Password Manager in Perimeter Network
Password Manager in a perimeter network
When deploying Password Manager in a perimeter network (also known as a DMZ), it is recommended to install the Password Manager Service and the sites in a corporate network at first (that is,use the Full installation option in the Password Manager setup), and then install only the Self-Service and Helpdesk sites in the perimeter network.
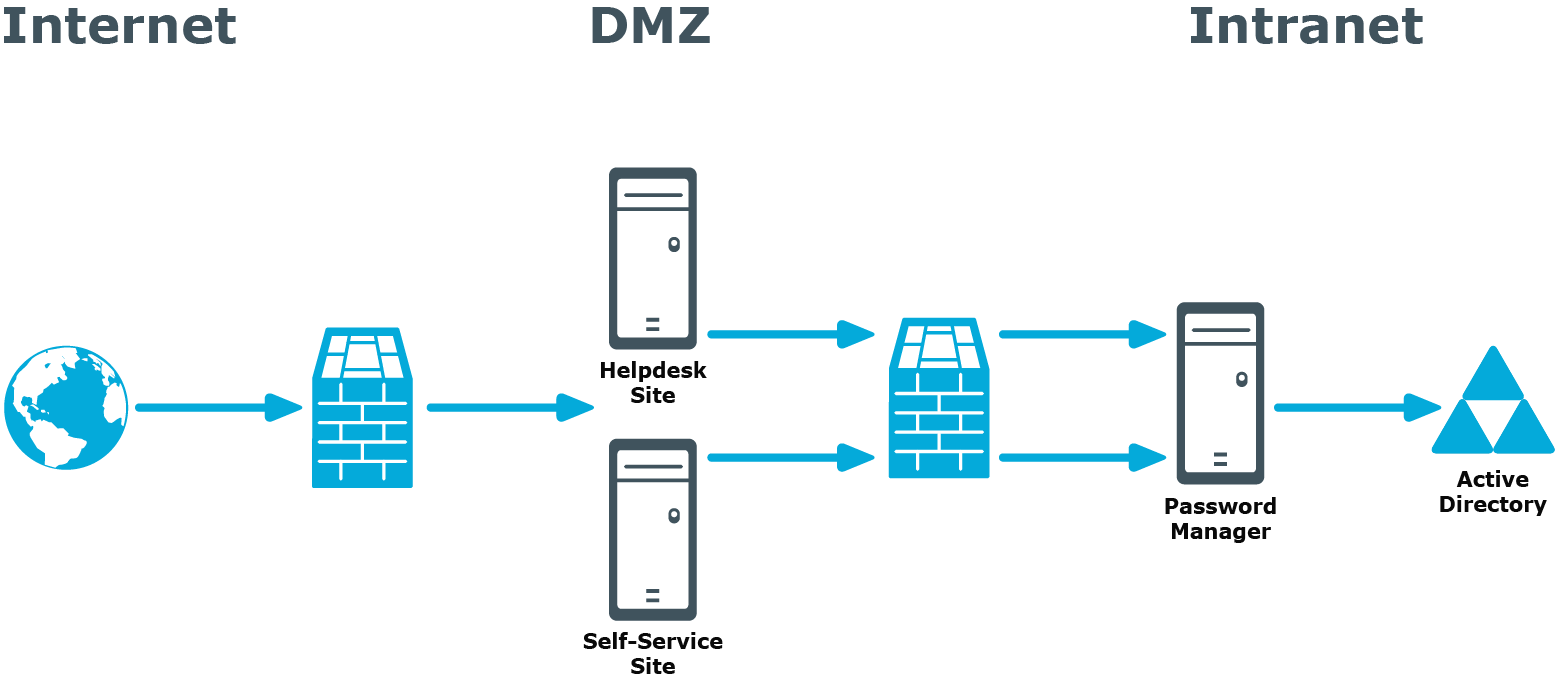
When you use this installation scenario, only one port should be open in the firewall between the corporate network and the perimeter network (by default, port number 8081 is used).
