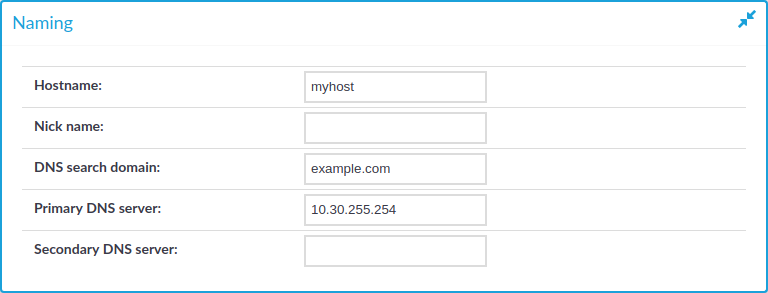
Figure 51: Basic Settings > Network > Naming
-
Hostname: Name of the machine running SPS.
-
Nick name: The nickname of SPS. Use it to distinguish the devices. It is displayed in the core and boot login shells.
-
DNS search domain: Name of the domain used on the network. When resolving the domain names of the audited connections, SPS will use this domain to resolve the target hostname if the appended domain entry of a target address is empty.
-
Primary DNS server: IP address of the name server used for domain name resolution.
-
Secondary DNS server: IP address of the name server used for domain name resolution if the primary server is unaccessible.
The HTTPS proxy settings must be configured if your company policies do not allow devices to connect directly to the web. Once configured, SPS uses the configured proxy server for outbound web requests to external integrated services, such as Join to Starling or SPS plugins.
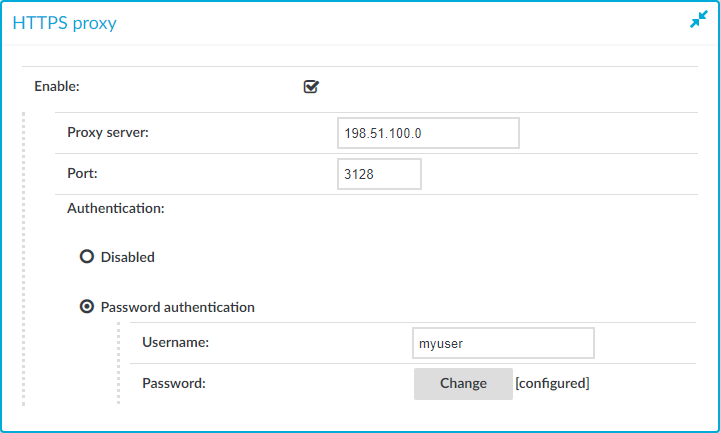
Figure 52: Basic Settings > Network > HTTPS proxy
-
Proxy server: The IP address or DNS name of the proxy server.
-
Port: The IP address or DNS name of the proxy server.
NOTE:
If different ports are specified in the Proxy server and the Port field, the Port field takes precedence.
-
Username: The user name used to connect to the proxy server.
NOTE:
The username and password are only required if your proxy server requires them to be specified.
-
Password: The password required to connect to the proxy server.
NOTE:
The username and password are only required if your proxy server requires them to be specified.
You can configure two separate login addresses for accessing the web interface of One Identity Safeguard for Privileged Sessions (SPS):
-
Web login (admin): On this address, users can, depending on their access privileges, modify the configuration of SPS, and perform authentication-related activities (gateway authentication, 4-eyes authorization).
-
Web login (user): The configuration of SPS cannot be viewed or altered from this address. Users (even ones with administrator privileges) can only perform gateway authentication and 4-eyes authorization.
Both login addresses can be configured to restrict connections to a configured set of IP addresses only.
NOTE:
When configuring HTTP or SSH connections, avoid using the IP address configured for administrator or user login on SPS.
To configure two separate login addresses for accessing the web interface of SPS
-
Navigate to Basic Settings > Local Services > Web login.
