table 1: Users
| Company policy administrators |
Administrators must be assigned to the Identity & Access Governance | Company policies | Administrators application role.
Users with this application role:
-
Enter base data for setting up company policies.
-
Set up policies and assign policy supervisors to them.
-
Can calculation policies and view policy violations if required.
-
Set up reports about policy violations.
-
Enter mitigating controls.
-
Create and edit risk index functions.
-
Administer application roles for policy supervisors, exception approvers and attestors.
-
Set up other application roles as required. |
| Policy supervisors |
Policy supervisors must be assigned to the Identity & Access Governance | Company policies | Policy supervisors application role or another child application role.
Users with this application role:
-
Are responsible for the contents of company policies.
-
Edit working copies of company policies.
-
Enable and disable company policies.
-
Can calculation policies and view policy violations if required.
-
Assign mitigating controls. |
| One Identity Manager administrators |
administrator and administrative system users Administrative system users are not added to application roles.
administrators:
-
Create customized permissions groups for application roles for role-based login to administration tools in the Designer as required.
-
Create system users and permissions groups for non role-based login to administration tools in the Designer as required.
-
Enable or disable additional configuration parameters in the Designer as required.
-
Create custom processes in the Designer as required.
-
Create and configure schedules as required. |
| Exception approvers |
Exception approvers must be assigned to the Identity & Access Governance | Company policies | Exception approvers application role or a child application role.
Users with this application role:
|
| Company policy attestors |
Attestors must be assigned to the Identity & Access Governance | Company policies | Attestors application role.
Users with this application role:
NOTE: This application role is available if the module Attestation Module is installed. |
| Compliance and security officer |
Compliance and security officers must be assigned to the Identity & Access Governance | Compliance & Security Officer application role.
Users with this application role:
-
View all compliance relevant information and other analysis in the Web Portal. This includes attestation policies, company policies and policy violations, compliance rules, and rule violations and risk index functions.
-
Edit attestation polices. |
| Auditors |
Auditors are assigned to the Identity & Access Governance | Auditors application role.
Users with this application role:
|
Company policies include more properties in One Identity Manager apart from just technical descriptions, for example, risk assessment of a policy violation and accountability. Classification of company policies by compliance framework and structuring in policy groups is also possible.
Detailed information about this topic
A working copy is added for every company policy. Edit the working copies to create company policies and change them. Changes to the company policy do not take effect until the working copy is enabled.
NOTE: One Identity Manager users with the Identity & Access Governance | Identity Audit | Policy supervisors application role can edit existing working copies that they are entered as being responsible for in the main data.
To create a new company policy
-
In the Manager, select the Company Policies > Policies category.
-
Click  in the result list.
in the result list.
-
Enter the company policy's main data.
-
Save the changes.
This adds a working copy.
-
Select the Enable working copy task. Confirm the security prompt with OK.
This adds an enabled company policy. The working copy is retained and can be used to make changes later.
To edit an existing company policy
-
In the Manager, select the Company Policies > Policies category.
-
Select a company policy in the result list.
-
Select the Create working copy task.
The data from the existing working copy are overwritten by the data from the original company policy after a security prompt. This opens the working copy, which you can then edit.
- OR -
In the Manager, select the Company policies > Policies > Working copies of policies category.
-
Select a working copy in the result list.
-
Select the Change main data task.
-
Edit the working copy's main data.
-
Save the changes.
-
Select Enable working copy. Confirm the security prompt with OK.
Changes to the working copy are transferred to the company policy. This can reenable a disabled company policy if prompted.


 in the result list.
in the result list.