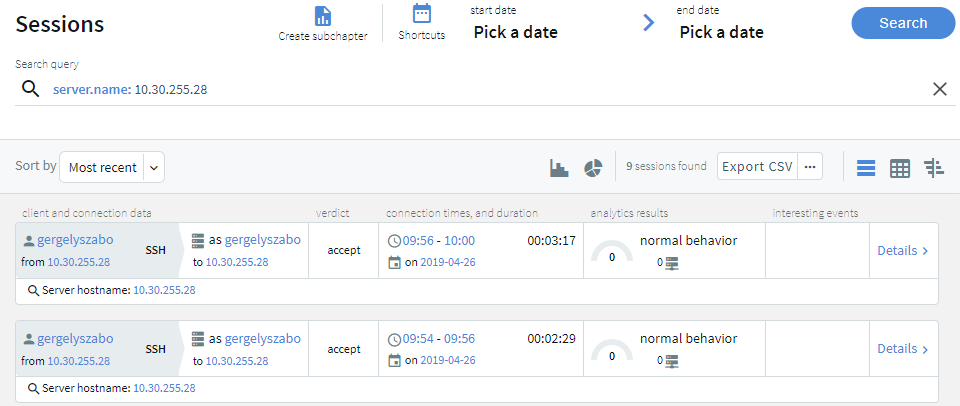
Specify a time range to restrict, or filter your search criteria by setting boundaries on your searches. You can restrict the search to one of the preset time ranges, or use a custom time range for a more specific search.
The following describes how you can use search filters to perform a more specific search.
This section lists the search filters that you can use to perform a more specific search. For information about how to use the search filters listed below, see Using search filters.
The following table provides an explanation to the search filter tables listed in this section.
session
Active
|
Name: |
Active |
|
Search filter: |
active |
|
Type: |
boolean |
|
Displayed: |
True |
The session is still open.
Analytics Interesting events
|
Name: |
Analytics Interesting events |
|
Search filter: |
analytics.interesting_events |
|
Type: |
string |
|
Displayed: |
True |
Collection of interesting command(s) and window title(s) from the session.
Analytics Score
|
Name: |
Analytics Score |
|
Search filter: |
analytics.score.aggregated |
|
Type: |
long |
|
Displayed: |
True |
The risk score that the Analytics Module assigned to the session.Ranges from 0 to 100, 100 is the highest risk score.
Score time
|
Name: |
Score time |
|
Search filter: |
analytics.score.time |
|
Type: |
date |
|
Displayed: |
False |
The scoring time of the given analytics. The different analytics are scored at different times based on the type of the analytics and certain configuration settings.
Command score
|
Name: |
Command score |
|
Search filter: |
analytics.score.details.command.score |
|
Type: |
long |
|
Displayed: |
True |
Score given by the Command algorithm.
FIS score
|
Name: |
FIS score |
|
Search filter: |
analytics.score.details.fis.score |
|
Type: |
long |
|
Displayed: |
True |
Score given by the Frequent Item Set (FIS) algorithm
Host login score
|
Name: |
Host login score |
|
Search filter: |
analytics.score.details.hostlogin.score |
|
Type: |
long |
|
Displayed: |
True |
Score given by the Host login algorithm.
Login time score
|
Name: |
Login time score |
|
Search filter: |
analytics.score.details.logintime.score |
|
Type: |
long |
|
Displayed: |
True |
Score given by the Login time algorithm.
Keystroke score
|
Name: |
Keystroke score |
|
Search filter: |
analytics.score.details.keystroke.score |
|
Type: |
long |
|
Displayed: |
True |
Score given by the Keystroke algorithm.
Windowtitle score
|
Name: |
Windowtitle score |
|
Search filter: |
analytics.score.details.windowtitle.score |
|
Type: |
long |
|
Displayed: |
True |
Score given by the Window title algorithm.
Scripted
|
Name: |
Scripted |
|
Search filter: |
analytics.scripted |
|
Type: |
boolean |
|
Displayed: |
True |
True if the One Identity Safeguard for Privileged Analytics module marked the session as scripted because of non-human activity
Similar Sessions
|
Name: |
Similar Sessions |
|
Search filter: |
analytics.similar_sessions |
|
Type: |
string |
|
Displayed: |
True |
Collection of similar sessions from different sources.
|
Name: |
Analytics tags |
|
Search filter: |
analytics.tags |
|
Type: |
string |
|
Displayed: |
True |
The Analytics tags section in Search > details.
Client IP
|
Name: |
Client IP |
|
Search filter: |
client.ip |
|
Type: |
ip |
|
Displayed: |
True |
The IP address of the client that initiated the session.
Client name
|
Name: |
Client name |
|
Search filter: |
client.name |
|
Type: |
string |
|
Displayed: |
True |
The name of the client that initiated the session.
