Assigning E-Business Suite entitlements directly to a user account
To react quickly to special requests, you can assign entitlements directly to a user account. You cannot directly assign permissions that have the Only use in IT Shop option set.
To assign entitlements directly to a user account
-
In the Manager, select the Oracle E-Business Suite > User accounts category.
-
Select the user account in the result list.
-
Select the Assign permission task.
The top area of the form displays all entitlements that have already been assigned, together with their validity periods. The overview shows the entitlements that have been assigned both directly and indirectly. For direct assignments, an Active from (direct) date is set; indirect assignments do not have a direct validity date.
To assign an entitlement to the user account
-
Click Add.
-
Select the entitlement you want to assign from the E-Business Suite Entitlement menu.
-
In the Active from (direct) input field, enter the first date from on the direct entitlement assignment is valid.
-
(Optional) In the Active to (direct) input field, enter the last date on which the direct entitlement assignment is valid.
-
(Optional) Add further entitlements.
- Save the changes.
To edit a direct entitlement assignment
-
In the overview, select the direct entitlement assignment that you want to edit.
-
Change the values in the input fields Active from (direct), Active to (direct), or Description.
- Save the changes.
Only direct assignments can be edited. If you select and edit an indirect assignment in the overview, this creates an additional direct assignment.
Entitlement assignments cannot be deleted. Instead, there are two options for indicating that a direct assignment is no longer valid.
-
Enter the current date as the expiration date of the entitlement.
Select this option, for example, if an entitlement assignment will become invalid on a defined date in the future.
- OR -
-
Delete the entitlement assignment.
Select this option, for example, if an inherited entitlement assignment also exists alongside the direct assignment, and you want the inherited entitlement assigned to replace the direct assignment.
To set the expiration date for a direct entitlement assignment
-
In the overview, select the direct entitlement assignment that you no longer want to be effective.
-
Next to the input field Active to (direct), click ....
-
Click Today or define a different expiration date.
- Save the changes.
To remove a direct entitlement assignment
-
In the overview, select the direct entitlement assignment that you no longer want to be effective.
-
Click Delete.
- Save the changes.
The first and last validity date of the direct assignment (Active from (direct) and Active to (direct)) are deleted. The final validity date (Active to (effective)) is recalculated. If no further valid assignments exist, the final validity date is set to a date in the past and XOrigin is assigned the value 16.
Detailed information about this topic
Related topics
Validity period of permission assignments
You can limit the time for which permission assignments are valid. A user account can receive permissions by direct assignment as well as through a variety of different inheritance paths. Each of these assignments can have a different validity period. One Identity Manager uses all validity periods to determine the actual validity period effective at the current time. This calculation considers all assignments with OriginIndirect = 0.
Table 25: Properties of a permission assignment
|
Active from (effective) |
First date from which the assignment is valid. This date is calculated from all assignments (direct and indirect). |
|
Active to (effective) |
Last date on which the assignment is valid This date is calculated from all assignments (direct and indirect). If no date is specified, the assignment is unlimited. |
|
Active from (direct) |
First date from which the direct assignment is valid |
|
Active to (direct) |
Last date on which the direct assignment is valid If no date is specified, the assignment is unlimited. |
|
Indirect |
Specifies whether this assignment maps an indirect permission from the target system. You cannot edit indirect assignments in One Identity Manager. |
|
Description |
Text field for additional explanation. |
Calculation of the effective validity period
In One Identity Manager, one user account-permission combination can have multiple assignments with different validity periods. However, only the effective assignment is transferred to Oracle E-Business Suite. One Identity Manager calculates the effective validity period from all the assignments. The different assignment types are incorporated into the calculation as follows:
Table 26: Determine validity period
|
Direct assignment |
Active from (direct) and Active to (direct) |
|
Request |
Validity period of the request when the Valid from date of the request has been reached or exceeded.
For unlimited requests, 01.01.1900 is entered at the first validity date. |
|
assignment request |
Validity period of the request when the Valid from date of the request has been reached or exceeded.
For unlimited requests, 01.01.1900 is entered at the first validity date. |
|
Inheritance by department, location, cost center, or business role (not an assignment request) |
Unlimited only
The date of the assignment is set as the first date of the validity. |
|
Inheritance through dynamic role |
Unlimited only
The date of the assignment is set as the first date of the validity. |
|
Inheritance by system role |
Unlimited only
The date of the assignment is set as the first date of the validity. |
The effective assignment is controlled by a schedule.
