Managing UNIX users with MMC
You can access Active Directory Users and Computers (ADUC) from the Control Center. Navigate to the Tools > Safeguard Authentication Services Extensions for Active Directory Users and Computers.
After installing Safeguard Authentication Services on Windows, a UNIX Account tab appears in the Active Directory user's Properties dialog:
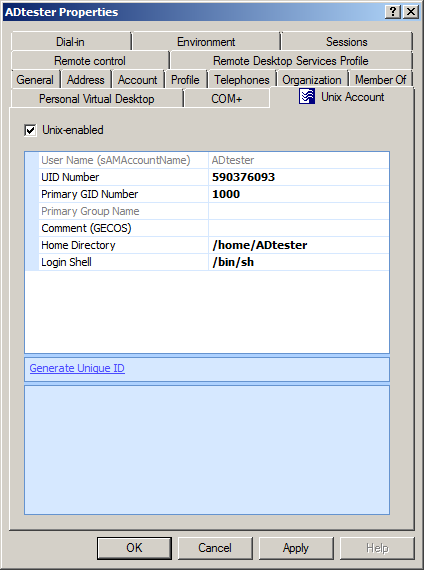
NOTE: If the UNIX Account tab does not appear in the user's Properties dialog, review the installation steps outlined in the Safeguard Authentication Services Installation Guide to ensure that Safeguard Authentication Services was installed correctly. For more information, see UNIX Account tab is missing in ADUC.
Select the UNIX-enabled option to UNIX-enable the user. UNIX-enabled users can log in to UNIX hosts joined to the domain. Selecting this option causes Safeguard Authentication Services to generate default values for each of the UNIX attributes. You can alter the way default values are generated using Control Center.
Table 12: UNIX attributes
|
User Name |
This is the UNIX user name of the Windows account used to log in to a UNIX host. |
|
UID Number |
Use this field to set the numeric UNIX User ID (UID). This value must be unique in the forest. In some environments, users have a different UID number on each UNIX host. In this case, you can use mapped user, local account overrides, or Ownership Alignment Tool (OAT) to ensure that the local UNIX user is associated with the correct Windows user account and that local resources are still associated with the correct UID Number. |
|
Primary Group ID |
Use this field to set the UNIX Primary Group ID. This field determines the group ownership of files that are created by the user. Click the Search button to search for UNIX-enabled groups in Active Directory. This field defaults to 1000. You can modify the default in the Control Center > Preferences. |
|
Primary Group Name |
This read-only field displays the name of the group associated with the Primary Group ID. If the Primary Group ID is not associated with a UNIX-enabled Active Directory group, then the field is blank. |
|
Comment (GECOS) |
Use this free-form field to store information that is found in the GECOS field in /etc/passwd. This information is typically used to record the user's full name and other information, such as phone number and office location. If this field contains a colon, the colon will be replaced by a _ on UNIX. You can change the Comment (GECOS) default in the Control Center > Preferences. |
|
Home Directory |
Use this field to configure the user's UNIX home directory. If the home directory does not exist when the user logs in to a machine for the first time, Safeguard Authentication Services creates it. The default value is /home/<User Name>. (/Users/<User Name> on macOS.) You can override the default home directory prefix in the Control Center > Preferences. |
|
Login Shell |
Use this field to configure the shell that is launched when the user logs in to UNIX using a terminal-based login. If the specified shell does not exist, the user will not be allowed to log in. You can use a Symlink Policy to ensure that a particular shell path exists on all of your UNIX hosts. This value defaults to /bin/sh. You can modify the default in the Control Center > Preferences. |
|
Generate Unique ID |
Click this link to generate a unique User ID number. If the ID is already unique, it will not be modified. By default you cannot save a non-unique ID number. You can modify this setting in the Control Center > Preferences. |
|
Clear UNIX Attributes |
If a user is not UNIX-enabled, you can click this link to clear all of the UNIX attribute values. |
Managing user accounts from the UNIX command line
NOTE: In the following examples, it is assumed that you have already logged in with a user that has sufficient permissions in Active Directory to perform the intended command. See Permissions matrix. If your present account is lacking necessary permissions, you may use either of the following methods to perform the desired administrative command:
-
Use vastool kinit <elevated-permission-user> to obtain elevated permissions. For example, execute vastool kinit admin-user, then perform the command as outlined in the examples.
