How this policy works
When creating a user account, Active Roles relies on this policy to assign a certain pre-Windows 2000 user logon name to the user account. The policy generates the name based on properties of the user account being created. A policy may include one or more rules that construct the name value as a concatenation of entries that are similar to those you encounter when using a Property Generation and Validation policy.
A special entry—uniqueness number—is provided to help make the policy-generated name unique. A uniqueness number entry represents a numeric value the policy will increment in the event of a naming conflict. For example, a policy may provide the option to change the new name from JSmith to J1Smith if there is an existing user account with the pre-Windows 2000 user logon name set to JSmith. If the name J1Smith is also in use, the new name can be changed to J2Smith, and so on.
The policy configuration provides the option to allow or disallow manual edits of policy-generated names. Permission to modify a policy-generated name can be restricted to the case where the name is in use by another account.
Some specific features of the policy behavior are as follows:
-
With a single rule that does not use a uniqueness number, Active Roles simply attempts to assign the generated name to the user account. The operation may fail if the generated name is not unique, that is, the same pre-Windows 2000 user logon name is already assigned to a different user account. If the policy allows manual edits of policy-generated names, the name can be corrected by the operator who creates the user account.
-
With multiple rules or with a rule that uses a uniqueness number, Active Roles adds a button at the client side, next to the User logon name (pre-Windows 2000) field on the user creation and modification forms.
-
To generate a name, the client user (operator) must click that button, which is also the case where the generated name is in use. Clicking the Generate button applies a subsequent rule or increases the uniqueness number by one, thereby allowing the name to be made unique.
-
The policy defines a list of characters that are unacceptable in pre-Windows 2000 user logon names. The following characters are not allowed: " / \ [ ] : ; | = , + * ? < >
-
The policy causes Active Roles to deny processing of operation requests that assign the empty value to the pre-Windows 2000 user logon name.
-
When checking user accounts for policy compliance (see later in this document), Active Roles detects, and reports of, the pre-Windows 2000 user logon names that are set up not as prescribed by the user logon name generation policy.
How to configure a User Logon Name Generation policy
To configure a User Logon Name Generation policy, select User Logon Name Generation on the Policy to Configure page in the New Provisioning Policy Object Wizard or in the Add Provisioning Policy Wizard. Then, click Next to display the User Logon Name (pre-Windows 2000) Generation Rules page.
Figure 58: New Provisioning Policy Object Wizard

On the User Logon Name (pre-Windows 2000) Generation Rules page, you can set up a list of generation rules. Each entry in the list includes the following information:
-
Priority: The policy applies generation rules in the order of their priority, as they stand in the list: first read, first applied.
-
Rule: Syntax that defines the rule.
-
Uniqueness Number: Displays Yes or No, indicating whether the rule includes a uniqueness number entry.
You can use these buttons manage the list of rules:
-
Add: Opens the Configure Value dialog, discussed in How to configure a Property Generation and Validation policy. Use that dialog to configure a value for the ‘Logon Name (pre-Windows 2000)’ must be condition, in the same way as you do when configuring a Property Generation and Validation policy. For more information, see Configuring a logon name generation rule.
-
Remove: Deletes the rules you select from the list.
-
View/Edit: Opens the Configure Value dialog for the rule you select from the list. Modify the selected rule by managing the list of entries in that dialog.
-
Up and Down: Change the order of rules in the list. Click Up or Down to move a selected rule higher or lower in the list to give the rule a higher or lower priority, respectively.
-
Advanced: Set certain options that apply to all rules in the list, such as the maximum length of the generated name, whether to format the name as the uppercase or lowercase string, the scope where you want the generated name to be unique, and the characters to be excluded from the generated names.
By selecting the Allow manual edits of pre-Windows 2000 logon name check box, you authorize the operator who creates or updates the user account to make changes to the policy-generated name. If this check box is cleared, Active Roles displays the User logon name (pre-Windows 2000) field as read-only on the user creation and modification forms.
By selecting the Always option, you authorize the operator to modify the pre-Windows 2000 logon name at their discretion. With the Only if a unique name cannot be generated by this policy option, you limit manual changes to the situation where a unique name cannot be generated in accordance with the policy rules.
Configuring a logon name generation rule
To configure a generation rule, click Add beneath the Generation rules list. This displays the Configure Value dialog, prompting you to set up a value for the ‘Logon Name’ must be condition.
To start configuring a value, click Add in the Configure Value dialog. This displays the Add Entry window.
A value is a concatenation of one or more entries. In the Add Entry window, you can select the type of the entry to add, and then configure the entry. The following table summarizes the available types of entries.
Table 20: Types of entries
|
Text |
Adds a text string to the value. |
|
Uniqueness Number |
Adds a numeric value the policy will increment in the event of a naming conflict. |
|
User Property |
Adds a selected property (or a part of a property) of the user account to which the policy will assign the logon name. |
|
Parent OU Property |
Adds a selected property (or a part of a property) of an Organizational Unit in the hierarchy of containers above the user account to which the policy will assign the logon name. |
|
Parent Domain Property |
Adds a selected property (or a part of a property) of the domain of the user account to which the policy will assign the logon name. |
Instructions on how to configure an entry depend on the type of the entry. You can use the instructions outlined in How to configure a Property Generation and Validation policy to configure an entry of any of these types:
The following subsection elaborates on the Uniqueness Number entry.
Entry type: Uniqueness Number
When you select Uniqueness Number under Entry type in the Add Entry window, the Entry properties area looks as follows.
Figure 59: Entry Type: Uniqueness Number
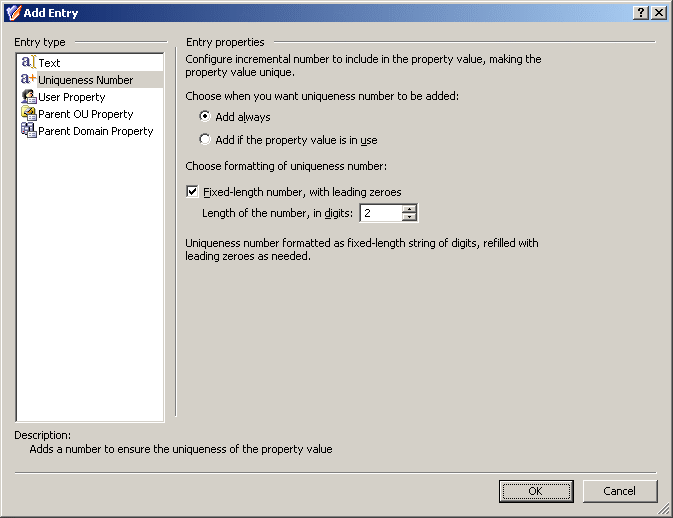
Using this entry type, you can add an entry that represents a number the policy will increment in the event of a naming conflict.
First, you need to choose when you want the policy to employ this entry. You have the following options:
-
Add always: The value includes this entry regardless of whether or not the policy encounters a naming conflict when applying the generation rule.
-
Add if the property value is in use: The policy adds this entry to the value in the event of a naming conflict; otherwise the value does not include this entry.
Next, you can specify how you want the entry to be formatted:
-
To have the entry formatted as a variable-length string of digits, clear the Fixed-length number, with leading zeroes check box. In most cases, this will result in a single-digit entry.
-
To have the entry formatted as a fixed-length string of digits, select the Fixed-length number, with leading zeroes check box, and then specify the number of digits you want the string to include. This will result in an entry prefixed with the appropriate number of zeroes, such as 001, 002, 003, and so on.
When you are done configuring an entry, click OK to close the Add Entry window. The entry is added to the Configure Value dialog.


