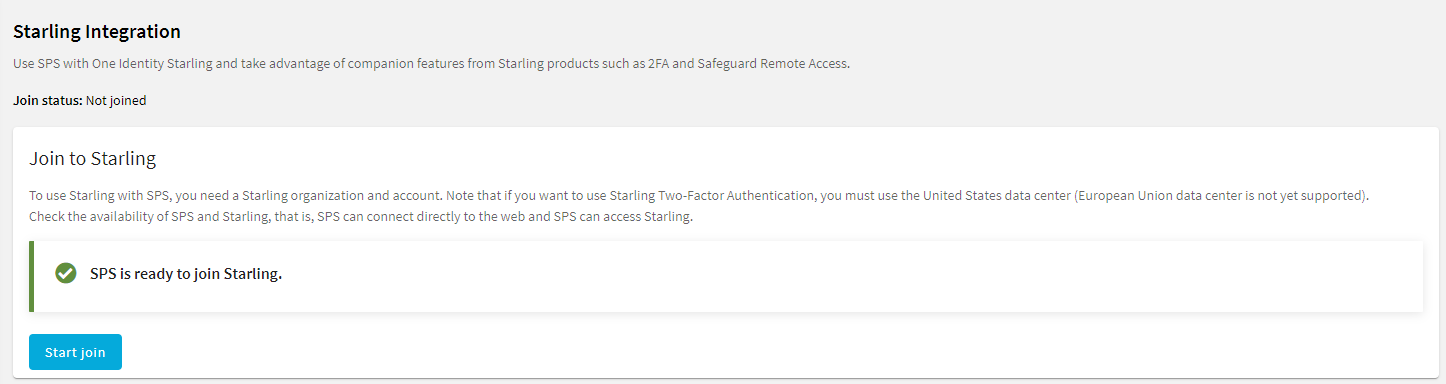
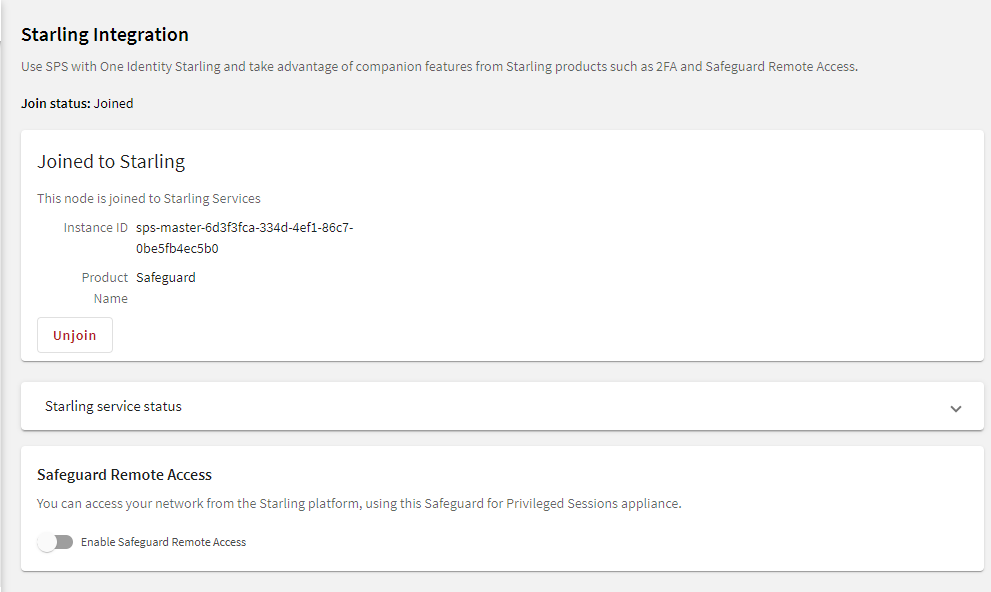
One Identity Starling helps to combine products from the One Identity line to create a secure and customizable cloud service. For more information, see the Starling technical documentation.
If you are using a Starling 2FA plugin, (that is, you have uploaded it to Basic Settings > Plugins and then configured it at Policies > AA Plugin Configurations) and the SPS node is joined to One Identity Starling, you do not have to specify api_key and api_url in the Starling 2FA plugin configuration. This configuration method is more secure.