-OR-
-
Use vastool -u <elevated-permission-user>. For example, vastool create user test-account becomes vastool -u admin-user create user test-account.
You can use the vastool command from the command line to create and delete users, as well as list user information.
To create a user, use the vastool create command. The following command creates a non-UNIX-enabled user, bsmith, in Active Directory:
vastool create bsmith
To create a user that has its UNIX account enabled, pass in an /etc/passwd formatted string using the -i option, as follows:
vastool create -i "bsmith:x:1003:1000:Bob:/home/bsmith:/bin/bash" bsmith
By default, all users created with vastool create are created in the Users container. To create a user in a different organizational unit, use the -c command line option.
The following command creates a UNIX-enabled user, bsmith, in the OU=sales,DC=example,DC=com Organizational Unit:
vastool create -i \
"bsmith:x:1003:1000:Bob:/home/bsmith:/bin/bash" \
-c "OU=sales,DC=example,DC=com" bsmith
To delete a user, use vastool delete. The following command deletes the bsmith user:
vastool delete bsmith
To list users, use vastool list users. The vastool list users command returns information from the local account cache. The following command lists all the users with UNIX accounts enabled:
vastool list users
This command produces output similar to the following:
pspencer:VAS:1000:1000:Pat Spencer:/home/pspencer:/bin/bash
djones:VAS:1001:1000:Dave Jones:/home/djones:/bin/bash
molsen:VAS:1002:1000:Mary Olsen:/home/molsen/bin/bash
bsmith:VAS:1003:1000:Bob Smith:/home/bsmith:/bin/bash
Managing users with Windows PowerShell
Safeguard Authentication Services includes PowerShell modules that provide a "scriptable" interface to many Safeguard Authentication Services management tasks.
Using Safeguard Authentication Services PowerShell commands you can UNIX-enable, UNIX-disable, modify, report on, and clear UNIX attributes of Active Directory users.
NOTE: You can access a customized PowerShell console from Control Center > Tools. To add Safeguard Authentication Services cmdlets to an existing PowerShell session, run Import-Module Quest.AuthenticationServices. For a complete list of available commands, see PowerShell Cmdlets.
To UNIX-enable a user, use the Enable-QasUnixUser command. The following command UNIX-enables the user bsmith in Active Directory:
Enable-QasUnixUser -Identity <domain>\bsmith
To disable a user for UNIX access use the Disable-QasUnixUser command:
Disable-QasUnixUser -Identity <domain>\bsmith
To set a particular UNIX attribute use the Set-QasUnixUser command. The following command sets the Comment (GECOS) field of the bsmith user to Bob Smith:
Set-QasUnixUser -Identity <domain>\bsmith -Gecos "Bob Smith"
To report on a user, use the Get-QASUnixUser command. The following command shows all users that start with "bsm".
Get-QasUnixUser -Identity bsm
The Safeguard Authentication Services PowerShell commands are designed to work with the Active Directory commands from Microsoft (Get-ADUser) and One Identity (Get-QADUser). You can pipe the output of these commands to any of the Safeguard Authentication Services PowerShell commands that operate on users. For example, the following command clears the UNIX attributes from the bsmith user.
Get-QADUser -Identity <domain>\bsmith | Clear-QasUnixUser
The Safeguard Authentication Services PowerShell commands are aware of the options and schema settings configured in Control Center. Scripts written using the Safeguard Authentication Services PowerShell commands work without modification in any Safeguard Authentication Services environment.
PowerShell cmdlets
Safeguard Authentication Services supports the flexible scripting capabilities of PowerShell to automate administrative, installation, and configuration tasks. A wide range of new PowerShell cmdlets are included in Safeguard Authentication Services.
