TLS-encrypted message transfer
Encrypting log messages with TLS
Configuring TLS on the syslog-ng clients
Configuring TLS on the syslog-ng server
Mutual authentication using TLS
Configuring TLS on the syslog-ng clients
Secure logging using TLS
The syslog-ng application can send and receive log messages securely over the network using the Transport Layer Security (TLS) protocol using the network() and syslog() drivers.
This chapter describes how to use TLS encryption when using the standard syslog protocols, that is, the network() and syslog() drivers, for example, to forward log messages between two syslog-ng nodes, or to send log data to syslog-ng Store Box or another log server. Other destinations that support TLS-encryption are not discussed in this chapter (for example, http()).
TLS uses certificates to authenticate and encrypt the communication, as illustrated on the following figure:
Figure 18: Certificate-based authentication
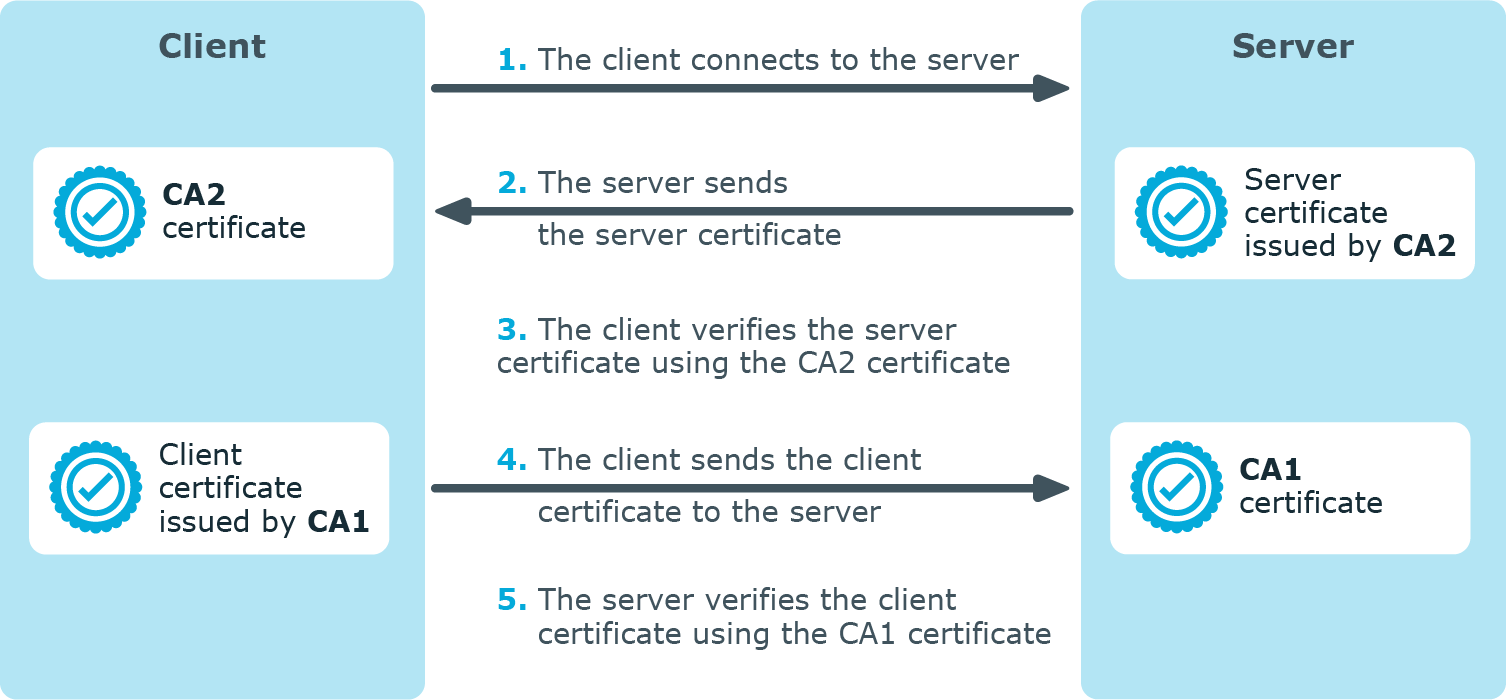
The client authenticates the server by requesting its certificate and public key. Optionally, the server can also request a certificate from the client, thus mutual authentication is also possible.
In order to use TLS encryption in syslog-ng, the following elements are required:
-
A certificate on the syslog-ng server that identifies the syslog-ng server.
-
The certificate of the Certificate Authority that issued the certificate of the syslog-ng server (or the self-signed certificate of the syslog-ng server) must be available on the syslog-ng client.
When using mutual authentication to verify the identity of the clients, the following elements are required:
-
A certificate must be available on the syslog-ng client. This certificate identifies the syslog-ng client.
-
The certificate of the Certificate Authority that issued the certificate of the syslog-ng client must be available on the syslog-ng server.
Mutual authentication ensures that the syslog-ng server accepts log messages only from authorized clients.
For more information about configuring TLS communication in syslog-ng, see Encrypting log messages with TLS.
For more information about TLS-related error messages, see Error messages.
Encrypting log messages with TLS
This section describes how to configure TLS encryption in syslog-ng. For the concepts of using TLS in syslog-ng, see Secure logging using TLS.
Configuring TLS on the syslog-ng clients
Purpose:
Complete the following steps on every syslog-ng client host. Examples are provided using both the legacy BSD-syslog protocol (using the network() driver) and the new IETF-syslog protocol standard (using the syslog() driver):
Steps:
-
Copy the CA certificate (for example, cacert.pem) of the Certificate Authority that issued the certificate of the syslog-ng server (or the self-signed certificate of the syslog-ng server) to the syslog-ng client hosts, for example, into the /opt/syslog-ng/etc/syslog-ng/ca.d directory.
Issue the following command on the certificate: openssl x509 -noout -hash -in cacert.pem The result is a hash (for example, 6d2962a8), a series of alphanumeric characters based on the Distinguished Name of the certificate.
Issue the following command to create a symbolic link to the certificate that uses the hash returned by the previous command and the .0 suffix.
ln -s cacert.pem 6d2962a8.0
-
Add a destination statement to the syslog-ng configuration file that uses the tls( ca-dir(path_to_ca_directory) ) option and specify the directory using the CA certificate. The destination must use the network() or the syslog() destination driver, and the IP address and port parameters of the driver must point to the syslog-ng server.
Example: A destination statement using TLS
The following destination encrypts the log messages using TLS and sends them to the 6514/TCP port of the syslog-ng server having the 10.1.2.3 IP address.
destination demo_tls_destination { network("10.1.2.3" port(6514) transport("tls") tls( ca_dir("/opt/syslog-ng/etc/syslog-ng/ca.d")) ); };A similar statement using the IETF-syslog protocol and thus the syslog() driver:
destination demo_tls_syslog_destination { syslog("10.1.2.3" port(6514) transport("tls") tls(ca_dir("/opt/syslog-ng/etc/syslog-ng/ca.d")) ); }; -
Include the destination created in Step 2 in a log statement.
Caution: The encrypted connection between the server and the client fails if the Common Name or the subject_alt_name parameter of the server certificate does not contain the hostname or the IP address (as resolved from the syslog-ng clients and relays) of the server.
Do not forget to update the certificate files when they expire.

