Finding non-compliant authorizations
SAP authorizations are verified on the basis of the SAP applications permitted for an SAP user account and the associated authorization objects. To determine whether potentially dangerous authorizations are assigned within the company, define SAP functions that group together the SAP applications and authorization objects to be checked. One Identity Manager compares all authorization objects assigned to single profiles with the authorization definition in the SAP function. This way, it determines all SAP roles and profiles that have exactly these authorization objects assigned through the single profiles.
The TargetSystem | SAPR3 | SAPRights | TestWithoutTCD configuration parameter is evaluated by authorization checks. The configuration parameter defines whether only the authorization objects or also the SAP applications are to be taken into account during the authorization check.
The TestWithoutTCD configuration parameter is not set (default)
The following rules apply to the authorization check:
An SAP role or SAP profile matches an SAP function when
- It has at least one of the SAP applications defined in the SAP function.
- It has all the authorization objects for this SAP application.
- It has all the different authorization object function elements.
- At least one of the instances is defined exactly the same function element.
An SAP role matches an SAP function if the SAP profile of this SAP role contains one the SAP applications defined in the SAP function. The SAP profile must have all this SAP application's authorization objects to do this. If a list of different instances is defined for the authorization object, the SAP profile matches the SAP function if it has at least one of these instances.
The TestWithoutTCD configuration parameter is set
SAP applications are not taken into account during the authorization check. In this case, the following rules apply for authorization checking:
An SAP role or SAP profile matches an SAP function when
- It has all the authorization objects for all SAP applications.
- It has all the different authorization object function elements.
- At least one of the instances is defined exactly same function element.
Example of authorization checking
An SAP function is defined with the following SAP applications, authorization objects, and function elements.
Figure 2: Authorization definition
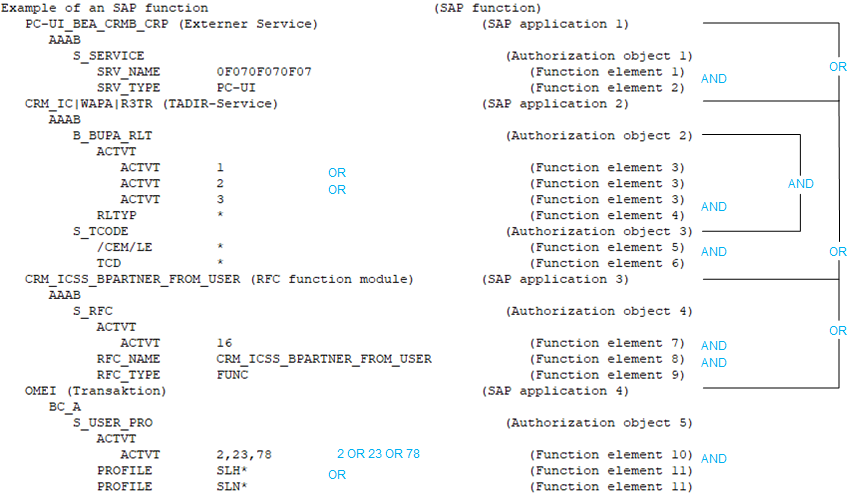
If the configuration parameter is not set, all SAP roles and SAP profiles with the authorizations found by the SAP function shown are listed here:
-
SAP application 1 with authorization object 1 and function element 1 AND 2
- OR -
-
SAP application 2 with authorization object 2 and function element 3 with the instance 1 OR 2 OR 3 AND function element 4
- AND -
with authorization object 3 and function element 5 AND 6
- OR -
-
SAP application 3 with authorization object 4 and function element 7 AND 8 AND 9
- OR -
-
SAP application 4 with authorization object 5 and function element 10 with the instance 2 OR 23 OR 78 AND function element 11 with the instance SLH* OR SLN*.