Table 13: PowerShell cmdlets
|
Add-QasLicense |
Installs an Safeguard Authentication Services license file in Active Directory. Licenses installed this way are downloaded by all UNIX clients. |
|
Clear-QasUnixGroup |
Clears the UNIX identity information from group object in Active Directory. The group is no longer UNIX-enabled and will be removed from the cache on the Safeguard Authentication Services UNIX clients. |
|
Clear-QasUnixUser |
Clears the UNIX identity information from a user object in Active Directory. The user is no longer UNIX-enabled will be removed from the cache on the Safeguard Authentication Services UNIX clients. |
|
Disable-QasUnixGroup |
UNIX-disables a group and will be removed from the cache on the Safeguard Authentication Services UNIX clients. Similar to Clear-QasUnixGroup except the UNIX group name is retained. |
|
Disable-QasUnixUser |
Removes an Active Directory user‘s ability to log in on UNIX hosts. (The user will still be cached on the Safeguard Authentication Services UNIX clients.) |
|
Enable-QasUnixGroup |
Enables an Active Directory group for UNIX by giving a UNIX GID number. The GID number is automatically generated. |
|
Enable-QasUnixUser |
Enables an Active Directory user for UNIX. The required account attributes UID number, primary GID number, GECOS, login shell, and home directory are generated automatically. |
|
Get-QasConfiguration |
Returns an object representing the Safeguard Authentication Services application configuration data stored in Active Directory. |
|
Get-QasGpo |
Returns a set of objects representing GPOs with UNIX and/or macOS settings configured. This cmdlet is in the Quest.AuthenticationServices.GroupPolicy module. |
|
Get-QasLicense |
Returns objects representing the Safeguard Authentication Services product licenses stored in Active Directory. |
|
Get-QasOption |
Returns a set of configurable global options stored in Active Directory that affect the behavior of Safeguard Authentication Services. |
|
Get-QasSchema |
Returns the currently configured schema definition from the Safeguard Authentication Services application configuration. |
|
Get-QasSchemaDefinition |
Returns a set of schema templates that are supported by the current Active Directory forest. |
|
Get-QasUnixGroup |
Returns an object that represents an Active Directory group as a UNIX group. The returned object can be piped into other cmdlets such as Clear-QasUnixGroup or Enable-QasUnixGroup. |
|
Get-QasUnixUser |
Returns an object that represents an Active Directory user as a UNIX user. The returned object can be piped into other cmdlets such as Clear-QasUnixUser or Enable-QasUnixUser. |
|
Get-QasVersion |
Returns the version of Safeguard Authentication Services currently installed on the local host. |
|
Move-QasConfiguration |
Moves the Safeguard Authentication Services application configuration information from one container to another in Active Directory. |
|
New-QasAdConnection |
Creates an object that represents a connection to Active Directory using specified credentials. You can pass a connection object to most Safeguard Authentication Services cmdlets to execute commands using different credentials. |
|
New-QasArsConnection |
Creates an object that represents a connection to an Active Roles Server using the specified credentials. You can pass a connection object to most Safeguard Authentication Services cmdlets to execute commands using different credentials. |
|
New-QasConfiguration |
Creates a default Safeguard Authentication Services application configuration in Active Directory and returns an object representing the newly created configuration. |
|
Remove-QasConfiguration |
Accepts a Safeguard Authentication Services application configuration object as input and removes it from Active Directory. This cmdlet produces no output. |
|
Remove-QasLicense |
Accepts an Safeguard Authentication Services product license object as input and removes the license from Active Directory. This cmdlet produces no output. |
|
Set-QasOption |
Accepts an Safeguard Authentication Services options set as input and saves it to Active Directory. |
|
Set-QasSchema |
Accepts an Safeguard Authentication Services schema template as input and saves it to Active Directory as the schema template that will be used by all Safeguard Authentication Services UNIX clients. |
|
Set-QasUnixGroup |
Accepts a UNIX group object as input and saves it to Active Directory. You can also set specific attributes using command line options. |
|
Set-QasUnixUser |
Accepts a UNIX user object as input and saves it to Active Directory. You can also set specific attributes using command line options. |
Safeguard Authentication Services PowerShell cmdlets are contained in PowerShell modules named Quest.AuthenticationServices and Quest.AuthenticationServices.GroupPolicy. Use the Import-Module command to import the Safeguard Authentication Services commands into an existing PowerShell session.

