Privileged Access Suite for Unix
Unix security simplified
Privileged Access Suite for Unix solves the intrinsic security and administration issues of Unix-based systems (including Linux and macOS) while making satisfying compliance requirements easier. It unifies and consolidates identities, assigns individual accountability, and enables centralized reporting for user and administrator access to Unix. The Privileged Access Suite for Unix combines an Active Directory bridge and root delegation solutions under a unified console that grants organizations centralized visibility and streamlined administration of identities and access rights across their entire Unix environment.
Active Directory bridge
Achieve unified access control, authentication, authorization, and identity administration for Unix, Linux, and macOS systems by extending them into Active Directory (AD) and taking advantage of AD’s inherent benefits. Patented technology allows non-Windows resources to become part of the AD trusted realm, and extends AD’s security, compliance, and Kerberos-based authentication capabilities to Unix, Linux, and macOS. See www.oneidentity.com/products/safeguard-authentication-services/ for more information about the Active Directory Bridge product.
Root delegation
The Privileged Access Suite for Unix offers two different approaches to delegating the Unix root account. The suite either enhances or replaces sudo, depending on your needs.
-
By choosing to enhance sudo, you will keep everything you know and love about sudo while enhancing it with features like a central sudo policy server, centralized keystroke logs, a sudo event log, and compliance reports for who can do what with sudo.
See www.oneidentity.com/products/privilege-manager-for-sudo/ for more information about enhancing sudo.
-
By choosing to replace sudo, you will still be able to delegate the Unix root privilege based on centralized policy reporting on access rights, but with a more granular permission and the ability to log keystrokes on all activities from the time a user logs in, not just the commands that are prefixed with "sudo." In addition, this option implements several additional security features like restricted shells, remote host command execution, and hardened binaries that remove the ability to escape out of commands and gain undetected elevated access.
See www.oneidentity.com/products/privilege-manager-for-unix/ for more information about replacing sudo.
Privileged Access Suite for Unix offers two editions: Standard edition and Advanced edition. Both editions include the Safeguard Authentication Services patented technology that allows organizations to extend the security and compliance of Active Directory to Unix, Linux, and macOS platforms and enterprise applications. In addition:
- The Standard edition licenses you for Safeguard for Sudo.
- The Advanced edition licenses you for Privilege Manager for Unix.
The Defender Integration Guide is intended for Windows and non-Windows system administrators, network administrators, consultants, analysts, and any other IT professionals who will be integrating Defender with Safeguard Authentication Services for token-based two factor authentication. This guide walks you through the process of installing and configuring the necessary Defender access policies and Group Policy settings.
Note: The term "Unix" is used informally throughout the Safeguard Authentication Services documentation to denote any operating system that closely resembles the trademarked system, UNIX.
Defender enhances security by enabling two-factor authentication to network, Web, and applications-based resources. One Identity designed Defender to base all administration and identity management on an organization's existing investment in Active Directory and eliminates the costs and time involved in setting up and maintaining proprietary databases.
One Identity supports Defender integration on all platforms that support Safeguard Authentication Services, except macOS and AIX 5.2 or earlier.
Note: On AIX 5.3 and later you must use PAM authentication.
In addition, Defender works with any OATH-compliant hardware token enabling organizations to select the most appropriate token for their users. By leveraging an organization's existing investment in Active Directory and supporting multiple token vendors, Defender enables organizations to increase security and achieve and sustain compliance in a cost-effective manner.
Defender provides strong authentication capabilities.
Why is strong authentication an important part of an Active Directory bridge solution?
When Safeguard Authentication Services integrates Unix with Active Directory, it provides centralized access control and password policy enforcement. However, there are situations where security policies dictate a stronger level of authentication. Safeguard Authentication Services addresses this need with optional strong authentication capabilities. Customers now can use the same solution for integrated Active Directory authentication and strong authentication. Organizations that have tight security requirements will no longer be forced to purchase and implement a third-party solution.
How is strong authentication used with an Active Directory bridge solution?
An organization may have many Unix systems deployed in a traditional, highly secure perimeter network environment. As they are integrated with Active Directory, they will require an Active Directory credential to authenticate. Now, an additional layer of authentication can be added for administrators accessing these systems, using either a hardware or software token.
If an organization has integrated hundreds or thousands of Unix systems with Active Directory, a system administrator can now use the same Active Directory credential to access all of them. An additional level of security can be easily added by requiring the system administrator to use one-time password (OTP) in additional to the Active Directory credential.
How do Safeguard Authentication Services’ strong authentication capabilities compare to other Active Directory bridge solutions?
Strong authentication combined with an Active Directory bridge is a unique and critical differentiator for One Identity. No other Active Directory bridge vendor offers strong authentication as an integrated part of its solution, and no strong authentication vendor offers Unix coverage and Active Directory integration.
Is there an additional charge for strong authentication with Safeguard Authentication Services 4.x?