Client port
|
Name: |
Client port |
|
Search filter: |
client.port |
|
Type: |
port |
|
Displayed: |
True |
The port number of the client that initiated the session.
Creation time
|
Name: |
Creation time |
|
Search filter: |
creation_time |
|
Type: |
date |
|
Displayed: |
True |
The first time the pipeline created the session. It is different from start_time and can be later than start_time.
Duration
|
Name: |
Duration |
|
Search filter: |
duration |
|
Type: |
long |
|
Displayed: |
True |
The length of the session (how long the session lasted).
End time
|
Name: |
End time |
|
Search filter: |
end_time |
|
Type: |
date |
|
Displayed: |
True |
Date when the session was closed.
For ongoing connections, the value is null.
Starting with SPS 5 LTS, the timestamp is in ISO 8601 format, for example, 2018-10-11T09:23:38.000+02:00. In earlier versions, it was in UNIX timestamp format.
Log adapter
|
Name: |
Log adapter |
|
Search filter: |
log.adapter_name |
|
Type: |
string |
|
Displayed: |
True |
The name of the Log Adapter Plugin. This plugin can be uploaded at Basic Settings > Plugins.
Log auth method
|
Name: |
Log auth method |
|
Search filter: |
log.auth_method |
|
Type: |
string |
|
Displayed: |
True |
SSH relayed authentication method. It is configured at SSH Control > Authentication Policies > Relayed authentication methods.
Log syslog time
|
Name: |
Log syslog time |
|
Search filter: |
log.syslog_time |
|
Type: |
date |
|
Displayed: |
True |
Date of the message in the ISO 8601 compatible standard timestamp format.
Node ID
|
Name: |
Node ID |
|
Search filter: |
node_id |
|
Type: |
string |
|
Displayed: |
True |
The node ID of the Safeguard for Privileged Sessions machine
Origin
|
Name: |
Origin |
|
Search filter: |
origin |
|
Type: |
string |
|
Displayed: |
True |
How One Identity Safeguard for Privileged Analytics received this session. Can be One Identity Safeguard for Privileged Sessions for sessions based on an audit trail recorded by One Identity Safeguard for Privileged Sessions, or LOG for sessions built from log data.
Protocol
|
Name: |
Protocol |
|
Search filter: |
protocol |
|
Type: |
enum |
|
Displayed: |
True |
The protocol used in the session: Citrix ICA, HTTP, RDP, SSH, Telnet (including TN3270 and TN5250), or VNC.
Possible values:
-
HTTP: HTTP
-
ICA: ICA
-
RDP: RDP
-
SSH: SSH
-
TELNET: TELNET
-
VNC: VNC
|
Name: |
Additional metadata |
|
Search filter: |
recording.additional_metadata |
|
Type: |
string |
|
Displayed: |
False |
Data about the session recorded by the different plugins of One Identity Safeguard for Privileged Sessions, for example, when using an Authentication and Authorization plugin.
Recording Archive date
|
Name: |
Recording Archive date |
|
Search filter: |
recording.archive.date |
|
Type: |
date |
|
Displayed: |
True |
The date when the connection was archived or cleaned up.
Recording Archive path
|
Name: |
Recording Archive path |
|
Search filter: |
recording.archive.path |
|
Type: |
string |
|
Displayed: |
True |
The path where the audit trail was archived on the remote server.
Recording Archive policy
|
Name: |
Recording Archive policy |
|
Search filter: |
recording.archive.policy |
|
Type: |
string |
|
Displayed: |
True |
The archive policy used to archive the audit trail.
Recording Archive server
|
Name: |
Recording Archive server |
|
Search filter: |
recording.archive.server |
|
Type: |
ip |
|
Displayed: |
True |
The hostname or IP address of the remote server where the audit trail was archived.
Recording Archived
|
Name: |
Recording Archived |
|
Search filter: |
recording.archived |
|
Type: |
boolean |
|
Displayed: |
True |
Shows if the data (metadata, audit trail) about the session was archived to a remote server.
Audit trail path
|
Name: |
Audit trail path |
|
Search filter: |
recording.audit_trail |
|
Type: |
string |
|
Displayed: |
False |
The path to the audit trail file on One Identity Safeguard for Privileged Sessions. If One Identity Safeguard for Privileged Sessions has already archived the audit trail, see the Archive path field instead.
. If the session does not have an audit trail, this element is not used. To download the audit trail, see Replaying audit trails in your browser.
Audit trail download link
|
Name: |
Audit trail download link |
|
Search filter: |
trail_download_link |
|
Type: |
string |
|
Displayed: |
True |
The download link to the audit trail file on One Identity Safeguard for Privileged Sessions.
Recording Authentication method
|
Name: |
Recording Authentication method |
|
Search filter: |
recording.auth_method |
|
Type: |
string |
|
Displayed: |
True |
The authentication method used in the session.