For more information on installing the Self-Service and Helpdesk site separately from the Password Manager Service, see Installing Legacy Self-Service, Password Manager Self-Service, and Helpdesk Sites on a Standalone Server.
Installing Password Manager in Perimeter Network with Read-Only Domain Controllers
Installing Password Manager in Perimeter Network
with Read-Only Domain Controllers
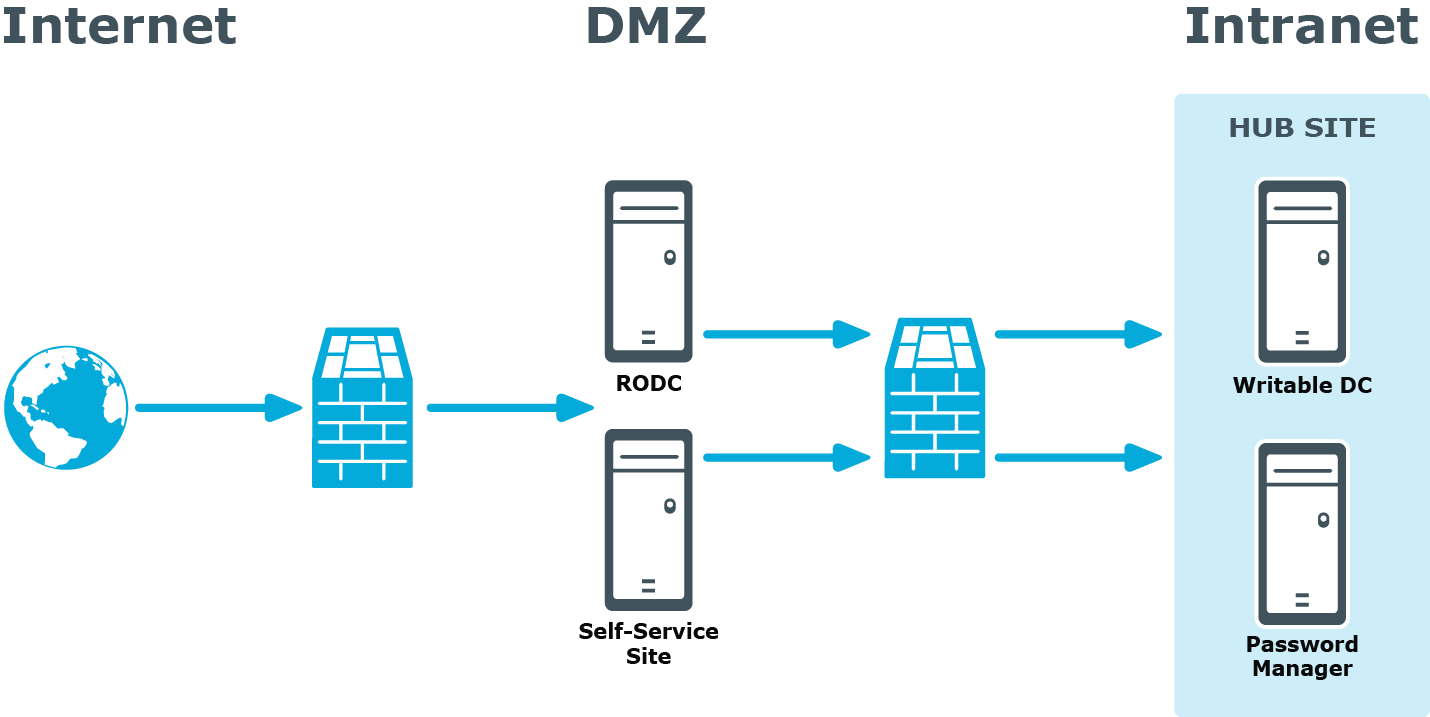
If your network topology includes a perimeter network (DMZ) that contains only read-only domain controllers (RODCs), you should consider the following when installing Password Manager in this environment.
Because password changes may not get immediately replicated to RODCs, users may experience downtime when authenticating using an RODC if their passwords were changed or reset on a DC in another Active Directory site.