There is no additional cost for strong authentication with Safeguard Authentication Services 4.x; it is a new feature available to new and upgrading customers.
Safeguard Authentication Services provides strong authentication for up to 25 users at no additional cost through included licenses and tokens for Safeguard Authentication Services Defender. These licenses will cover and secure 25 of an organization‘s Unix system administrators. Strong authentication support for additional end-users is available at an additional per-user cost.
How does strong authentication with Safeguard Authentication Services 4.x work?
Safeguard Authentication Services:
- Includes strong authentication modules and native packages for all supported platforms (100+).
- Remotely deploys and installs the strong authentication module.
- Provides hardware and software tokens for one-time passwords.
- Enables policy-based configuration of strong authentication through Active Directory Group Policy.
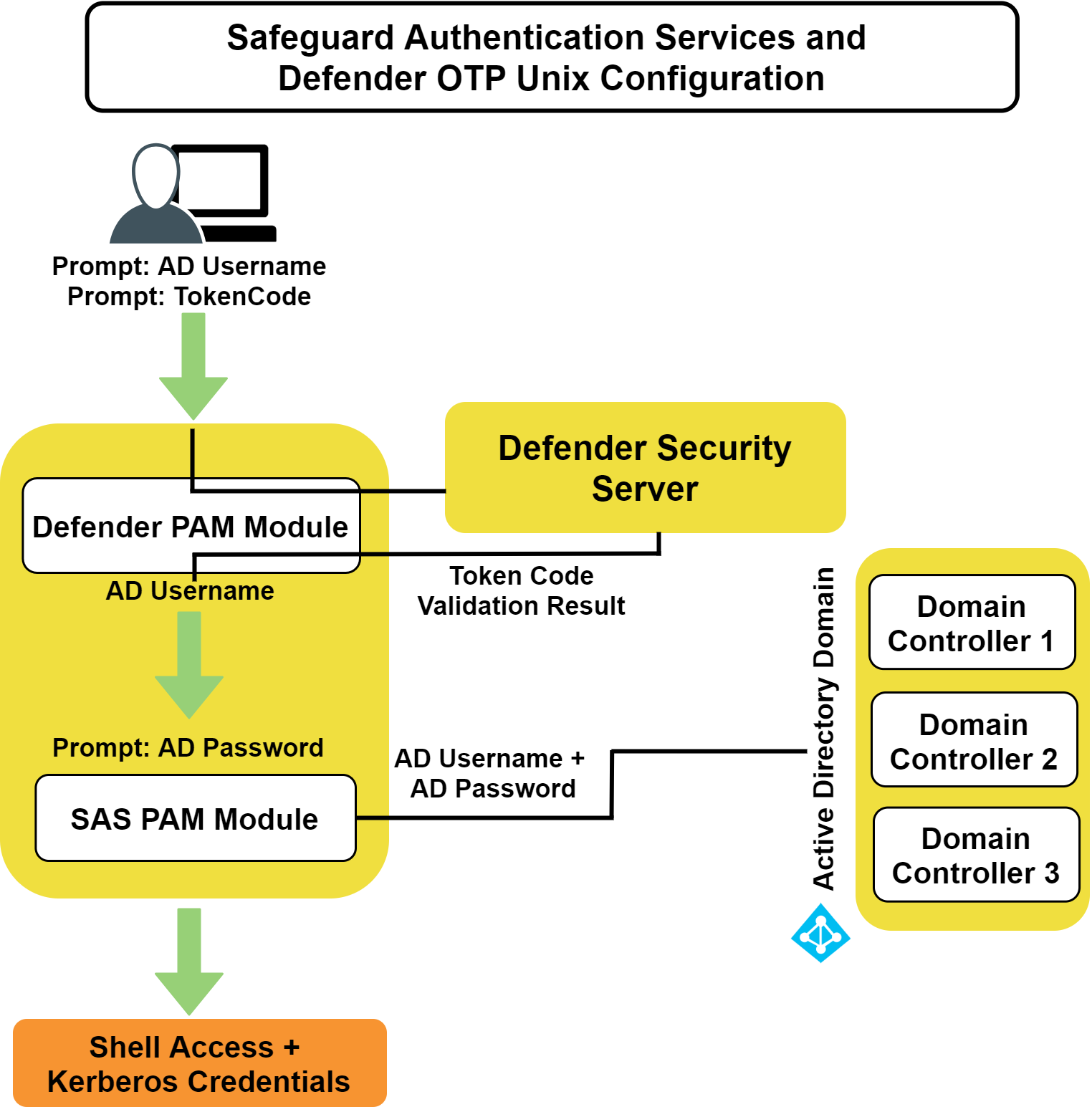
The following figure describes the flow of events that occur during a Unix or Linux login after both Safeguard Authentication Services Defender and Safeguard Authentication Services are configured according to this guide.
Figure 1: Defender Integration