Recording Channel policy
|
Name: |
Recording Channel policy |
|
Search filter: |
recording.channel_policy |
|
Type: |
string |
|
Displayed: |
True |
The Channel policy applied to the session. Channel policy determines the channels permitted in the connection, and if the channel is audited or not. The Channel policy can restrict access based on IP address, user list, user group, or time policy.
You can find the list of channel policies for each protocol at the <Protocol> Control > Channel Policies page.
Commands available
|
Name: |
Commands available |
|
Search filter: |
recording.command_extracted |
|
Type: |
boolean |
|
Displayed: |
True |
True if commands have been extracted from the session. The extracted commands are in the Events field.
Recording Connection policy
|
Name: |
Recording Connection policy |
|
Search filter: |
recording.connection_policy |
|
Type: |
string |
|
Displayed: |
True |
The name of the Connection policy that handled the client's connection request.
This is the name displayed on the <Protocol> Control > Connections page of the SPS web interface, and in the name field of the Connection Policy object. You can find the list of connection policies for each protocol at the <Protocol> Control > Connections page.
Recording Connection policy ID
|
Name: |
Recording Connection policy ID |
|
Search filter: |
recording.connection_policy_id |
|
Type: |
string |
|
Displayed: |
True |
The ID of the Connection policy that handled the client's connection request.
You can find the list of connection policies for each protocol at the <Protocol> Control > Connections page.
Recording Content reference ID
|
Name: |
Recording Content reference ID |
|
Search filter: |
recording.content_reference_id |
|
Type: |
long |
|
Displayed: |
True |
The unique identifier for the session content search.
Recording Indexing status
|
Name: |
Recording Indexing status |
|
Search filter: |
recording.index_status |
|
Type: |
enum |
|
Displayed: |
True |
Shows if the channel has been indexed.
Possible values:
-
CHANNEL_OPEN: Session is active
-
INDEXED: Session indexed
-
INDEXING_FAILED: Session indexing failed
-
INDEXING_IN_PROGRESS: Session indexing in progress
-
INDEXING_NOT_REQUIRED: Session indexing not required
-
NOT_INDEXED: Session is not indexed
-
NO_TRAIL: Auditing not enabled
Has ZAC
|
Name: |
Has ZAC |
|
Search filter: |
recording.has_zac |
|
Type: |
boolean |
|
Displayed: |
False |
Audit Content file is available for the session. This file allows the user to search the content of graphical sessions using the Safeguard Desktop Player.
Recording Network namespace
|
Name: |
Recording Network namespace |
|
Search filter: |
recording.network_id |
|
Type: |
string |
|
Displayed: |
True |
The ID of the Linux network namespace where the session originated from.
Server local IP address
|
Name: |
Server local IP address |
|
Search filter: |
recording.server_local.ip |
|
Type: |
ip |
|
Displayed: |
True |
The IP address of One Identity Safeguard for Privileged Sessions used in the server-side connection.
Server local name
|
Name: |
Server local name |
|
Search filter: |
recording.server_local.name |
|
Type: |
text |
|
Displayed: |
True |
The hostname of One Identity Safeguard for Privileged Sessions used in the server-side connection. If the hostname is not available, this field contains the IP address of One Identity Safeguard for Privileged Sessions.
Recording Server local port
|
Name: |
Recording Server local port |
|
Search filter: |
recording.server_local.port |
|
Type: |
port |
|
Displayed: |
True |
The port number of One Identity Safeguard for Privileged Sessions used in the server-side connection.
Recording Session ID
|
Name: |
Recording Session ID |
|
Search filter: |
recording.session_id |
|
Type: |
string |
|
Displayed: |
True |
A globally unique string that identifies the session. Log messages related to the session contain this ID.
Target IP address
|
Name: |
Target IP address |
|
Search filter: |
recording.target.ip |
|
Type: |
ip |
|
Displayed: |
True |
The client originally tried to access this IP address. This can differ from the destination address, for example, when One Identity Safeguard for Privileged Sessions is configured to redirect the connection. The address that the client actually connected to is in the Server address field.
Target name
|
Name: |
Target name |
|
Search filter: |
recording.target.name |
|
Type: |
text |
|
Displayed: |
True |
The client originally tried to access this host. This can differ from the destination address, for example, when One Identity Safeguard for Privileged Sessions is configured to redirect the connection. The address that the client actually connected to is in the Server address field. If the hostname is not available, this field contains the IP address of the host.
Recording Target port
|
Name: |
Recording Target port |
|
Search filter: |
recording.target.port |
|
Type: |
port |
|
Displayed: |
True |
The client originally tried to access this port. This can differ from the port of the destination server, for example, when One Identity Safeguard for Privileged Sessions is configured to redirect the connection. The port that the client actually connected to is in the Server port field.
Recording Verdict
|
Name: |
Recording Verdict |
|
Search filter: |
recording.verdict |
|
Type: |
enum |
|
Displayed: |
True |
Indicates what One Identity Safeguard for Privileged Sessions decided about the session.