-
Active from (effective): earliest initial validity date of all the assignments
-
Active to (effective): latest last validity date of all limited assignments
If the assignment is unlimited, Active to (effective) is empty.
Detailed information about this topic
Related topics
Effectiveness of entitlement assignments
When E-Business Suite entitlements are assigned to user accounts an employee may obtain two or more groups that are not permitted in this combination. To prevent this, you can declare mutually exclusive entitlements. To do this, you specify which of the two entitlements should become active on user accounts if both are assigned.
It is possible to assign an excluded entitlements directly, indirectly, or by IT Shop request at any time. One Identity Manager determines whether the assignment is effective.
NOTE:
- You cannot define a pair of mutually exclusive entitlements. This means that the definition "Entitlement A excludes entitlement B" AND "Entitlement B excludes entitlement A" is not permitted.
- Each entitlement to be excluded from another entitlement must be declared separately. Exclusion definitions cannot be inherited.
The effectiveness of the assignments is stored in the EBSUserInResp table using the ValidTo and XOrigin columns, and in the BaseTreeHasEBSResp table, using the XIsInEffect column.
Example of the effectiveness of entitlements
- The entitlements A, B, and C are defined in an E-Business Suite system.
- Entitlement A is assigned through the "Marketing" department, entitlement B through the "Finance" department, and entitlement C through the "Control group" business role.
Clara Harris has a user account in this system. She primarily belongs to the "marketing" department. The "Control group" business role and the "Finance" department are assigned to her secondarily. Without an exclusion definition, the user account obtains all the entitlements A, B, and C.
You need to use a suitable method to ensure that a employee cannot be assigned the entitlements A and B at the same time. This means that entitlements A and B are mutually exclusive. A user with entitlement C also cannot be assigned entitlement B. Entitlements B and C are therefore mutually exclusive.
Table 27: Definition of excluded entitlements (EBSRespExclusion table)
|
Entitlement A |
|
|
Entitlement B |
Entitlement A |
|
Entitlement C |
Entitlement B |
Table 28: Effective assignments
|
Ben King |
Marketing |
Entitlement A |
|
Jan Bloggs |
Marketing, finance |
Entitlement B |
|
Clara Harris |
Marketing, finance, control group |
Entitlement C |
|
Jenny Basset |
Marketing, control group |
Entitlement A
Entitlement C |
Only the entitlement C assignment is in effect for Clara Harris and is published in the target system. If Clara Harris leaves the "control group" business role at a later date, entitlement B also takes effect.
Entitlements A and C are in effect for Jenny Basset because no exclusions are defined between these two entitlements. If this should not be allowed, define a further exclusion for entitlement C.
Table 29: Excluded entitlements and effective assignments
|
Jenny Basset
|
Marketing |
Entitlement A |
|
Entitlement C
|
|
Control group |
Entitlement C |
Entitlement B
Entitlement A |
Prerequisites
-
The QER | Structures | Inherite | GroupExclusion configuration parameter is set.
In the Designer, set the configuration parameter and compile the database.
NOTE: If you disable the configuration parameter at a later date, model components and scripts that are not longer required, are disabled. SQL procedures and triggers are still carried out. For more information about the behavior of preprocessor relevant configuration parameters and conditional compiling, see the One Identity Manager Configuration Guide.
-
Mutually exclusive entitlements belong to the same E-Business Suite system.
To exclude entitlements
-
In the Manager, select the Oracle E-Business Suite > entitlements category.
-
Select an entitlement in the result list.
-
Select the Exclude E-Business Suite entitlements task.
-
In the Add assignments pane, assign entitlements that are mutually exclusive to the entitlement.
- OR -
In the Remove assignments pane, remove the entitlements that are no longer mutually exclusive.
- Save the changes.
Related topics
Inheritance of E-Business Suite entitlements based on categories
In One Identity Manager, user accounts can selectively inherit entitlements. To do this, entitlements, and user accounts are divided into categories. The categories can be freely selected and are specified using a mapping rule. Each category is given a specific position within the template. The mapping rule contains different tables. Use the user account table to specify categories for target system dependent user accounts. In the other tables, enter your categories for the permissions. Each table contains the category positions position 1 to position 63.
Every user account can be assigned to one or more categories. Each entitlement can also be assigned to one or more categories. If at least one of the category items between the user account and the assigned entitlement is the same, the entitlement is inherited by the user account. If the entitlement or the user account is not classified in a category, the entitlement is also inherited by the user account.