To mitigate this issue, it is recommended to do either of the following when installing Password Manager in the perimeter network:
- Install Password Manager Service in a dedicated RODC replication hub site (as shown below), if this hub site exists in your environment.
- If Password Manager Service cannot be installed in the dedicated RODC replication hub site, do either of the following:
- For your Management Policy, specify the appropriate writable DC from the hub site in the advanced settings of the domain connection. For more information, see Specifying advanced settings for domain connection.
- For your Management Policy, specify the hub site in the list of Active Directory sites to which replication changes will be forced. For more information, see Specifying advanced settings for domain connection.
- Enable change notification on the site link between the dedicated RODC replication hub site (or the site in which an RODC is installed) and the site in which Password Manager Service is installed.
Installing Password Manager in Perimeter Network with Reverse Proxy
Installing Password Manager in Perimeter Network
with Reverse Proxy
A reverse proxy is a proxy server that is typically deployed in a perimeter network to enhance security of the corporate network. By providing a single point of access to the servers installed in the intranet, the reverse proxy server protects the intranet from an external attack.
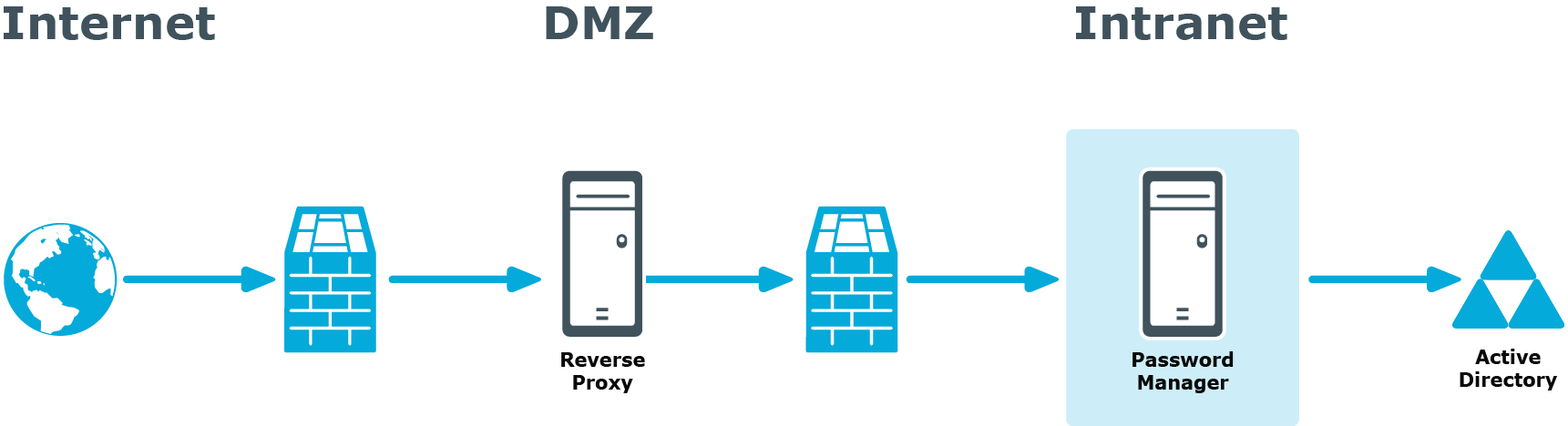
If you have the reverse proxy deployed in the perimeter network in your environment, it is recommended to install the Password Manager Service and the Self-Service and Helpdesk sites in the intranet and configure the reverse proxy to redirect requests from external users to the correct intranet URLs of the Password Manager sites.
Installing Password Manager in Perimeter Networ kwithout AD DS
Installing Password Manager in Perimeter Network
without AD DS
If Active Directory Domain Services (AD DS) is not deployed in a perimeter network in your environment, you may still install Password Manager in this perimeter network.
When AD DS is not deployed in the perimeter network, servers are placed in a workgroup. Password Manager allows installing the Self-Service and Helpdesk sites on servers that are not placed in any domain.