Possible values:
-
ACCEPT: Accepted
-
ACCEPT_TERMINATED: Terminated by a content policy
-
AUTH_FAIL: Authentication failed
-
DENY: Connection rejected
-
FAIL: Connection timed out on the server
-
GW_AUTH_FAIL: Gateway authentication failed
-
KEY_ERROR: Hostkey mismatch
-
USER_MAPPING_FAIL: Usermapping failed
|
Name: |
Recording Window titles available |
|
Search filter: |
recording.window_title_extracted |
|
Type: |
boolean |
|
Displayed: |
True |
True if window titles have been extracted from the session. The extracted window titles are in the Window title field.
Server IP
|
Name: |
Server IP |
|
Search filter: |
server.ip |
|
Type: |
ip |
|
Displayed: |
True |
The IP address of the server that One Identity Safeguard for Privileged Sessions connected to. This address was the remote end of the server-side connection.
Server ID
|
Name: |
Server ID |
|
Search filter: |
server.id |
|
Type: |
string |
|
Displayed: |
True |
The id of the server that One Identity Safeguard for Privileged Sessions connected to.
Server hostname
|
Name: |
Server hostname |
|
Search filter: |
server.name |
|
Type: |
string |
|
Displayed: |
True |
The hostname of the server that One Identity Safeguard for Privileged Sessions connected to.
Server port
|
Name: |
Server port |
|
Search filter: |
server.port |
|
Type: |
port |
|
Displayed: |
True |
The port number of the server that One Identity Safeguard for Privileged Sessions connected to.
Start time
|
Name: |
Start time |
|
Search filter: |
start_time |
|
Type: |
date |
|
Displayed: |
True |
Date when the session was started.
Starting with SPS 5 LTS, the timestamp is in ISO 8601 format, for example, 2018-10-11T09:23:38.000+02:00. In earlier versions, it was in UNIX timestamp format.
Gateway username
|
Name: |
Gateway username |
|
Search filter: |
user.gateway_username |
|
Type: |
string |
|
Displayed: |
True |
The username used to authenticate on the One Identity Safeguard for Privileged Sessions gateway (that is, in the client-side connection). Sometimes it is also called client-side username.
Gateway username domain
|
Name: |
Gateway username domain |
|
Search filter: |
user.gateway_username_domain |
|
Type: |
string |
|
Displayed: |
True |
The domain of the username used to authenticate on the One Identity Safeguard for Privileged Sessions gateway (that is, in the client-side connection).
User ID
|
Name: |
User ID |
|
Search filter: |
user.id |
|
Type: |
string |
|
Displayed: |
True |
The ID of the user.
Username
|
Name: |
Username |
|
Search filter: |
user.name |
|
Type: |
string |
|
Displayed: |
True |
This field contains the username which was used by the user to authenticate to the remote server. Its value is the same as the gateway username when it is available. Otherwise, it will be filled with the server username.
Name domain
|
Name: |
Name domain |
|
Search filter: |
user.name_domain |
|
Type: |
string |
|
Displayed: |
True |
This field contains the domain of the username which was used by the user to authenticate to the remote server. Its value is the same as the gateway domain when it is available. Otherwise, it will be filled with the server domain.
Server username
|
Name: |
Server username |
|
Search filter: |
user.server_username |
|
Type: |
string |
|
Displayed: |
True |
The username used to log in to the remote server. This username can differ from the client-side username if usermapping is used in the connection.
Server username domain
|
Name: |
Server username domain |
|
Search filter: |
user.server_username_domain |
|
Type: |
string |
|
Displayed: |
True |
The domain of the username used to log in to the remote server.
Verdict
|
Name: |
Verdict |
|
Search filter: |
verdict |
|
Type: |
enum |
|
Displayed: |
True |
Indicates what One Identity Safeguard for Privileged Sessions decided about the session. A session verdict that originates from log events or other external events.
Possible values:
-
ACCEPT: Accepted
-
AUTH_FAIL: Authentication failed
-
DENY: Connection rejected
-
FAIL: Connection timed out on the server
-
PENDING: Connection is pending
-
TERMINATED: Connection terminated
Channel is active
|
Name: |
Channel is active |
|
Search filter: |
channel.active |
|
Type: |
boolean |
|
Displayed: |
False |
True if the session has not ended yet.
Application
|
Name: |
Application |
|
Search filter: |
channel.application |
|
Type: |
string |
|
Displayed: |
False |
The name of the application accessed in a seamless Citrix ICA connection.
Audit stream ID
|
Name: |
Audit stream ID |
|
Search filter: |
channel.audit_stream_id |
|
Type: |
string |
|
Displayed: |
False |
The identifier of the channel's audit stream. If the session does not have an audit trail, this element is not used.