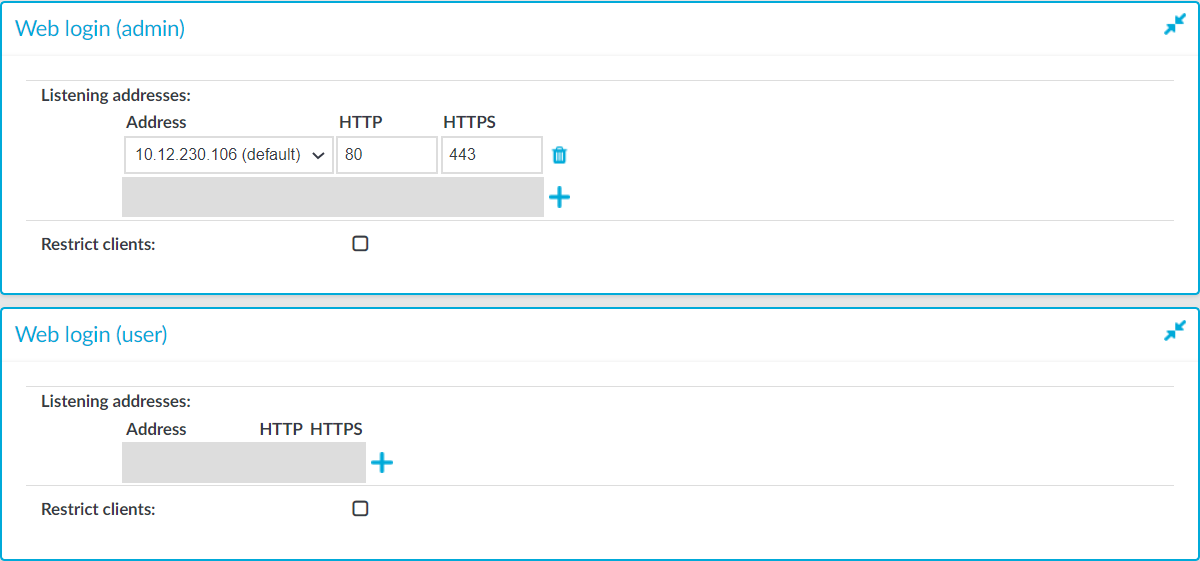
Figure 53: Basic Settings > Local Services > Web login — Configuring web login address
-
Choose  in the Listening addresses field.
in the Listening addresses field.
-
Enter the IP address to use for connecting to SPS's user interface into the Address field.
The available addresses correspond to the interface addresses configured in Basic Settings > Network > Interfaces. Only IPv4 addresses can be selected.
-
Enter the port number for HTTP connections into the HTTP field.
-
Enter the port number for HTTPS connections into the HTTPS field.
-
(Optional) To permit access to the SPS web interface only from selected subnets or IP addresses, select Restrict clients, click  and enter the IP address and netmask of the allowed clients. Note that these settings do not affect the SSH access to SPS.
and enter the IP address and netmask of the allowed clients. Note that these settings do not affect the SSH access to SPS.
|

|
Caution:
Permit administrative access to SPS only from trusted networks. If possible, monitored connections and administrative access to the SPS web interface should originate from separate networks.
After comitting the changes, the web interface will be available only from the configured subnets or IP addresses. |
Use an IPv4 address.
-
Recommended: configure a separate login address for user connections in Web login (user). The configuration settings of SPS cannot be viewed or modified from this address.
-
Click Commit.
You can assign logical interfaces to a physical interface. Each logical interface must have its own VLAN ID, and can have its own set of (alias) IP addresses and prefixes. The configured name for each logical interface is visible on One Identity Safeguard for Privileged Sessions (SPS)'s user interface only.
You can configure IPv4 and IPv6 addresses as well. IPv6 is intended for configuring monitored connections. Local services (including the web login) require IPv4 addresses. An interface can have multiple IP addresses, including a mix of IPv4 and IPv6 addresses.
NOTE: SPS does not support scenarios with two hosts using the same IP address on different VLAN groups.
To manage logical interfaces
-
Navigate to Basic Settings > Network > Interfaces.
