Copying an asset or asset account tag to another partition
Tags for assets and asset accounts belong to a partition. Use the 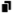 Copy button on the Tags pane on the Asset Management settings page to clone an asset or asset account tag and assign it to a different partition.
Copy button on the Tags pane on the Asset Management settings page to clone an asset or asset account tag and assign it to a different partition.
You cannot modify the partition assignment of an existing tag using the View Details operation. Use this Copy operation to clone the tag and assign it to an additional partition.
To copy an asset or asset account tag to another partition
- Navigate to Asset Management | Tags.
-
Click the 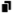 toolbar button. The Copy Tag dialog displays, allowing you to select one or more partitions.
toolbar button. The Copy Tag dialog displays, allowing you to select one or more partitions.
-
Select the check box for the partitions to which the selected tag is to be assigned.
-
Click Select Partition. If a tag with the same name already exits in the selected partition, you will be asked if you want to replace the tag.
Viewing asset and asset account tag assignments
Use the 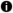 Occurrences button on the Tags pane on the Asset Management page to view a list of all the assets and asset accounts assigned to a tag.
Occurrences button on the Tags pane on the Asset Management page to view a list of all the assets and asset accounts assigned to a tag.
To view asset and asset account tag assignments
- Navigate to Asset Management | Tags.
- Select a tag from the list.
-
Click the 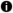 Occurrences toolbar button.
Occurrences toolbar button.
The Occurrences dialog displays, which contains a list of all the assets and accounts assigned to the selected dynamic tag:
- Name: Name of the asset or account.
- Domain Name: Name of the domain.
- Asset: The name of the asset.
- Dynamic: Indicates whether or not the tag is dynamically assigned.
- Type: Whether the occurrence identifies an Asset or Account associated with the named Asset.
- Use the Search box to locate a specific tag or set of tags in this list. Enter the character string to be used to search for a match.
- Click
 to close the dialog and return to the Tags pane.
to close the dialog and return to the Tags pane.
Registered Connectors
The Asset Administrator is responsible for adding and managing registered connectors.
Navigate to:
After joining Safeguard for Privileged Passwords with One Identity Starling (for more information, see Starling), the Registered Connectors pane displays the following.
Table 165: Registered Connectors: Properties
| Display |
This column shows the display name entered for the registered connector. |
|
Platform Name |
This column shows the platform name. |
|
Visible To Partitions |
This column shows the partitions that the connector is visible for. When a connector is visible to all partitions then the column will show All Partitions. |
Use the following toolbar buttons to manage the registered connector settings.
Table 166: Registered Connectors: Toolbar
 Add Add |
Add a registered connector. For more information, see Adding a registered connector. |
 Delete Delete |
Remove the selected registered connector. |
|
 Edit Edit
|
Edit the selected registered connector. |
 Refresh Refresh |
Update the list of registered connectors. |
|
 View View
|
View the valid operations for the registered connector. |
Adding a registered connector
It is the responsibility of the Asset Administrator to configure registered connectors.
To add a registered connector
IMPORTANT: Before adding a registered connector, read the Starling Connect documentation for instructions on configuring the connector within Starling Connect for use with Safeguard for Privileged Passwords. The connectors currently available for use with Safeguard for Privileged Passwords are listed in the Starling Connect documentation.
- Navigate to:
- Click
 Add.
Add.
- These fields display:
- Registered Connectors: Select the connector (already configured in Starling Connect) to register with Safeguard for Privileged Passwords.
- Starling Connector Version: Select the version for the Starling connector.
- Display: Enter a display name for the connector.
- Visible To All Partitions: Select this check box to make the registered connector visible to all partitions.
- Visible To Partitions: Available when Visible To All Partitions is not selected, use this section to define which partitions this registered connector will be visible to:
 (Add): Use this button to add a new partition.
(Add): Use this button to add a new partition.
 (Remove): Use this button to remove a previously selected partition.
(Remove): Use this button to remove a previously selected partition.
-
To add the registered connector, click OK.
The connector will now be registered as a platform and be available as a platform type in the definition of an asset.
IMPORTANT: When using a registered connector with Safeguard for Privileged Passwords, there may be additional considerations involved when configuring certain functionalities. For example, Azure AD uses throttling to limit the number of password changes that can occur within a set period of time. This can mean errors are reported within Safeguard for Privileged Passwords when a large number of accounts associated with a registered Azure AD connector are all scheduled to automatically update their passwords due to their password management settings.
toolbar button. The Copy Tag dialog displays, allowing you to select one or more partitions.

 Occurrences button on the Tags pane on the Asset Management page to view a list of all the assets and asset accounts assigned to a tag.
Occurrences button on the Tags pane on the Asset Management page to view a list of all the assets and asset accounts assigned to a tag.  to close the dialog and return to the Tags pane.
to close the dialog and return to the Tags pane.  web client: Asset Management | Connect and Platforms | Registered Connectors.
web client: Asset Management | Connect and Platforms | Registered Connectors. Add
Add  Delete
Delete  Edit
Edit  Refresh
Refresh  View
View  Add.
Add.
 (Remove): Use this button to remove a previously selected partition.
(Remove): Use this button to remove a previously selected partition.