Channel ID
|
Name: |
Channel ID |
|
Search filter: |
channel.channel_id |
|
Type: |
long |
|
Displayed: |
False |
The unique ID of the channel.
Client X.509 Subject
|
Name: |
Client X.509 Subject |
|
Search filter: |
channel.client_x509_subject |
|
Type: |
string |
|
Displayed: |
False |
The client's certificate in TELNET or VNC sessions. Available only if the 'Client-side transport security settings > Peer certificate validation' option is enabled in One Identity Safeguard for Privileged Sessions.
Executed commands
|
Name: |
Executed commands |
|
Search filter: |
channel.command |
|
Type: |
string |
|
Displayed: |
False |
Lists the commands executed in an SSH session.
Port-forward target IP
|
Name: |
Port-forward target IP |
|
Search filter: |
channel.connected.ip |
|
Type: |
ip |
|
Displayed: |
False |
The traffic was forwarded to this IP address in Remote Forward and Local Forward channels.
Port-forward target name
|
Name: |
Port-forward target name |
|
Search filter: |
channel.connected.name |
|
Type: |
text |
|
Displayed: |
False |
The traffic was forwarded to this host in Remote Forward and Local Forward channels. If the hostname is not available, this field contains the IP address of the host
Port-forward target port
|
Name: |
Port-forward target port |
|
Search filter: |
channel.connected.port |
|
Type: |
port |
|
Displayed: |
False |
The traffic was forwarded to this port in Remote Forward and Local Forward channels.
Device name
|
Name: |
Device name |
|
Search filter: |
channel.device_name |
|
Type: |
string |
|
Displayed: |
False |
The name or ID of the shared device (redirect) used in the RDP connection.
Channel duration
|
Name: |
Channel duration |
|
Search filter: |
channel.duration |
|
Type: |
long |
|
Displayed: |
False |
The length of the channel (how long the channel lasted).
Dynamic channel
|
Name: |
Dynamic channel |
|
Search filter: |
channel.dynamic_channel |
|
Type: |
string |
|
Displayed: |
False |
The name or ID of the dynamic channel opened in the RDP session.
Used with the dynamic virtual RDP channel type.
Channel end time
|
Name: |
Channel end time |
|
Search filter: |
channel.end_time |
|
Type: |
date |
|
Displayed: |
False |
Date when the channel was closed.
Environment
|
Name: |
Environment |
|
Search filter: |
channel.environment |
|
Type: |
string |
|
Displayed: |
False |
Date when the channel was closed.
Four-eyes authorizer
|
Name: |
Four-eyes authorizer |
|
Search filter: |
channel.four_eyes_authorizer |
|
Type: |
string |
|
Displayed: |
False |
The username of the user who authorized the session. Available only if four-eyes authorization is required for the channel.
Four-eyes description
|
Name: |
Four-eyes description |
|
Search filter: |
channel.four_eyes_description |
|
Type: |
string |
|
Displayed: |
False |
The description submitted by the authorizer of the session.
Channel originator IP address
|
Name: |
Channel originator IP address |
|
Search filter: |
channel.originator.ip |
|
Type: |
ip |
|
Displayed: |
False |
The IP address of the host initiating the channel in Remote Forward and Local Forward channels. Note that this host is not necessarily the client or the server of the SSH connection.
Channel originator name
|
Name: |
Channel originator name |
|
Search filter: |
channel.originator.name |
|
Type: |
text |
|
Displayed: |
False |
The hostname of the host initiating the channel in Remote Forward and Local Forward channels. Note that this host is not necessarily the client or the server of the SSH connection. If the hostname is not available, this field contains the IP address of the host.
Originator port
|
Name: |
Originator port |
|
Search filter: |
channel.originator.port |
|
Type: |
port |
|
Displayed: |
False |
The number of the forwarded port in Remote Forward and Local Forward SSH channels.
Rule number
|
Name: |
Rule number |
|
Search filter: |
channel.rule_num |
|
Type: |
string |
|
Displayed: |
False |
The number of the line in the Channel policy applied to the channel.
SCP path
|
Name: |
SCP path |
|
Search filter: |
channel.scp_path |
|
Type: |
string |
|
Displayed: |
False |
Name and path of the file copied via SCP. Available only for SCP sessions (Session exec SCP SSH channels) if the Log file transfers to database option isenabled in the Channel Policy of the connection.
Channel start time
|
Name: |
Channel start time |
|
Search filter: |
channel.start_time |
|
Type: |
date |
|
Displayed: |
False |
Date when the channel was started.
Subsystem name
|
Name: |
Subsystem name |
|
Search filter: |
channel.subsystem_name |
|
Type: |
string |
|
Displayed: |
False |
Name of the SSH subsystem used in the channel.
Channel type
|
Name: |
Channel type |
|
Search filter: |
channel.type |
|
Type: |
enum |
|
Displayed: |
False |
Type of the channel.