NOTE: Inheritance through categories is only taken into account when entitlements are assigned indirectly through hierarchical roles. Categories are not taken into account when entitlements are directly assigned to user accounts.
Table 30: Category examples
| 1 |
Default user |
Default entitlements |
| 2 |
System users |
System user entitlements |
| 3 |
System administrator |
System administrator entitlements |
Figure 2: Example of inheriting through categories.
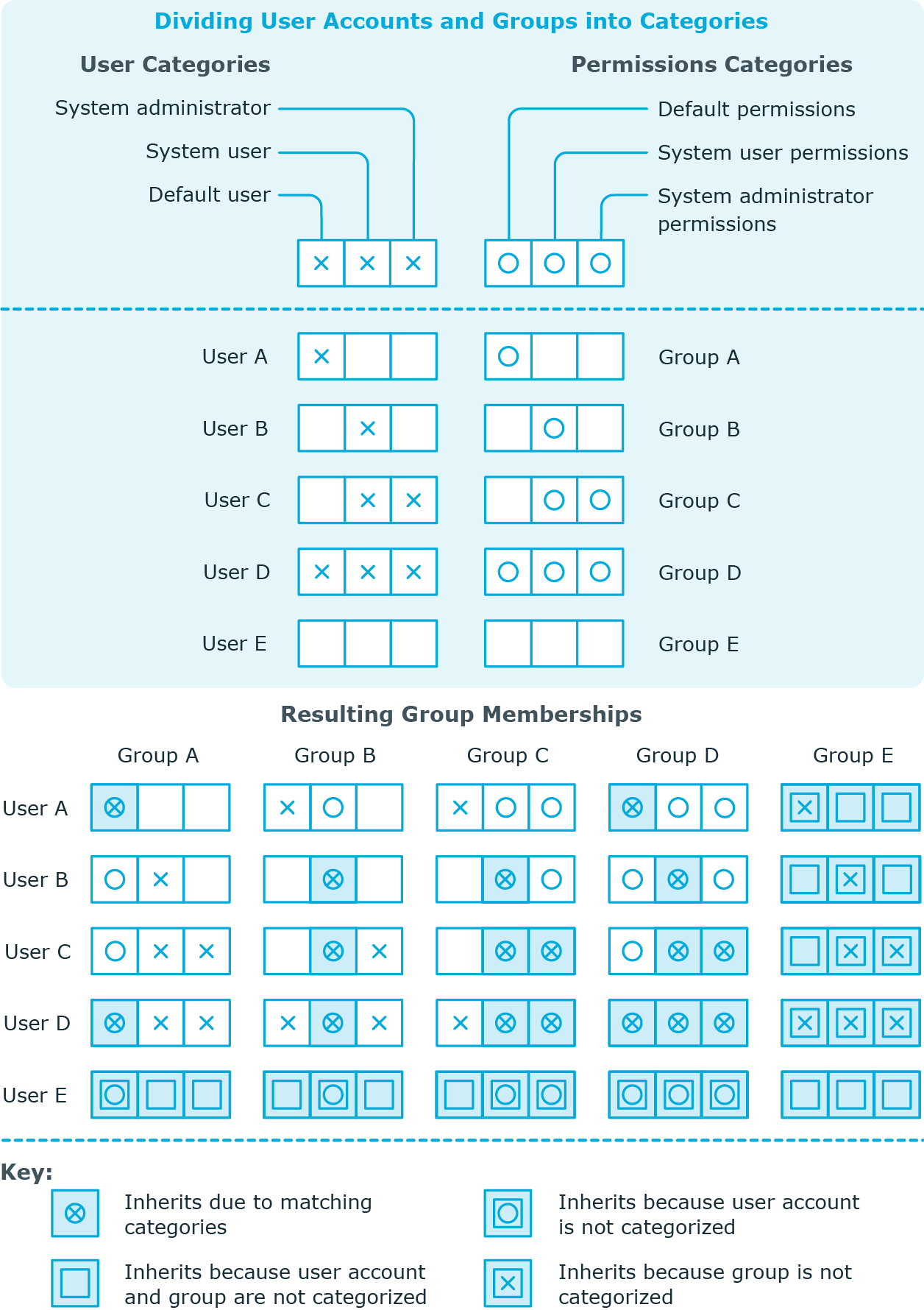
To use inheritance through categories
- Define the categories in the E-Business Suite system.
- Assign categories to user accounts through their main data.
- Assign categories to entitlements through their main data.
Related topics