If the configuration parameter is set, all SAP roles and SAP profiles with the authorizations found by the SAP function are listed here:
-
Authorization object 1 and function element 1 AND 2
- AND -
-
Authorization object 2 and function element 3 with the instance 1 OR 2 OR 3 AND function element 4
- AND -
-
Authorization object 3 and function element 5 AND 6
- AND -
-
Authorization object 4 and function element 7 AND 8 AND 9
- AND -
-
Authorization object 5 and function element 10 with the instance 2 OR 23 OR 78 AND function element 11 with the instance SLH* OR SLN*.
Examples of SAP functions
If you create an authorization definition, you need to think about which authorization combinations are not compliant. You can differentiate between two use cases:
- Find all SAP roles and profiles with invalid combinations of authorizations.
Create an SAP function for authorizations that cannot occur together with an SAP role or an SAP profile. The authorization test identifies all SAP roles and profiles that have this non-compliant combination of authorizations.
- Find all employees that have obtain non-compliant combinations of authorizations through their SAP user accounts.
Create SAP functions for compliant authorizations or combinations of authorizations. Create compliance rules for mutually exclusive SAP functions. The compliance check finds all employees that combine such non-compliant authorization combinations through their SAP user accounts.
Example for use case 1
A company has changed its policies on compliant SAP authorizations. Now the new policies must be tested to see if existing authorizations (SAP roles and profiles) comply. SAP roles and profiles with non-compliant combinations of authorizations must be identified so that they can be modified to meet the new requirements.
An SAP function is created for each non-compliant authorization combination.
Table 5: Example of an authorization definition
|
A |
TR |
BO2 |
ACTVT |
* |
|
TR |
BO2 |
Class |
* |
|
TR |
BO3 |
ACTVT |
01, 02 |
|
RF |
BO5 |
ACTVT |
* |
|
RF |
BO5 |
RLTYP |
R* |
|
B |
TR |
BO3 |
ACTVT |
* |
|
TR |
BO4 |
ACTVT |
02, 03, 07 |
|
TR |
BO4 |
Class |
* |
The following SAP roles are available:
Table 6: Defined SAP roles
|
R1 |
TR |
BO1 |
ACTVT |
* |
|
TR |
BO1 |
Class |
* |
|
TR |
BO3 |
ACTVT |
* |
|
TR |
BO4 |
ACTVT |
01, 02 |
|
TR |
BO4 |
Class |
DEF* |
|
R2 |
TR |
BO2 |
ACTVT |
* |
|
TR |
BO2 |
Class |
* |
|
TR |
BO3 |
ACTVT |
* |
|
R3 |
TR |
BO4 |
ACTVT |
03, 07 |
|
TR |
BO4 |
Class |
* |
|
R4 |
RF |
BO5 |
ACTVT |
03 |
|
RF |
BO5 |
RLTYP |
* |
SAP roles are found that match the SAP function during authorization testing.
Authorization test results:
-
SAP function: B
Configuration parameter TestWithoutTCD: set or not set
The configuration parameter does not affect the result of the authorization test because only one SAP application is used in the SAP function.
Open SAP role: R1
The role R1 has all the authorization objects and fields named in the SAP function and at least one field characteristic.
Role R2 is missing authorization object BO4. Therefore it does not match the SAP function.
Role R3 is missing authorization object BO3. Therefore it does not match the SAP function.
The role R4 is missing authorization object BO3 and BO4. Therefore it does not match the SAP function.
-
SAP function: A
Configuration parameter TestWithoutTCD: not set
Open SAP roles: R2, R4
The role R2 has all the authorization objects, fields, and characteristics named in SAP application TR.
The role R4 has all the authorization objects, fields, and characteristics named in SAP application RF.
The role R1 is missing the authorization object BO2 or BO5. Therefore it does not match the SAP function.
The role R3 does not have any of the named authorization objects. Therefore it does not match the SAP function.
-
SAP function: A
Configuration parameter TestWithoutTCD: set
Open SAP roles: R2, R4
The role R1 is missing authorization object BO2 and BO5. Therefore it does not match the SAP function.
Role 2 is missing authorization object BO5. Therefore it does not match the SAP function.
