Exercise 6: Auditing access requests
The Request Workflow dialog allows you to audit the transactions that took place within a password release or session request. This dialog can be accessed using the 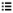 Workflow button in the Activity Center view when an access request event is selected in an activity audit log report.
Workflow button in the Activity Center view when an access request event is selected in an activity audit log report.
The 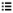 Workflow button also appears to reviewers for completed access requests.
Workflow button also appears to reviewers for completed access requests.
To view the request workflow for a password release or session request
- Log in as the Auditor.
- From the Home page, navigate to the
 Activity Center.
Activity Center.
- Run an activity audit log report.
-
On the results page, select an access request event and click 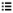 Workflow.
Workflow.
The Request Workflow dialog displays the workflow transactions from request to approval to review.
- Select Show Details to view more information about the request, approval, and review transactions of that request.
Stay logged in as the Auditor for the next exercise.
Exercise 7: Running reports
 Reports allows the Auditor and Security Policy Administrators to view and export entitlement reports that show which assets and accounts a selected user is authorized to access. Reports may be exported in .csv or .json format.
Reports allows the Auditor and Security Policy Administrators to view and export entitlement reports that show which assets and accounts a selected user is authorized to access. Reports may be exported in .csv or .json format.
Entitlement reports
Safeguard for Privileged Passwords provides these entitlement reports.
- User: Lists information about the accounts a selected user is authorized to request.
- Asset: Lists information about the accounts associated with a selected asset and the users who have authorization to request those accounts.
- Account: Lists detailed information about the users who have authorization to request a selected account including: Entitlement, Policy, Access Type, Password Included, Password Change, Time Restrictions, Expiration Date, Group, From Linked Account, and Last Accessed.
To run an entitlement report
- As Auditor, select
 Reports from the Safeguard for Privileged Passwords desktop Home page.
Reports from the Safeguard for Privileged Passwords desktop Home page.
- Choose to view entitlements by Asset.
- Browse to select all assets and click OK.
- In the top pane of the results screen, select an asset to see the details.
- View both the Total Accounts tab and the People tab.
- Select an item from the results to drill down into the details about the users and the accounts.
- Click
 Export to create a file of the search results in a location of your choice.
Export to create a file of the search results in a location of your choice.
- Log out.
Discovery exercises
These exercises will guide you through a step-by-step evaluation of the Safeguard for Privileged Passwords discovery features:
Exercise 1: Discovering assets
Safeguard for Privileged Passwords allows you to set up Asset Discovery jobs to run automatically against the directory assets you have added to Safeguard for Privileged Passwords. For more information, see the Safeguard for Privileged Passwords Administration Guide, Asset Discovery section.
To create an Asset Discovery job using the Directory Method
- Log in as the Asset Administrator and navigate to
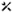 Administrative Tools | Discovery | Asset Discovery tile.
Administrative Tools | Discovery | Asset Discovery tile.
- Click
 Add to create an Asset Discovery job.
Add to create an Asset Discovery job.
- Provide information for the Asset Discovery job on the following tabs:
| General tab |
- Enter a name for the Asset Discovery job.
- For Partition, browse to select the partition.
- For Method, select Directory.
|
| Information tab |
In Directory, select the directory. |
| Rules tab |
Click  Add to create an Asset Discovery rule: Add to create an Asset Discovery rule:
- Enter a Name for the rule.
- For the Settings, click Add Condition to define criteria, including the search scope in the directory, then click OK.
- On the Asset Discovery Rule dialog, for Connection Template, leave the default of None.
- For Asset Profile, use the default partition profile to govern the discovered assets.
- Keep the Manged Network default value and click OK.
|
| Schedule tab |
You can skip adding the schedule to run the Asset Discovery job since we will run the discovery job manually for this exercise. |
| Summary tab |
Review the discovery job and click Add Discovery. |
- In the Asset Discovery dialog, select the job and click
 Run Now. The Tasks pop-up shows the progress of the Asset Discovery job.
Run Now. The Tasks pop-up shows the progress of the Asset Discovery job.