Possible values:
-
#drawing: Drawing
-
CTXCAM: Audio
-
CTXCDM: Drive
-
CTXCLIP: Clipboard
-
CTXCOM1: Printer (COM1)
-
CTXCOM2: Printer (COM2)
-
CTXCPM: Printer Spooler
-
CTXFLSH: HDX Mediastream
-
CTXLPT1: Printer (LPT1)
-
CTXLPT2: Printer (LPT2)
-
CTXSCRD: Smartcard
-
CTXTW: Drawing (Thinwire)
-
CTXTWI: Seamless
-
CTXUSB: USB
-
SPDBRS: Speedbrowse
-
auth-agent: Agent
-
cliprdr: Clipboard
-
custom: Custom
-
direct-tcpip: Local forward
-
drawing: Drawing
-
drdynvc: Dynamic virtual channel
-
forwarded-tcpip: Remote forward
-
http: HTTP
-
rdpdr: Redirects
-
rdpdr-disk: Disk redirect
-
rdpdr-parallel: Parallel redirect
-
rdpdr-printer: Printer redirect
-
rdpdr-scard: SCard redirect
-
rdpdr-serial: Serial redirect
-
rdpsnd: Sound
-
seamrdp: Seamless
-
session-exec: Session exec
-
session-exec-scp: Session exec SCP
-
session-shell: Session shell
-
session-subsystem: Session subsystem
-
session-subsystem-sftp: Session SFTP
-
telnet: Telnet
-
vnc: VNC
-
x11: X11 forward
Channel verdict
|
Name: |
Channel verdict |
|
Search filter: |
channel.verdict |
|
Type: |
enum |
|
Displayed: |
False |
Indicates what One Identity Safeguard for Privileged Sessions decided about the channel.
Possible values:
-
ACCEPT: Accepted
-
DENY: Denied
-
FOUR_EYES_DEFERRED: Waiting for remote username
-
FOUR_EYES_ERROR: Internal error during four-eyes authorization
-
FOUR_EYES_REJECT: Four-eyes authorization rejected
-
FOUR_EYES_TIMEOUT: Four-eyes authorization timed out
Event Action
|
Name: |
Event Action |
|
Search filter: |
event.action |
|
Type: |
string |
|
Displayed: |
False |
The command line without prompt in commands
Channel ID
|
Name: |
Channel ID |
|
Search filter: |
event.channel_id |
|
Type: |
string |
|
Displayed: |
False |
The id of the channel the event belongs to.
Event content
|
Name: |
Event content |
|
Search filter: |
event.content |
|
Type: |
string |
|
Displayed: |
False |
The command executed, or the window title detected in the channel (for example, ls, exit, or Firefox).
Protocol details
|
Name: |
Protocol details |
|
Search filter: |
event.details |
|
Type: |
string |
|
Displayed: |
False |
The details of the protocol used for the operation.
Operation
|
Name: |
Operation |
|
Search filter: |
event.operation |
|
Type: |
string |
|
Displayed: |
False |
The type of the operation that occurred, for example, Create file (in the case of FTP) or GET (in the case of HTTP).
Path
|
Name: |
Path |
|
Search filter: |
event.path |
|
Type: |
string |
|
Displayed: |
False |
The path (if any) used by the operation that occurred.
Event ID
|
Name: |
Event ID |
|
Search filter: |
event.record_id |
|
Type: |
long |
|
Displayed: |
False |
The identifier of the event within the audit trail (.zat file).
Response code
|
Name: |
Response code |
|
Search filter: |
event.response_code |
|
Type: |
long |
|
Displayed: |
False |
The status code of the protocol response (if any) returned.
Event date
|
Name: |
Event date |
|
Search filter: |
event.time |
|
Type: |
date |
|
Displayed: |
False |
The date when the event happened.
Event type
|
Name: |
Event type |
|
Search filter: |
event.type |
|
Type: |
string |
|
Displayed: |
False |
The type of the event, for example, command, screen_content, window_title.
Alert type
|
Name: |
Alert type |
|
Search filter: |
alert.alert_type |
|
Type: |
enum |
|
Displayed: |
False |
The type of the alert.
Possible values:
-
adp.event.command: A command entered in SSH or Telnet.
-
adp.event.screen.content: Alert triggered by the screen content.
-
adp.event.screen.creditcard: Credit card numbers detected. Displayed only as an alert, not visible in the events.
-
adp.event.screen.windowtitle: The title of the window in graphic protocols.
Channel ID
|
Name: |
Channel ID |
|
Search filter: |
alert.channel_id |
|
Type: |
string |
|
Displayed: |
False |
The id of the channel the alert belongs to.
Matched regexp on action
|
Name: |
Matched regexp on action |
|
Search filter: |
alert.matched_action |
|
Type: |
string |
|
Displayed: |
False |
The regular expression that matched the command line without prompt
Matched content
|
Name: |
Matched content |
|
Search filter: |
alert.matched_content |
|
Type: |
string |
|
Displayed: |
False |
The content the alert matched.