The role R3 does not have any of the named authorization objects. Therefore it does not match the SAP function.
The role R4 is missing authorization object BO2 and BO3. Therefore it does not match the SAP function.
The SAP role R3 complies with the new policies and can still be used. The roles R1, R2, and R4 must be modified to comply to the new policies. If an authorization test is compliant without taking the SAP applications into account, only role R1 must be modified.
Example for use case 2
Now you need to run a test to ascertain which SAP user accounts do not conform to the new policies. To do this, you have to create compliance rules for the SAP functions.
Table 7: SAP user accounts used
|
User 1 |
K1 |
R1 |
BO1 | ACTVT {*}
BO1 | CLASS {*}
BO3 | ACTVT {*}
BO4 | ACTVT {01, 02}
BO4 | CLASS {DEF*} |
|
User 2 |
K2 |
R2, R3 |
BO2 | ACTVT {*}
BO2 | CLASS {*}
BO3 | ACTVT {*}
BO4 | ACTVT {03, 07}
BO4 | CLASS {*} |
|
User 3 |
K3 |
R2 |
BO2 | ACTVT {*}
BO2 | CLASS {*}
BO3 | ACTVT {*} |
|
User 3 |
K4 |
R3 |
BO4 | ACTVT {03, 07}
BO4 | CLASS {*} |
|
User 5 |
K5 |
R3 |
BO4 | ACTVT {03, 07}
BO4 | CLASS {*} |
The SAP roles R2 and R3 are assigned to user account K2. The user account obtains all the authorizations from both these roles. However, according to the new policies, an employee cannot own the authorizations BO3 and BO4 (SAP function B) at the same time. A compliance rule is created for this, which finds all employees matching the SAP function B (rule C1). Since neither role R2 nor role R3 matches this SAP function, a rule violation is not found.
In order for One Identity Manager to acknowledge the rule violation, SAP functions must be created for the conflicting authorization objects. As a result. the SAP functions that cause a rule violation are combined into a compliance rule.
Table 8: More SAP functions
|
B |
TR |
BO3 |
ACTVT |
* |
|
TR |
BO4 |
ACTVT |
02, 03, 07 |
|
TR |
BO4 |
Class |
* |
|
C |
TR |
BO3 |
ACTVT |
* |
|
D |
TR |
BO4 |
ACTVT |
02, 03, 07 |
|
TR |
BO4 |
Class |
* |
Table 9: Compliance rules
|
CR1 |
Employee owns SAP function B. |
User 1 |
|
CR2 |
The employee owns the SAP function C AND the employee own the SAP function D. |
User 1
User 2
User 3 |
User 5 does not violate the compliance rule. The SAP role R3 matches the SAP function D but this only leads to a rule violation in combination with the SAP function C.
Related topics
Setting up SAP functions
You can create function definitions, function instances, and variable sets for SAP functions. A function definition contains the authorization definition as well as general main data. An authorization definition consists of at least one SAP application. A least one authorization object belongs to an SAP application. Each authorization object consists of at least one function element (activity or authorization field) with concrete instances. Instances are given as single values or as upper and lower scope limits. Function elements can be listed more than once per authorization object.
You can use an SAP function for different instances. Use variables in the authorization definition to do this. Fixed variable values are grouped in variable sets and used in the function instances.
Notes on authorization definitions
Take the following advice into account when you create an authorization definition in the authorization editor.
- Click + to add an additional value for the ACTVT element to an authorization object. You can also write several permitted values for ACTVT elements as a comma delimited list.
- To add an additional value for another function element (for example, CLASS) to an authorization object, click C next to this function element. The permitted values of this function element cannot be entered as a comma delimited list. They must always appear as separate entries in the authorization definition.
- Authorization objects cannot be added more than once to an authorization definition. if you want to run a function test on the same authorization object with different instances, create a separate SAP function for each instance. Combine these SAP function in a compliance rule.
Detailed information about this topic
Related topics

