When creating a user in the ACF2 database, the following LDAP attributes must be defined:
-
objectclass
-
acf2lid
-
userPassword
When creating a user in the ACF2 database, the following LDAP attributes must be defined:
objectclass
acf2lid
userPassword
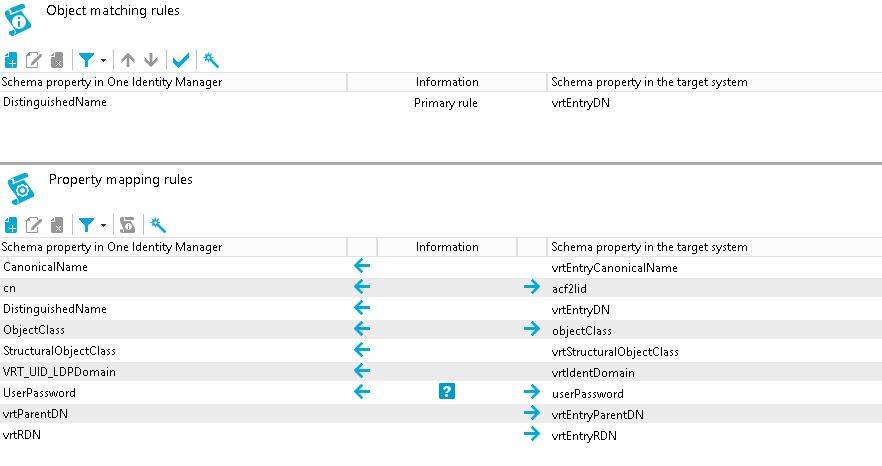
CanonicalName ← vrtEntryCanonicalName
vrtEntryCanonicalName is a virtual property, set to the canonical name of the object in the connector.
Sample value:
COM/MYCOMPANY/MAINFRAME2/LIDS/USER1234
cn ←→ acf2lid
On the ACF2 system, acf2lid is the user ID.
Sample value:
USER1234
DistinguishedName ← vrtEntryDN
vrtEntryDN is a virtual property, set to the DN of the object in the connector. Once this mapping rule has been created, edit the mapping rule by clicking on it. Select the Force mapping against direction of synchronization check box.
Sample value:
acf2lid=USER1234,acf2admingrp=lids,host=mainframe2,o=mycompany,c=com
ObjectClass ←→ objectClass
The objectClass attribute (multi-valued) on the ACF2 system. Select the Ignore case sensitivity check box.
Sample value:
ACF2LID
StructuralObjectClass ← vrtStructuralObjectClass
vrtStructuralObjectClass on the ACF2 system defines the single object class for the object type.
Sample value:
ACF2LID
UID_LDPDomain ← vrtIdentDomain
Create a fixed value property variable on the ACF2 side called vrtIdentDomain that is set to the value $IdentDomain$. Map this to UID_LDPDomain. This will cause a conflict and the Property Mapping Rule Conflict Wizard opens automatically.
To resolve the conflict
In the Property Mapping Rule Conflict Wizard, select the first option and click OK.
On the Select an element page, select Ident_Domain and click OK.
Confirm the security prompt with OK.
On the Edit property page:
Clear Save unresolvable keys.
Select Handle failure to resolve as error.
To close the Property Mapping Rule Conflict Wizard, click OK.
Sample value:
MAINFRAME2
vrtParentDN → vrtEntryParentDN
Create a fixed-value property variable on the One Identity Manager side called vrtParentDN equal to a fixed string with the value $UserLocation$. Map this to vrtEntryParentDN on the ACF2 side.
Sample value:
acf2admingrp=lids,host=mainframe2,o=mycompany,c=com
vrtRDN → vrtEntryRDN
Create a new variable on the One Identity Manager side of type Format Defined Property with the name vrtRDN. Set its value to acf2lid=%CN%. Then map this to vrtEntryRDN on the ACF2 side.
Sample value:
acf2lid=USER1234
userPassword → userPassword
Used to change a user’s ACF2 password. A condition needs to be set on this rule to map the password only when there is a value to be copied.
To add a condition
Create the mapping.
Edit the property mapping rule.
Expand the Condition for execution section at the bottom of the dialog.
Click Add condition and set the following condition (a blank password is indicated by using two apostrophe characters).
Left.UserPassword<>''
DistinguishedName (primary rule) vrtEntryDN
vrtEntryDN is a virtual property, set to the DN of the object in the connector. This forms a unique ID to distinguish individual user objects on the ACF2 system.
To convert this mapping into an object matching rule
Select the property mapping rule in the rule window.
Click 
A message appears.
Click Yes to convert the property mapping rule into an object matching rule and save a copy of the property mapping rule.
Sample value:
acf2lid=USER1234,acf2admingrp=lids,host=mainframe2,o=mycompany,c=com
The following figure shows the user mapping in operation.
© 2025 One Identity LLC. ALL RIGHTS RESERVED. Nutzungsbedingungen Datenschutz Cookie-Einstellungen ändern