- When the Tasks pop-up indicates that the job is successful (
 Success), click the Asset Discovery Results tile.
Success), click the Asset Discovery Results tile.
- In the Asset Discovery Results grid:
- Select Last 24 Hours.
- Click
 Refresh to show the latest data.
Refresh to show the latest data.
- Double-click an Asset Discovery job to see the result of the discovery.
- Click on the number of # Assets Found to view individual discovered assets.
-
To control management of an asset:
- Navigate to Administrative Tools | Assets.
- Right-click the asset then click Access Requests.
- Choose Enable Session Request or Disable Session Request.
Note: When you ignore an asset, Safeguard for Privileged Passwords disables it and disables/hides all associated accounts. If you choose to Enable Session Request the asset later, Safeguard for Privileged Passwords reenables all the associated accounts.
- You can also search the Activity Center for information about discovery jobs that have run. This is the same information as presented in the the Asset Discovery Results grid.
- Click
 Home.
Home.
- Under I would like to see, click
 Edit and select Asset Discovery Activity.
Edit and select Asset Discovery Activity.
- Under ... occurring within the ..., click
 Edit and select Last 24 Hours.
Edit and select Last 24 Hours.
- Keep the default of All Activity in the Last 24 Hours.
- Click the Run button.
- In the results grid, double-click the job to more information then click Details to show the progress of the Asset Discovery job.
- The Asset Discovery events are listed in the Activity Category column.
- To view all activity in the last 24 hours, return to the Activity Center dialog.
- Under I would like to see, click
 Edit and select All Activity.
Edit and select All Activity.
- Click the Run button.
- In the grid, User column, click the
 filter, and select your User name.
filter, and select your User name.
- To display additional columns, click
 Column in the upper right corner and select additional columns, such as Appliance, Asset, Object Name, and Object Type.
Column in the upper right corner and select additional columns, such as Appliance, Asset, Object Name, and Object Type.
- Double-click any of the rows to view additional information.
Set asset connection authentication credentials to define a service account
When None is selected as the Authentication Type, the discovered assets will not have a service account. In the next steps you will change the Authentication Type.
These steps provide valid information only if:
- You have created a directory asset and directory accounts that will be used as the service account for the Windows asset discovered.
- You have Linux assets that are discovered that have QAS installed and are joined to the directory.
- In Assets, select one of the newly discovered assets.
- On the General tab, double-click the Connection information box or click the
 Edit icon next to it.
Edit icon next to it.
- Choose an Authentication Type of Directory Account and provide the service account credentials.
Note:Safeguard for Privileged Passwords uses a service account to connect to an asset to securely manage passwords for the accounts on that asset.
Activity Center.
Workflow.

 Reports allows the Auditor and Security Policy Administrators to view and export entitlement reports that show which assets and accounts a selected user is authorized to access. Reports may be exported in .csv or .json format.
Reports allows the Auditor and Security Policy Administrators to view and export entitlement reports that show which assets and accounts a selected user is authorized to access. Reports may be exported in .csv or .json format.  Export to create a file of the search results in a location of your choice.
Export to create a file of the search results in a location of your choice.
 Administrative Tools | Discovery | Asset Discovery tile.
Administrative Tools | Discovery | Asset Discovery tile.
 Add to create an Asset Discovery job.
Add to create an Asset Discovery job.
 Run Now. The Tasks pop-up shows the progress of the Asset Discovery job.
Run Now. The Tasks pop-up shows the progress of the Asset Discovery job.
 Success), click the Asset Discovery Results tile.
Success), click the Asset Discovery Results tile.
 Refresh to show the latest data.
Refresh to show the latest data.
 Home.
Home.
 Edit and select Asset Discovery Activity.
Edit and select Asset Discovery Activity.
 filter, and select your User name.
filter, and select your User name.
 Column in the upper right corner and select additional columns, such as Appliance, Asset, Object Name, and Object Type.
Column in the upper right corner and select additional columns, such as Appliance, Asset, Object Name, and Object Type.
 Edit icon next to it.
Edit icon next to it.