Forwarding claims to federated applications
|
1 |
|
3 |
In the navigation bar, click Claim Mapping. |
|
4 |
|
5 |
Complete the Name of the claim to send to the application. For OpenID Connect/OAuth 2.0 applications, you can select from a preset list of standard claims. |
|
6 |
Rule Processing Mode: Mapping rules can be applied to users who have a certain role. You can use the Rules Processing Mode setting to determine whether only the first rule matching the user(s) should apply, or whether all rules should apply. |
|
• |
Use first rule matched - return the result of the first rule where the user is a member of the role set on the rule. |
|
• |
Use all rules matched - return the results of all rules where the user is a member of the role set on the rule. |
|
7 |
In the Claim Rule box: |
|
b |
Choose the Claim mapping mode: |
|
• |
If you want the claim to be derived from a claim from an identity provider, choose Map claim to user attribute. |
|
• |
If you want Cloud Access Manager to set the claim to a constant value, choose Map claim to static value. |
|
8 |
If you have chosen Map claim to static value, enter that value in the box provided. If you have chosen Map claim to user attribute, choose the attribute holding the information you want to send as a claim from the dropdown. To add more attributes to the list displayed in the dropdown, click Manage User Attributes. 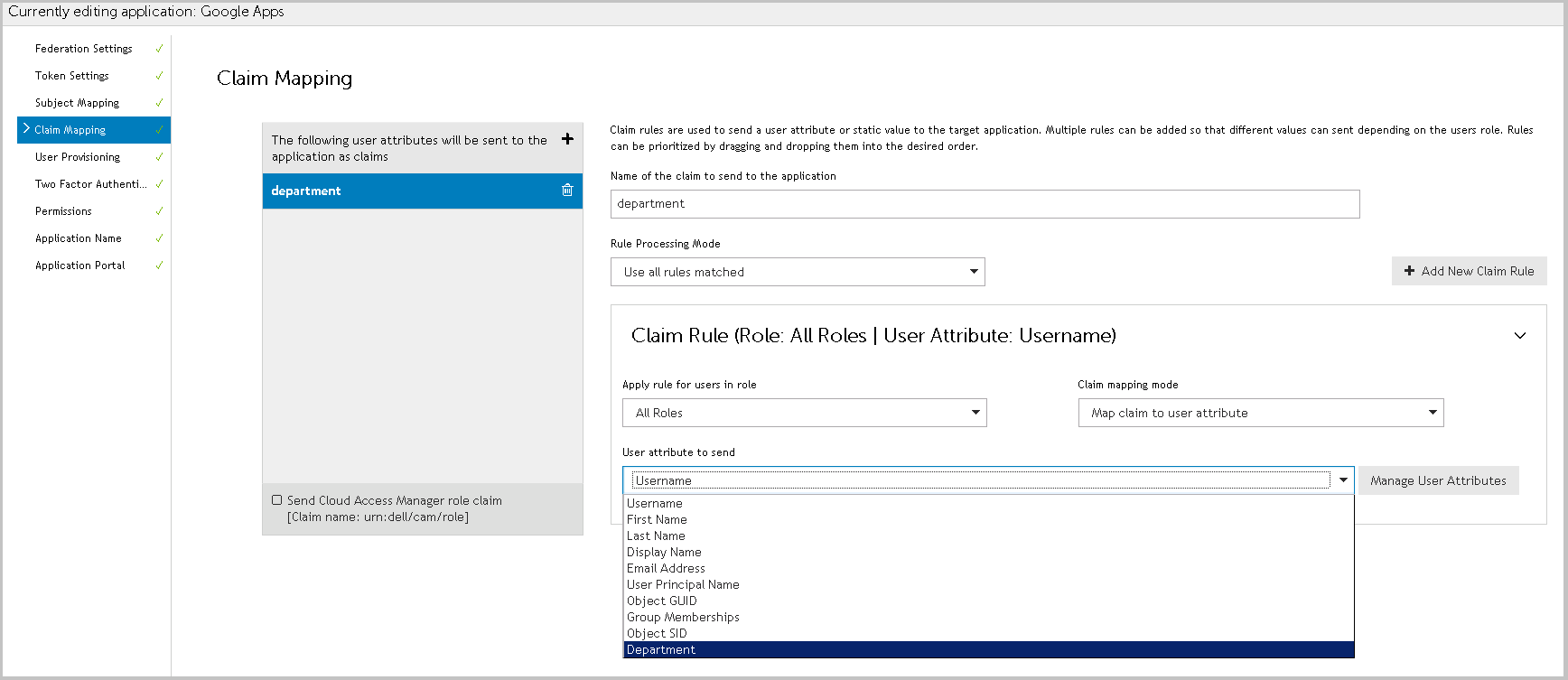 |
|
9 |
If the same claim can be derived from different attributes depending on the user's role, you can add another Claim Rule by clicking the Add New Claim Rule button. If you have defined multiple Claim Rules you can order them by dragging and dropping the rules into the correct position, so that the correct rule is processed for users in a given role. |
|
11 |
You can send the names of the user's Cloud Access Manager roles to the application as claims. To do this, select the Send Cloud Access Manager role claim box at the bottom of the claim list panel. |
|
NOTE: If you select Group Memberships for a claim rule and you are using Active Directory the user's Primary Group is not returned. In default installations, the user's Primary Group is Domain Users. The Primary Group is not returned because the claim rule returns the values in the memberOf attribute and the Primary Group is determined using the primaryGroupID attribute. |
Adding HTTP headers to proxy applications
|
1 |
|
3 |
In the navigation bar, click Header Mapping. |
|
4 |
Follow the instructions in Forwarding claims to federated applications, where you see Claim Mapping replace this with Header Mapping. |