Matched regexp
|
Name: |
Matched regexp |
|
Search filter: |
alert.matched_regexp |
|
Type: |
string |
|
Displayed: |
False |
The regular expression that matched the content.
Alert ID
|
Name: |
Alert ID |
|
Search filter: |
alert.record_id |
|
Type: |
long |
|
Displayed: |
False |
The identifier of the alert within the audit trail (.zat file).
Rule name
|
Name: |
Rule name |
|
Search filter: |
alert.rule_name |
|
Type: |
string |
|
Displayed: |
False |
The name of the content policy rule.
Alert time
|
Name: |
Alert time |
|
Search filter: |
alert.time |
|
Type: |
date |
|
Displayed: |
False |
The timestamp of the alert.
From API
|
Name: |
From API |
|
Search filter: |
trail_download.from_api |
|
Type: |
boolean |
|
Displayed: |
False |
The audit trail downloaded via API or not.
Trail download ID
|
Name: |
Trail download ID |
|
Search filter: |
trail_download.id |
|
Type: |
string |
|
Displayed: |
False |
The ID of an audit trail download event.
Download ip
|
Name: |
Download ip |
|
Search filter: |
trail_download.ip_address |
|
Type: |
ip |
|
Displayed: |
False |
The ip address from where the download is requested.
Download time
|
Name: |
Download time |
|
Search filter: |
trail_download.time |
|
Type: |
date |
|
Displayed: |
False |
The exact time when the user downloaded the audit trail file.
Downloader username
|
Name: |
Downloader username |
|
Search filter: |
trail_download.username |
|
Type: |
string |
|
Displayed: |
False |
The name of user who downloaded the audit trail of the session.
Commands indexed
|
Name: |
Commands indexed |
|
Search filter: |
indexer_info.config.command.enabled |
|
Type: |
boolean |
|
Displayed: |
False |
True if commands were extracted while indexing the session.
Keyboard buffering interval
|
Name: |
Keyboard buffering interval |
|
Search filter: |
indexer_info.config.keyboard.buffer_interval |
|
Type: |
double |
|
Displayed: |
False |
The buffering interval in milliseconds used when extracting keyboard events while indexing the session.
Keyboard extracted
|
Name: |
Keyboard extracted |
|
Search filter: |
indexer_info.config.keyboard.enabled |
|
Type: |
boolean |
|
Displayed: |
False |
True if keyboard events were extracted while indexing the session.
Mouse buffering interval
|
Name: |
Mouse buffering interval |
|
Search filter: |
indexer_info.config.mouse.buffer_interval |
|
Type: |
double |
|
Displayed: |
False |
The buffering interval in milliseconds used when extracting mouse events while indexing the session.
Mouse extracted
|
Name: |
Mouse extracted |
|
Search filter: |
indexer_info.config.mouse.enabled |
|
Type: |
boolean |
|
Displayed: |
False |
True if mouse events were extracted while indexing the session.
Near real-time indexing
|
Name: |
Near real-time indexing |
|
Search filter: |
indexer_info.config.near_realtime |
|
Type: |
boolean |
|
Displayed: |
False |
True if indexing this session was done near real-time (when the session was still active).
OCR languages
|
Name: |
OCR languages |
|
Search filter: |
indexer_info.config.ocr_languages |
|
Type: |
string |
|
Displayed: |
False |
The language configuration for optical character recognition used when indexing the session.
Screen content indexed
|
Name: |
Screen content indexed |
|
Search filter: |
indexer_info.config.screen.enabled |
|
Type: |
boolean |
|
Displayed: |
False |
True if screen content was extracted while indexing the session.
OCR tradeoff
|
Name: |
OCR tradeoff |
|
Search filter: |
indexer_info.config.screen.omnipage_trade_off |
|
Type: |
string |
|
Displayed: |
False |
The tradeoff used for optical character recognition when extracting screen content while indexing the session.
Titles indexed
|
Name: |
Titles indexed |
|
Search filter: |
indexer_info.config.title.enabled |
|
Type: |
boolean |
|
Displayed: |
False |
True if window titles were extracted while indexing the session.
Indexing error
|
Name: |
Indexing error |
|
Search filter: |
indexer_info.error.message |
|
Type: |
string |
|
Displayed: |
False |
The reason why indexing failed
Indexing cpu time
|
Name: |
Indexing cpu time |
|
Search filter: |
indexer_info.statistics.cpu_time |
|
Type: |
long |
|
Displayed: |
False |
The CPU time that indexing this session took in milliseconds.
Indexing duration
|
Name: |
Indexing duration |
|
Search filter: |
indexer_info.statistics.duration |
|
Type: |
long |
|
Displayed: |
False |
The duration of time that indexing this session took in milliseconds.