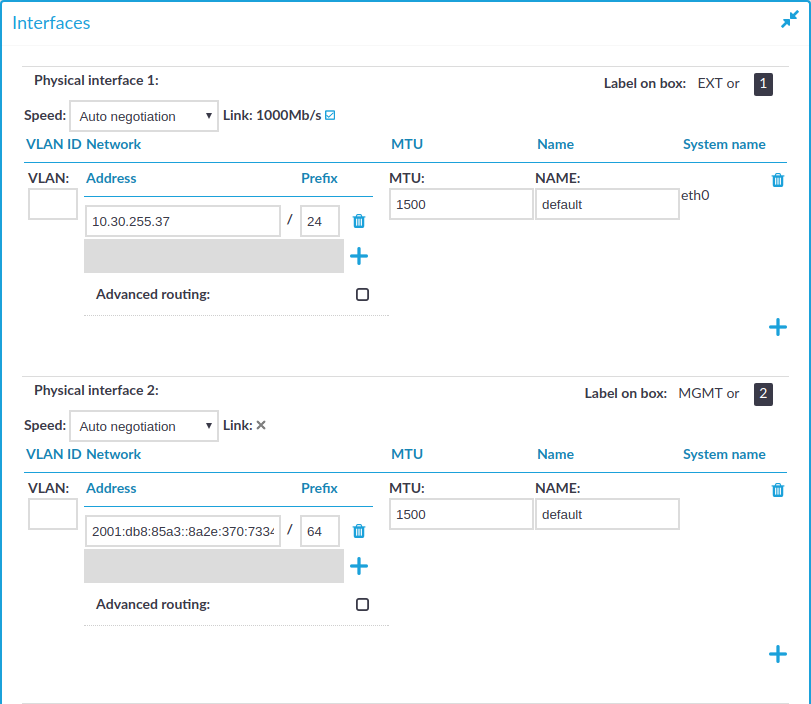
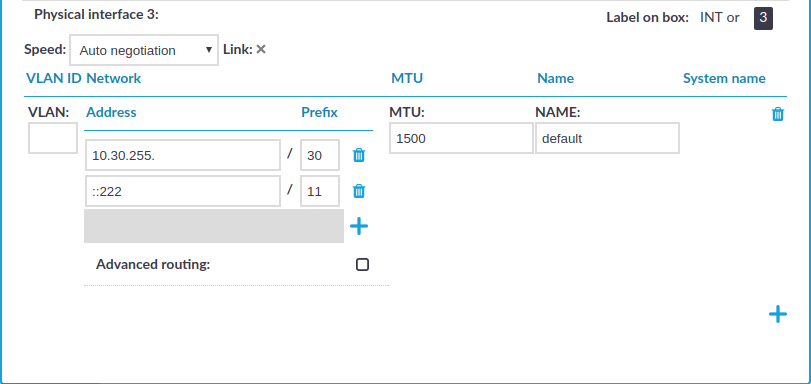
Figure 54: Basic Settings > Network > Interfaces — Managing the logical interfaces
-
If necessary, use the label on the SPS hardware to identify the physical interface to which you want to assign a logical interface.
-
Choose  to add a new logical interface. Provide the following:
to add a new logical interface. Provide the following:
-
VLAN: The VLAN ID of the logical interface. Optional.
|

|
Caution:
Do not set the VLAN ID unless your network environment is already configured to use this VLAN. Otherwise, your SPS appliance will be unavailable using this interface. |
-
Address: The IP address of the logical interface.
Alternatively, you can enter a hostname instead. SPS automatically resolves the hostname to an IP address.
NOTE: Note the following limitations:
-
To resolve the hostnames, SPS uses the Domain Name Servers set in the Basic Settings > Network > Naming > Primary DNS server and Secondary DNS server fields.
-
If the Domain Name Server returns multiple IP addresses, SPS randomly selects from the list.
NOTE: Do not use IP addresses that fall into the following ranges:
-
Prefix: The IP range of the logical interface.
-
Optional: To add additional (alias) IP addresses and prefixes to a logical interface, click  . To remove an alias IP address, click the corresponding
. To remove an alias IP address, click the corresponding  .
.
-
MTU: Maximum Transmission Unit (MTU) to set per network interface (VLAN or network interface card). The default value is 1500.
-
Name: The name of the logical interface. This name is visible on SPS's user interface only.
To remove a logical interface, choose the  on the right side.
on the right side.
-
Click  .
.




 in the Listening addresses field.
in the Listening addresses field.


 .
. .
.