Indexing start time
|
Name: |
Indexing start time |
|
Search filter: |
indexer_info.statistics.start_time |
|
Type: |
date |
|
Displayed: |
False |
The time and date when indexing this session started.
Indexing status
|
Name: |
Indexing status |
|
Search filter: |
indexer_info.status |
|
Type: |
string |
|
Displayed: |
False |
Shows if the channel has been indexed successfully or not.
Indexer ADP version
|
Name: |
Indexer ADP version |
|
Search filter: |
indexer_info.version.adp |
|
Type: |
string |
|
Displayed: |
False |
The version of the audit data processor used for indexing the session
Indexer version
|
Name: |
Indexer version |
|
Search filter: |
indexer_info.version.worker |
|
Type: |
string |
|
Displayed: |
False |
The version of the indexer worker used for indexing the session
ZAC created
|
Name: |
ZAC created |
|
Search filter: |
indexer_info.config.zac.enabled |
|
Type: |
boolean |
|
Displayed: |
False |
True if an Audit Content file was created while indexing the session.
Screen content
|
Name: |
Screen content |
|
Search filter: |
screen.content |
|
Type: |
string |
|
Displayed: |
False |
Text that appeared on the screen in the session.
Channel id in trail
|
Name: |
Channel id in trail |
|
Search filter: |
screen.channel_id_in_trail |
|
Type: |
long |
|
Displayed: |
False |
The ID of the channel where this content appeared. To check the channel ID (channel_id), select a session and click details. Navigate to details > Channels and click the channel type.
Screen content creation time
|
Name: |
Screen content creation time |
|
Search filter: |
screen.time |
|
Type: |
screen |
|
Displayed: |
False |
The creation time of the indexed screen content.
Screen content ID
|
Name: |
Screen content ID |
|
Search filter: |
screen.id |
|
Type: |
string |
|
Displayed: |
False |
The ID of a screen content event.
The following sections provide examples for different search queries.
For details on how to use more complex keyphrases that are not covered in this guide, see the Apache Lucene documentation.
By default, One Identity Safeguard for Privileged Sessions (SPS) searches for keywords as whole words and returns only exact matches. Note that if your search keywords include special characters, you must escape them with a backslash (\) character. For details on special characters, see Searching for special characters. The following characters are special characters: + - & | ! ( ) { } [ ] ^ " ~ * ? : \ /
You can also combine these search filters with other expressions and wildcards, for example, title:properties AND gateway.
By default, every keyword or phrase of a search expression is treated as equal. Use the caret ^ symbol to make a keyword or expression more important than the others.



 icon.
icon.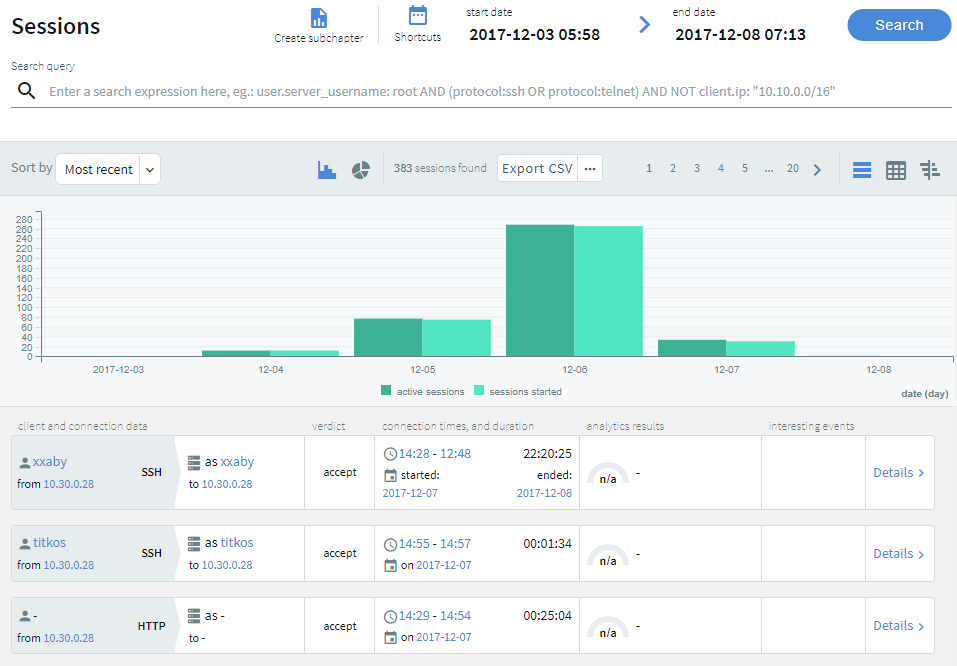
 . To disable the started sessions and view only the active sessions in the timeline, click
. To disable the started sessions and view only the active sessions in the timeline, click  .
.